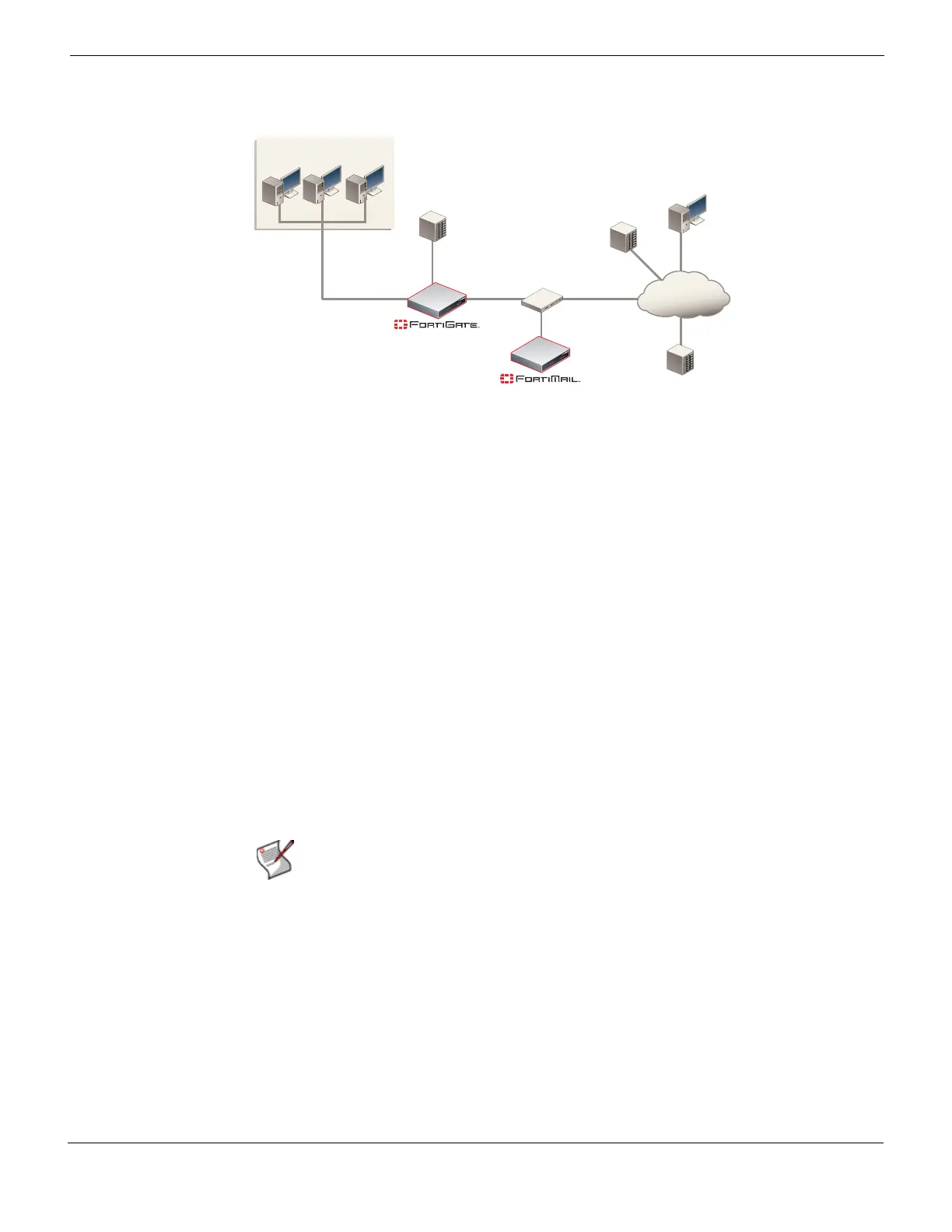
Gateway mode deployment Example 2: FortiMail unit in front of a firewall
FortiMail™ Secure Messaging Platform Version 4.0 Patch 1 Install Guide
Revision 2 105
http://docs.fortinet.com/ • Feedback
Figure 43: FortiMail unit in front of a NAT device
The FortiMail unit has also been configured with an access control rule that allows local
and remote email users to send email to unprotected domains if they first authenticate:
To deploy the FortiMail unit in front of a NAT device such as a firewall or router, you must
complete the following:
• Configuring the firewall
• Configuring the MUAs
• Testing the installation
Configuring the firewall
With the FortiMail unit in front of a FortiGate unit, the internal network located behind the
FortiGate unit, and the protected email server located on the DMZ, you must configure
firewall policies to allow traffic:
• between the internal network and the FortiMail unit
• between the internal network and protected email server
• between the protected email server and the FortiMail unit
• between the protected email server and the Internet
To create the required policies, complete the following:
Sender Pattern *@example.com
Recipient Pattern *
Sender IP/Netmask 0.0.0.0/0
Reverse DNS
Pattern
*
Authentication
Status
authenticated
TLS < none >
Action RELAY
External
Em ail Server
Local Em ail Users
Rem ote Em ail Users
DNS Server
Internet
Sw itch
Internal Em ail Server
192.168.1.10
wan1
10.10.10.1
port1
10.10.10.5
Protected Dom ain:
@exam ple.com
Em ail Dom ain:
@exam ple.com
exam ple.co m IN MX 10 fortimail.exam ple.com
fortimail IN A 10.10.10.5
internal
172.16.1.1
(v irtual IP:
172.16.1.2)
dm z
192.168.1.1
Note: This example assumes you have already completed the Quick Start Wizard and
configured records on the DNS server for each protected domain. For details, see “Quick
Start Wizard” on page 77 and “Configuring DNS records” on page 95.

 Loading...
Loading...











