3 Web-based Management
3.6.6.3 Group Information
This page displays the DHCP Snooping group information. Take the configuration in the
following figure as an example for illustration. A device with the MAC 6c-f0-49-82-be-cf of
VLAN 1, connected with the Ethernet 0/1 port, successfully got an IP address
192.168.104.250 from a DHCP server, and the lease time is 259200 seconds.
3.6.7 DHCP Limit
To prevent attacks from unauthorized DHCP servers, the switch CPU for validity checking will
process DHCP packets; but if attackers generate a large number of DHCP packets, the
switch CPU will be under extremely heavy load. As a result, the switch cannot work normally
and even goes down.
IPC-1840 switches support DHCP packet rate limit on a port and shut down the port under
attack to prevent hazardous impact on the device CPU.
After DHCP packet rate limit is enabled on an Ethernet port, the switch counts the number of
DHCP packets received on this port per second. If the number of DHCP packets received per
second exceeds the specified value, packets are passing the port at an over-high rate, which
implies an attack to the port. In this case, the switch shuts down this port so that it cannot
receive any packet, thus protect the switch from attacks.
In addition, the switch supports port state auto-recovery. After a port is shut down due to
over-high packet rate, it resumes automatically after a configurable period of time.
There are two tab pages to configure the related rate parameters of DHCP Limit.
3.6.7.1 Port Configuration
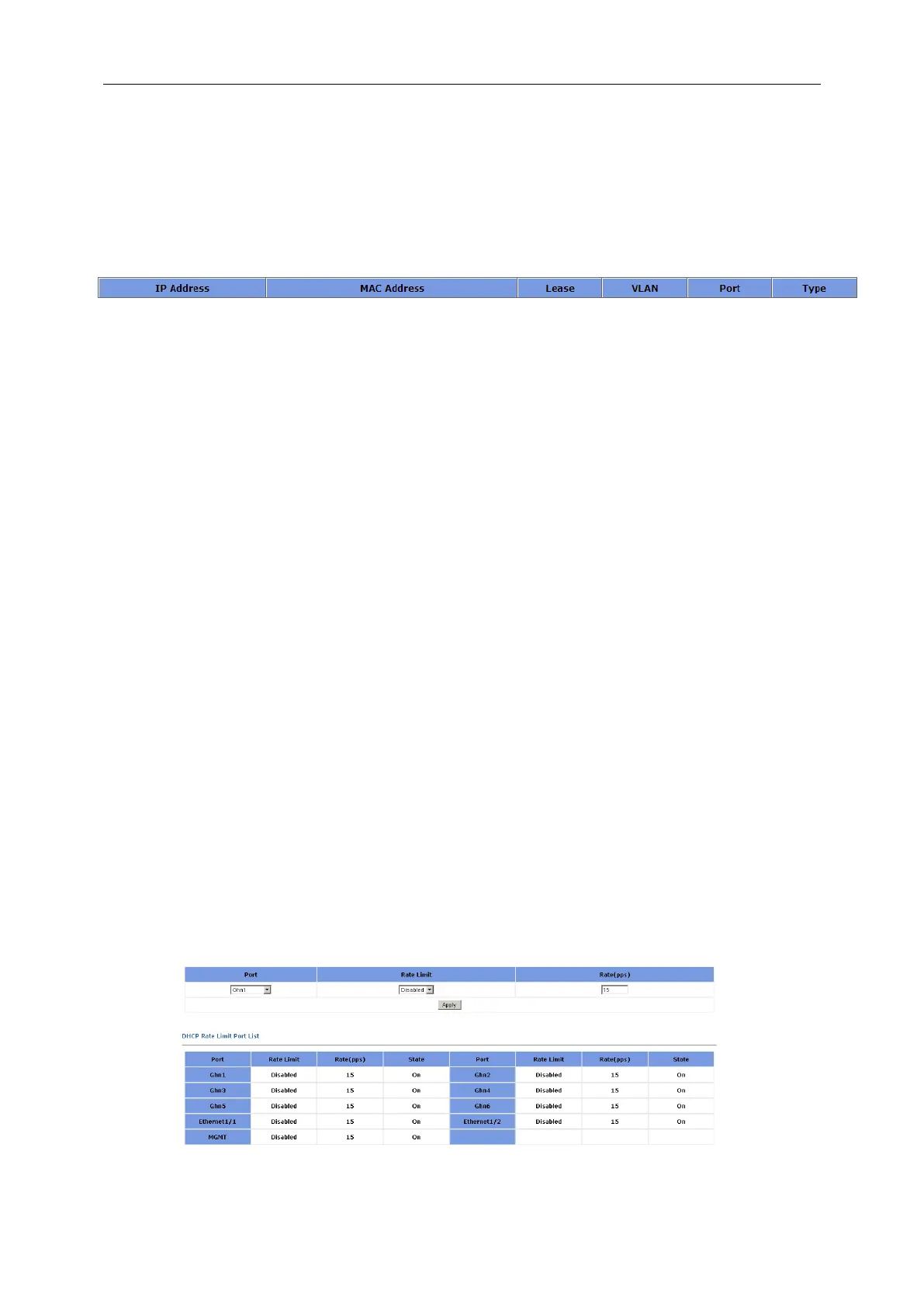
This page sets the DHCP Rate Limit for a specified Ethernet Port.
Rate Limit Enable /disable the function of DHCP Rate limit for a specified port
Rate It is in the range of 10 to 150, the default value is 15 pps.
State Port state, when it over speeds, it will be shown as “OFF”.
The lower part of this page lists all the DHCP Rate Limit ports.
 Loading...
Loading...