266
CA Issuers - URI:http://l00192b/CertEnroll/l00192b_CA%20server.crt
CA Issuers - URI:file://\\l00192b\CertEnroll\l00192b_CA server.crt
1.3.6.1.4.1.311.20.2:
.0.I.P.S.E.C.I.n.t.e.r.m.e.d.i.a.t.e.O.f.f.l.i.n.e
Signature Algorithm: sha1WithRSAEncryption
81029589 7BFA1CBD 20023136 B068840B
(Omitted)
You can also use some other display commands to display more information about the CA certificate. For
more information about the display pki certificate ca domain command, see Security Command
Reference.
Certificate attribute access control policy configuration
example
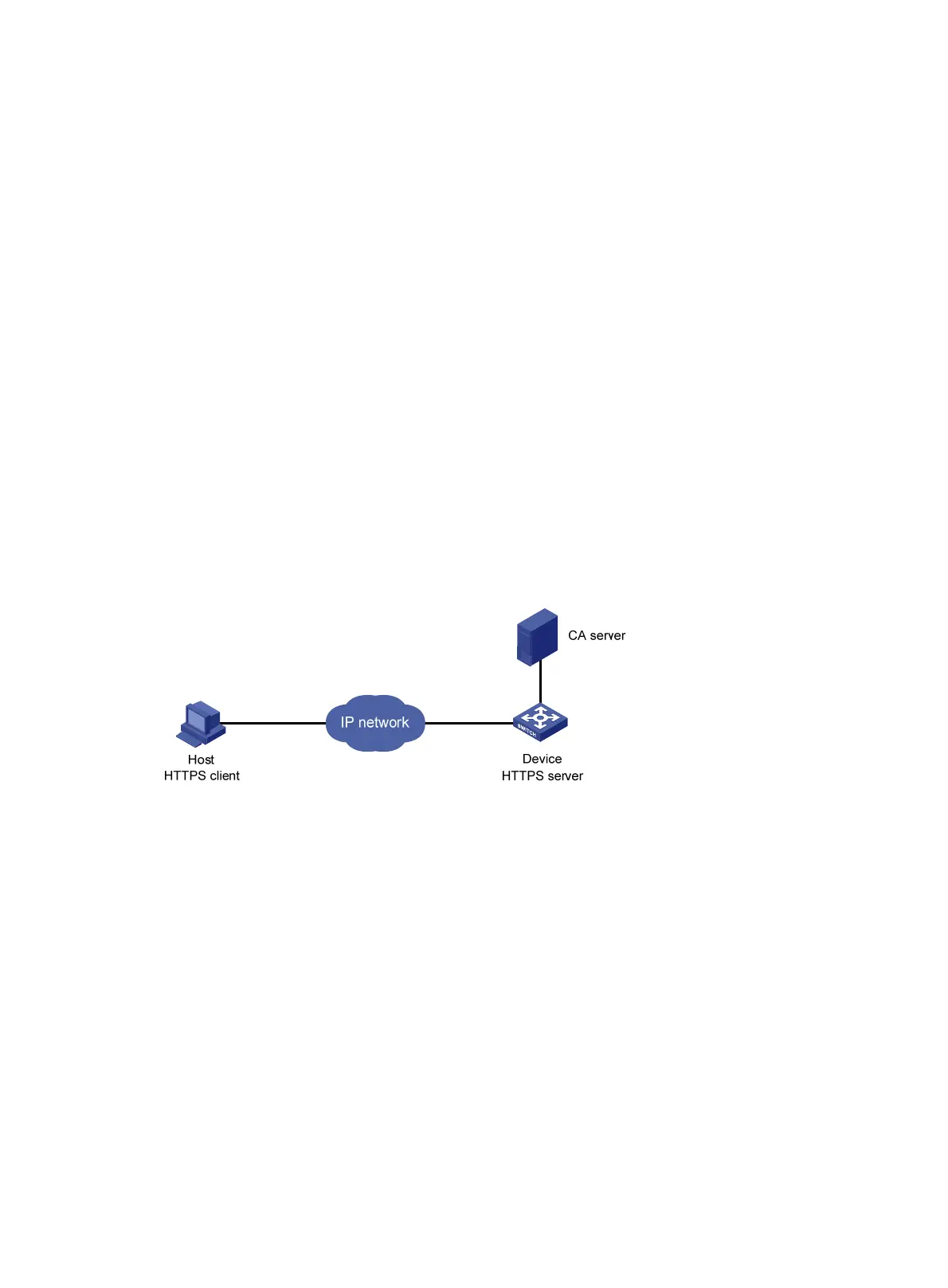
Network requirements
The client accesses the remote HTTP Secure (HTTPS) server through the HTTPS protocol.
Configure SSL to make sure that only legal clients log into the HTTPS server, and create a certificate
attribute access control policy to control access to the HTTPS server.
Figure 82 Network diagram
Configuration procedure
The configuration procedure involves SSL configuration and HTTPS configuration. For more information
about SSL configuration, see "Configuring SSL." F
or more information about HTTPS configuration, see
Fundamentals Configuration Guide.
The PKI domain to be referenced by the SSL policy must exist. For how to configure a PKI domain, see
"Configure the PKI domain:."
The configuration procedure is as follows:
1. Configure the HTTPS server:
# Configure the SSL policy for the HTTPS server to use.
<Device> system-view
[Device] ssl server-policy myssl
[Device-ssl-server-policy-myssl] pki-domain 1
[Device-ssl-server-policy-myssl] client-verify enable
[Device-ssl-server-policy-myssl] quit
2. Configure the certificate attribute group:

 Loading...
Loading...















