1-30
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring IPsec and ISAKMP
Configuring IPsec
Step 4 Apply the crypto maps collectively as a crypto map set by assigning the crypto map name they share to
the interface.
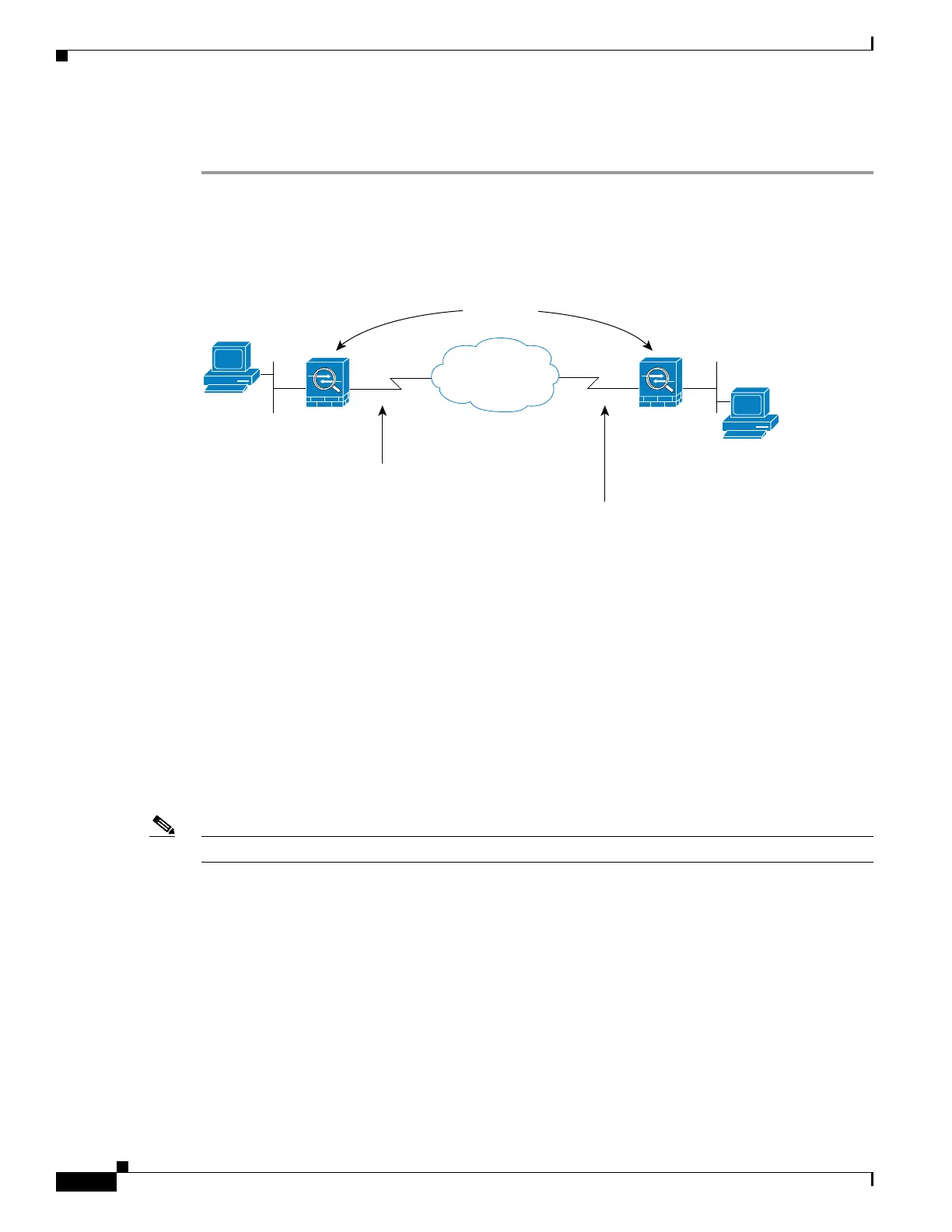
In Figure 1-4, IPsec protection applies to traffic between Host 10.0.0.1 and Host 10.2.2.2 as the data
exits the outside interface on Security Appliance A toward Host 10.2.2.2.
Figure 1-4 How Crypto Access Lists Apply to IPsec
Security Appliance A evaluates traffic from Host 10.0.0.1 to Host 10.2.2.2, as follows:
• source = host 10.0.0.1
• dest = host 10.2.2.2
Security Appliance A also evaluates traffic from Host 10.2.2.2 to Host 10.0.0.1, as follows:
• source = host 10.2.2.2
• dest = host 10.0.0.1
The first permit statement that matches the packet under evaluation determines the scope of the
IPsec SA.
Note If you delete the only element in an access list, the ASA also removes the associated crypto map.
If you modify an access list currently referenced by one or more crypto maps, use the crypto map
interface command to reinitialize the run-time SA database. See the crypto map command for more
information.
We recommend that for every crypto access list specified for a static crypto map that you define at the
local peer, you define a “mirror image” crypto access list at the remote peer. The crypto maps should
also support common transforms and refer to the other system as a peer. This ensures correct processing
of IPsec by both peers.
IPSec peers
92616
Internet
outside outside
Security
Appliance
Firewall A
Security
Appliance
Firewall B
Host
10.0.0.1
Host
10.2.2.2
IPSec Access List at "outside" interface:
access-list 101 permit ip host 10.0.0.1 host 10.2.2.2
IPSec Access List at "outside" interface:
access-list 111 permit ip host 10.2.2.2 host 10.0.0.1
Traffic exchanged between hosts 10.0.0.1 and 10.2.2.2 is protected between
Security Appliance Firewall A "outside" and Security Appliance Firewall B "outside"

 Loading...
Loading...