Protection from unauthorized access
94
6.6
Access Control Lists (ACL)
Basic - L3P
Release
3.1
06/07
6.6.3 Configuring IP ACLs
Example: Extended ACL
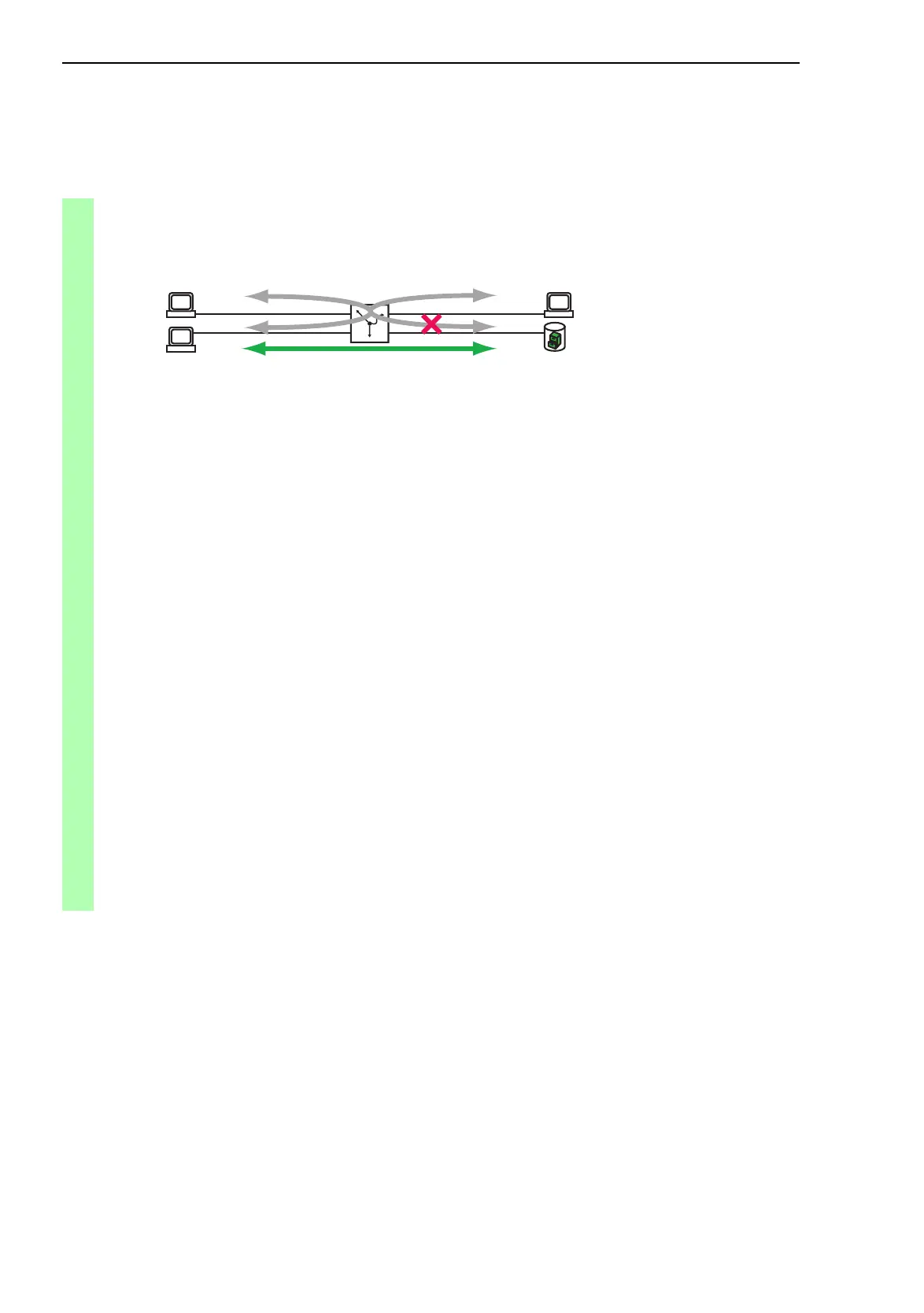
B and C are not allowed to communicate with A.
enable
configure
Switch to the privileged EXEC mode.
Switch to the configuration mode.
access-list 100 permit ip
10.0.1.11 0.0.0.0
10.0.1.158 0.0.0.0
access-list 100 permit any
any
Create the extended ACL 100 with the first rule.
This denies data traffic from the IP source address
10.0.1.11 to the IP destination address 10.0.1.158.
Add to ACL 100 a further rule. This permits data
traffic from any IP source address to any IP desti
-
nation address.
access-list 110 permit ip
10.0.1.11 0.0.0.0
10.0.1.158 0.0.0.0
access-list 100 permit any
any
Create the extended ACL 110 with the first rule.
This denies data traffic from the IP source address
10.0.1.13 to the IP destination address 10.0.1.158.
Add to ACL 110 a further rule. This permits data
traffic from any IP source address to any IP desti
-
nation address.
exit
show ip access-lists 100
Switch to the privileged EXEC mode.
Display the rules of ACL 100.
CB
DA
IP: 10.0.1.13/24
IP: 10.0.1.158/24
IP: 10.0.1.11/24
IP: 10.0.1.159/24
Interface: 3.1
Interface: 2.1Interface: 1.3
Interface: 2.3
 Loading...
Loading...