Configuring Security Features
939
DES-CBC3-SHA
DES-CBC3-MD5
DHE-RSA-AES128-SHA
DHE-DSS-AES128-SHA
AES128-SHA
RC2-CBC-MD5
IDEA-CBC-SHA
DHE-DSS-RC4-SHA
RC4-SHA
RC4-MD5
RC4-64-MD5
EXP1024-DHE-DSS-DES-CBC-SHA
EXP1024-DES-CBC-SHA
EDH-RSA-DES-CBC-SHA
EDH-DSS-DES-CBC-SHA
DES-CBC-SHA
DES-CBC-MD5
EXP1024-DHE-DSS-RC4-SHA
EXP1024-RC4-SHA
EXP1024-RC4-MD5
EXP-EDH-RSA-DES-CBC-SHA
EXP-EDH-DSS-DES-CBC-SHA
EXP-DES-CBC-SHA
EXP-RC2-CBC-MD5
EXP-RC4-MD5
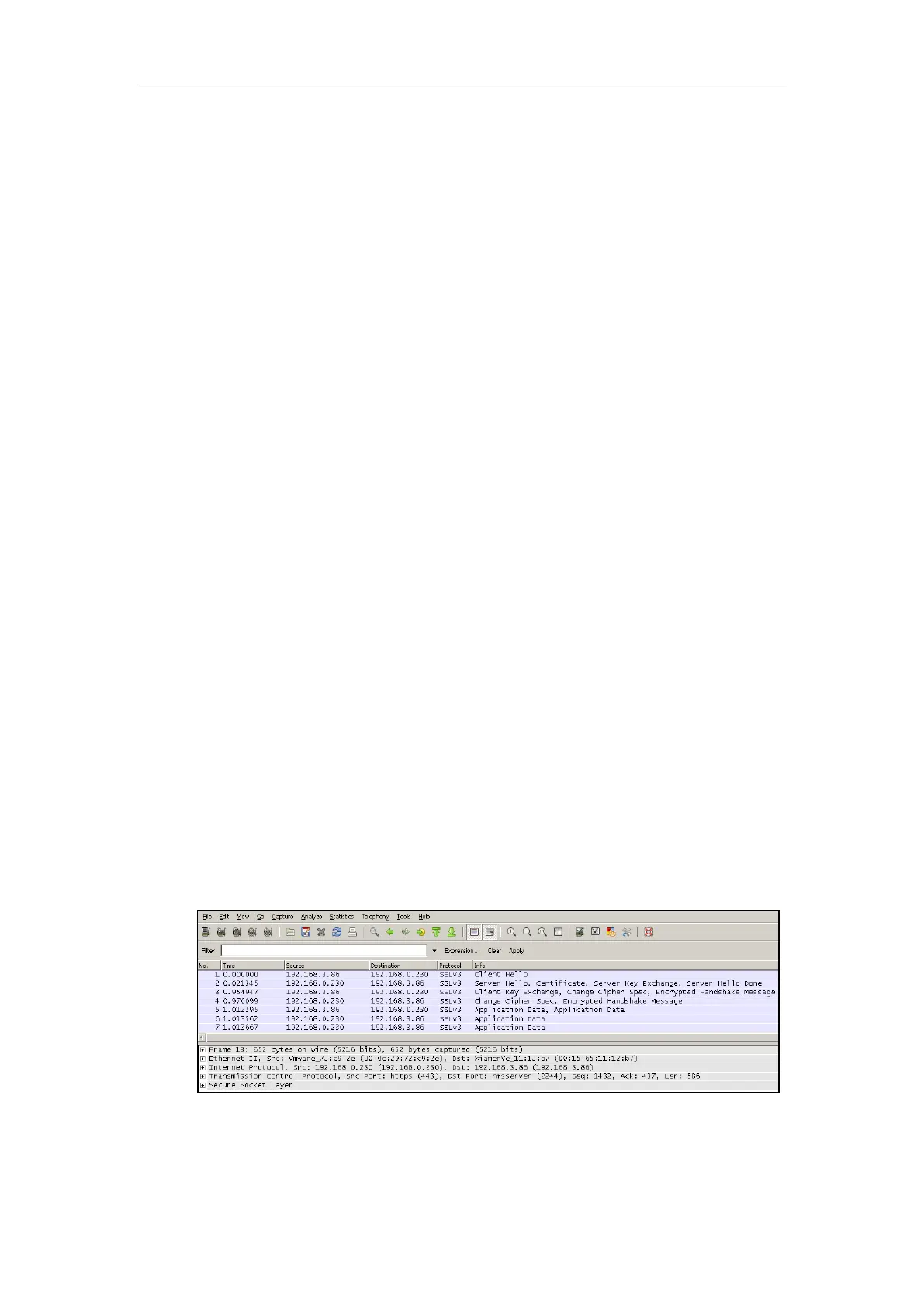
The following figure illustrates the TLS messages exchanged between the IP phone and TLS
server to establish an encrypted communication channel:
Step1: IP phone sends “Client Hello” message proposing SSL options.
Step2: Server responds with “Server Hello” message selecting the SSL options, sends its public
key information in “Server Key Exchange” message and concludes its part of the negotiation

 Loading...
Loading...
















