CONFIGURATION
31
1.15. IPSec tunnel configuration
IPsec tunnel configuration can be called up by option IPsec item in the menu. IPsec
tunnel allows protected (encrypted) connection of two networks LAN to the one which looks
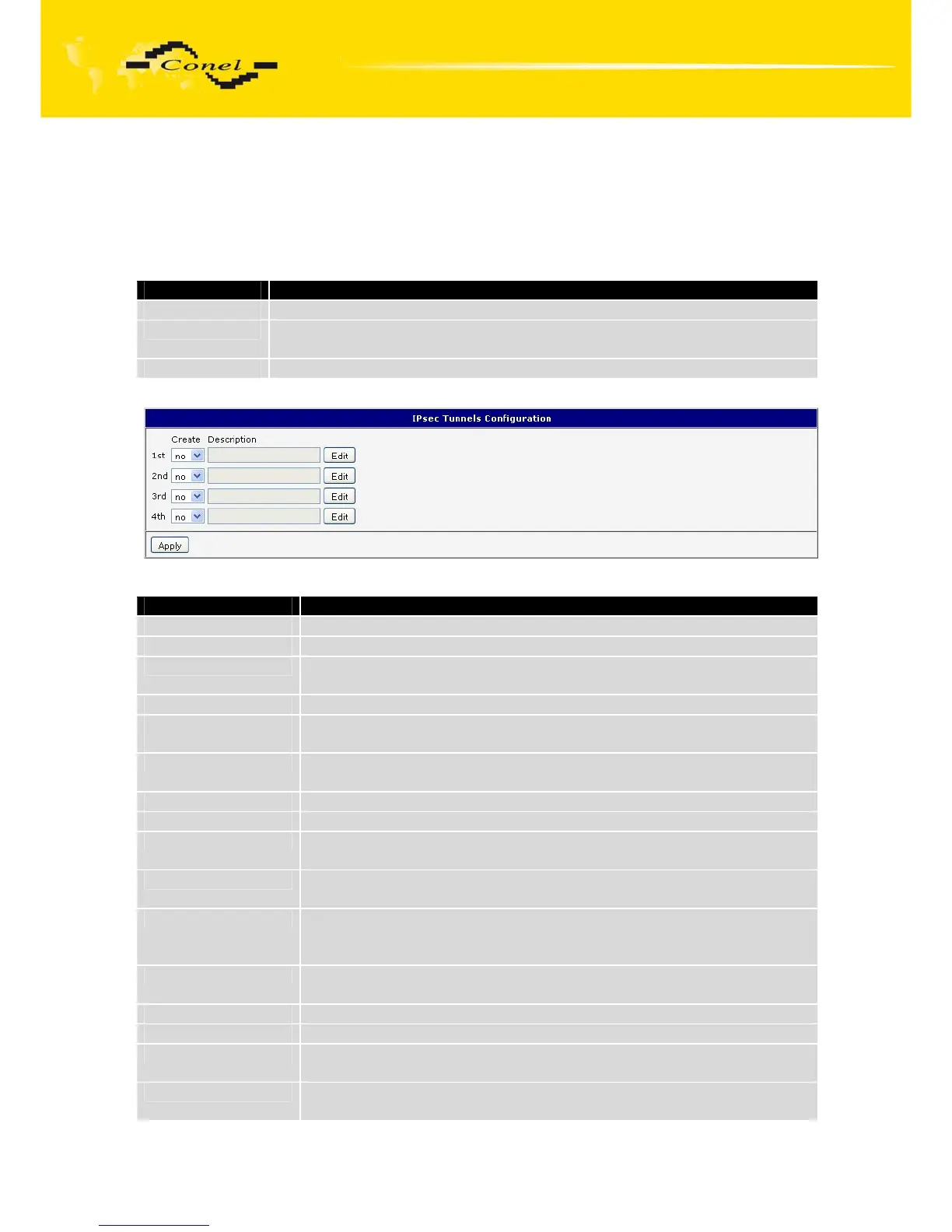
like one homogenous. In the IPsec Tunnels Configuration window are four rows, each row
for one configured one IPSec tunnel.
Item Description
Create This item enables the individual tunnels.
Description This item displays the name of the tunnel specified in the configuration
of the tunnel.
Edit Configuration IPsec tunnel.
Table 29: Overview IPsec tunnels
Fig. 32: IPsec tunnels configuration
Item Description
Description Description of tunnel.
Remote IP Address IP address of opposite side tunnel. Can be used domain main.
Remote ID Identification of opposite side tunnel. Parameters ID contain two parts:
hostname and domain-name.
Remote Subnet Address nets behind off - side tunnel
Remote Subnet
Mask
Subnet mask behind off - side tunnel
Local ID Identification of local side. Parameters ID contain two parts: hostname
and domain-name.
Local Subnet Local subnet address
Local subnet mask Local subnet mask
Key Lifetime Lifetime key data part of tunnel. The minimum value of this parameter
is 60s. The maximum value is 86400 s.
IKE Lifetime Lifetime key service part of tunnel. The minimum value of this
parameter is 60s. The maximum value is 86400 s.
Rekey Margin Specifies how long before connection expiry should attempt
to negotiate a replacement begin. The maximum value must be less
than half the parameters IKE and Key Lifetime.
Rekey Fuzz Specifies the maximum percentage by which should be randomly
increased to randomize re-keying intervals
DPD Delay Defines time after which is made IPsec tunnel verification
DPD Timeout By parameter DPD Timeout is set timeout of the answer
NAT traversal If address translation between two end points of the IPsec tunnel is
used, it needs to allow NAT Traversal
Aggressive mode If this parameter is enabled, establishing of IPsec tunnel will be faster,
but encryption will set permanently on 3DES-MD5.
 Loading...
Loading...