Communications services
3.6 Secure Communication
Communication
42 Function Manual, 11/2019, A5E03735815-AH
Verifying a signature:
1. The authenticator of the "MyCert" certificate obtains the certificate of the issuer and thus
the public key.
2. A new hash value is formed from the certificate data with the same hash algorithm that
was used for signing (for example SHA-1).
3. This hash value is then compared with the hash value that is determined by means of the
public key of the certificate issuer and the signature algorithm for checking the signature.
4. If the signature check produces a positive result, both the identity of the certificate subject
as well as the integrity, meaning authenticity and genuineness, of the certificate content
are proven. Anyone who has the public key, i.e. the certificate from the certificate
authority, can check the signature and thus recognize that the certificate was actually
signed by the certificate authority.
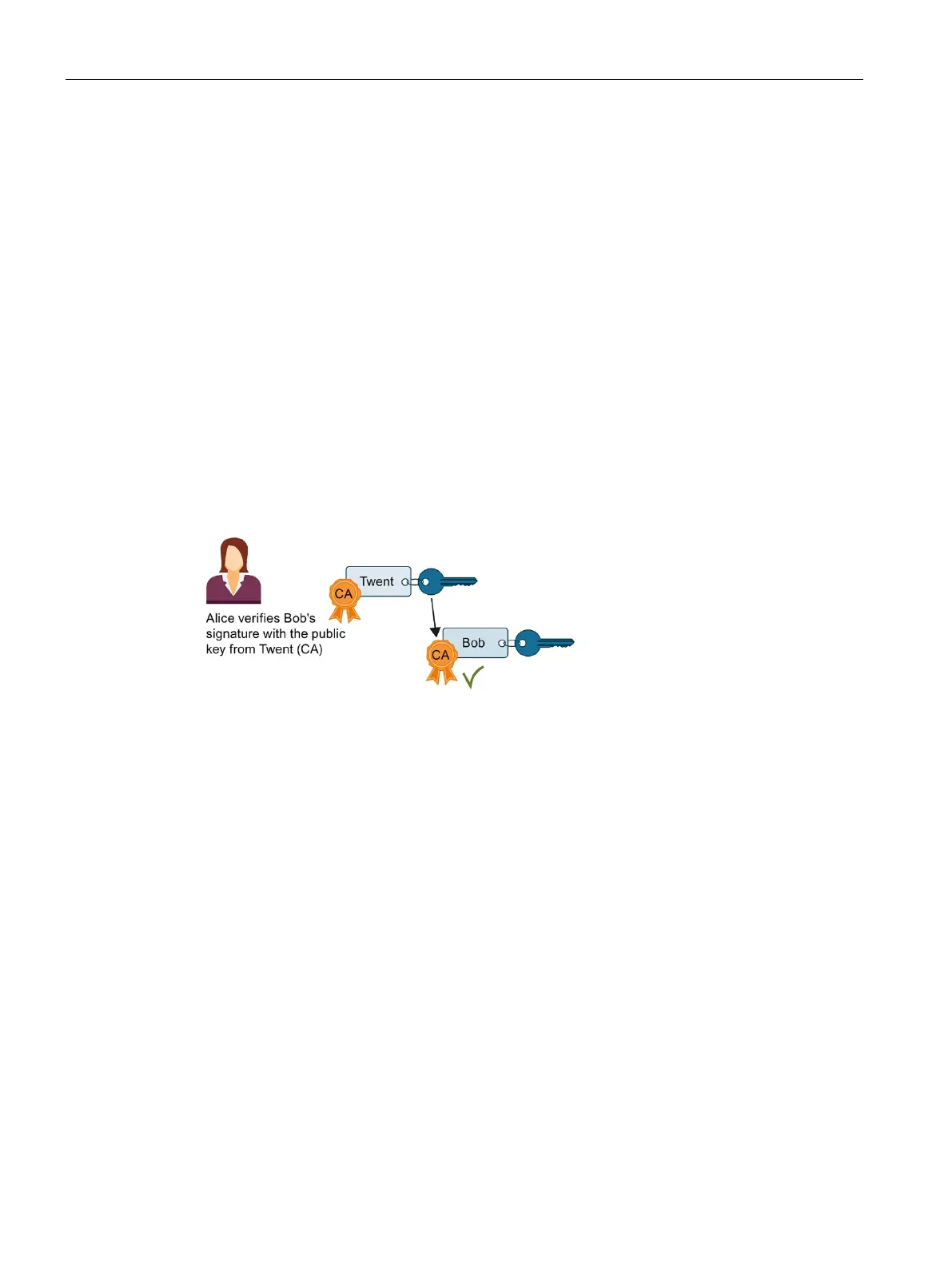
The figure below shows how Alice uses the public key in the certificate from Twent (who
represents the certificate authority, CA) to verify the signature on Bob's public key. All that is
required for verification is therefore the availability of the certificate from the certificate
authority at the moment of checking. The validation itself is executed automatically in the
TLS session.
Figure 3-10 Verification of a certificate with the public key of the certificate of a certificate authority
Signing messages
The method described above for signing and verifying also uses the TLS session for signing
and verifying messages.
If a hash value is generated by a message and this hash value is signed with the private key
of the sender and attached to the original message, the recipient of the message is able to
check the integrity of the message. The recipient decrypts the hash value with the public key
of the sender, puts together the hash value from the message received and compares the
two values. If the values are not the same, the message has been tampered with on the way.

 Loading...
Loading...





















