1-3
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Cisco Unified Presence
Information About Cisco Unified Presence
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service tcp 5060
5060
For another Cisco UP with the address 10.0.0.3, you must use a different set of PAT ports, such as 45062
or 45070:
hostname(config)# object network obj-10.0.0.3-01
hostname(config-network-object)# host 10.0.0.3
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service tcp 5061
45061
hostname(config)# object network obj-10.0.0.3-02
hostname(config-network-object)# host 10.0.0.3
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service tcp 5062
45062
hostname(config)# object network obj-10.0.0.3-03
hostname(config-network-object)# host 10.0.0.3
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service udp 5070
5070
hostname(config)# object network obj-10.0.0.2-03
hostname(config-network-object)# host 10.0.0.2
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service tcp 5070
45070
hostname(config)# object network obj-10.0.0.3-04
hostname(config-network-object)# host 10.0.0.3
hostname(config-network-object)# nat (inside,outside) static 192.0.2.1 service tcp 5060
45060
Dynamic NAT or PAT can be used for the rest of the outbound connections or the TLS handshake. The
ASA SIP inspection engine takes care of the necessary translation (fixup).
hostname(config)# object network obj-0.0.0.0-01
hostname(config-network-object)# subnet 0.0.0.0 0.0.0.0
hostname(config-network-object)# nat (inside,outside) dynamic 192.0.2.1
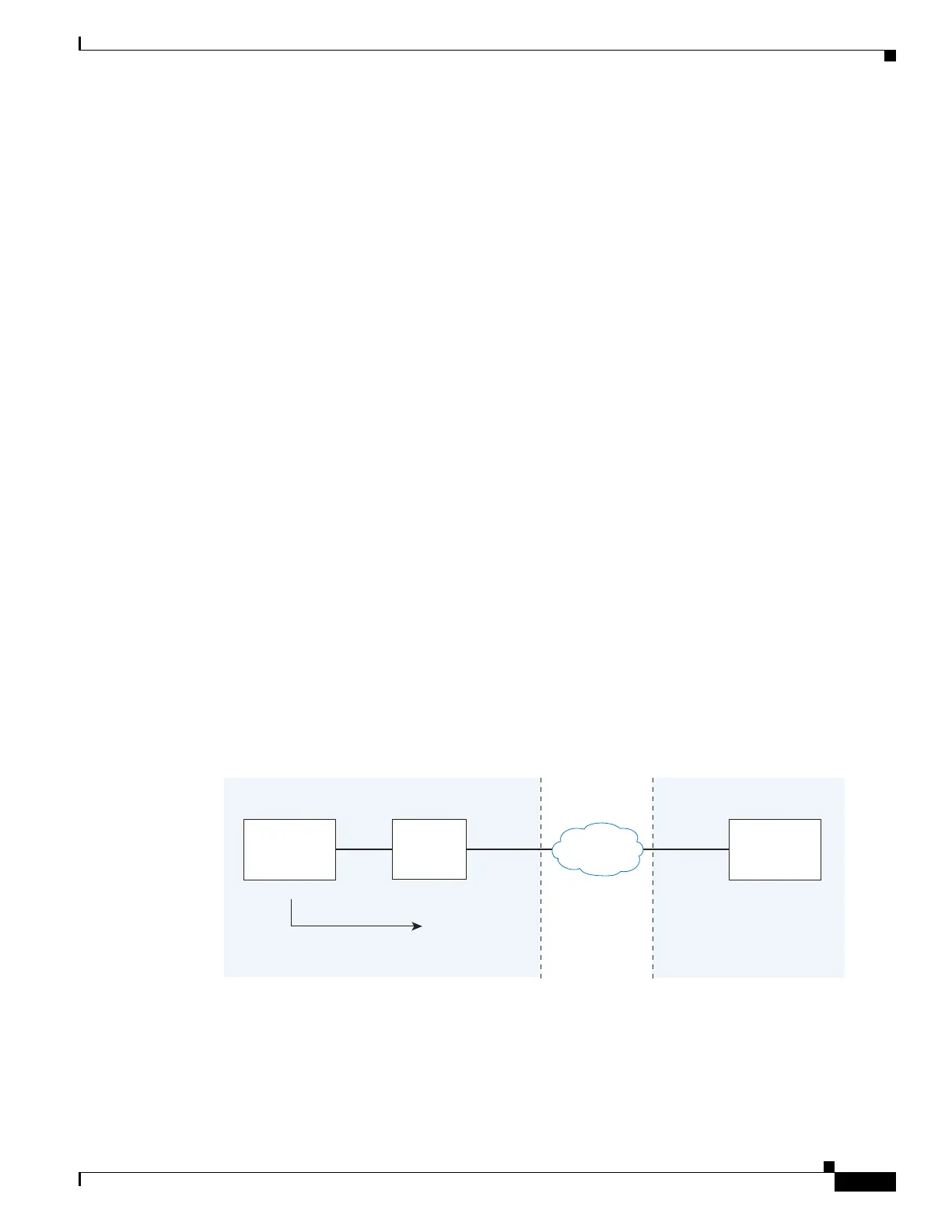
Figure 1-2 illustrates an abstracted scenario with Entity X connected to Entity Y through the presence
federation proxy on the ASA. The proxy is in the same administrative domain as Entity X. Entity Y could
have another ASA as the proxy but this is omitted for simplicity.
Figure 1-2 Abstracted Presence Federation Proxy Scenario between Two Server Entities
For the Entity X domain name to be resolved correctly when the ASA holds its credential, the ASA could
be configured to perform NAT for Entity X, and the domain name is resolved as the Entity X public
address for which the ASA provides proxy service.
For further information about configuring Cisco Unified Presence Federation for SIP Federation, see the
Integration Guide for Configuring Cisco Unified Presence for Interdomain Federation.:
271638
SIP/TLS
Internet
Entity X Entity Y
Enterprise X Enterprise Y
ASA
TLS Proxy
192.0.2.1
192.0.2.2
192.0.2.25410.0.0.2
10.0.0.1
OutsideInside
Enterprise Y Firewall omitted

 Loading...
Loading...