Yealink Skype for Business HD IP Phones Administrator Guide
vi
Conventions Used in Yealink Documentations
Yealink documentations contain a few typographic conventions.
You need to know the following basic typographic conventions to distinguish types of in-text
information:
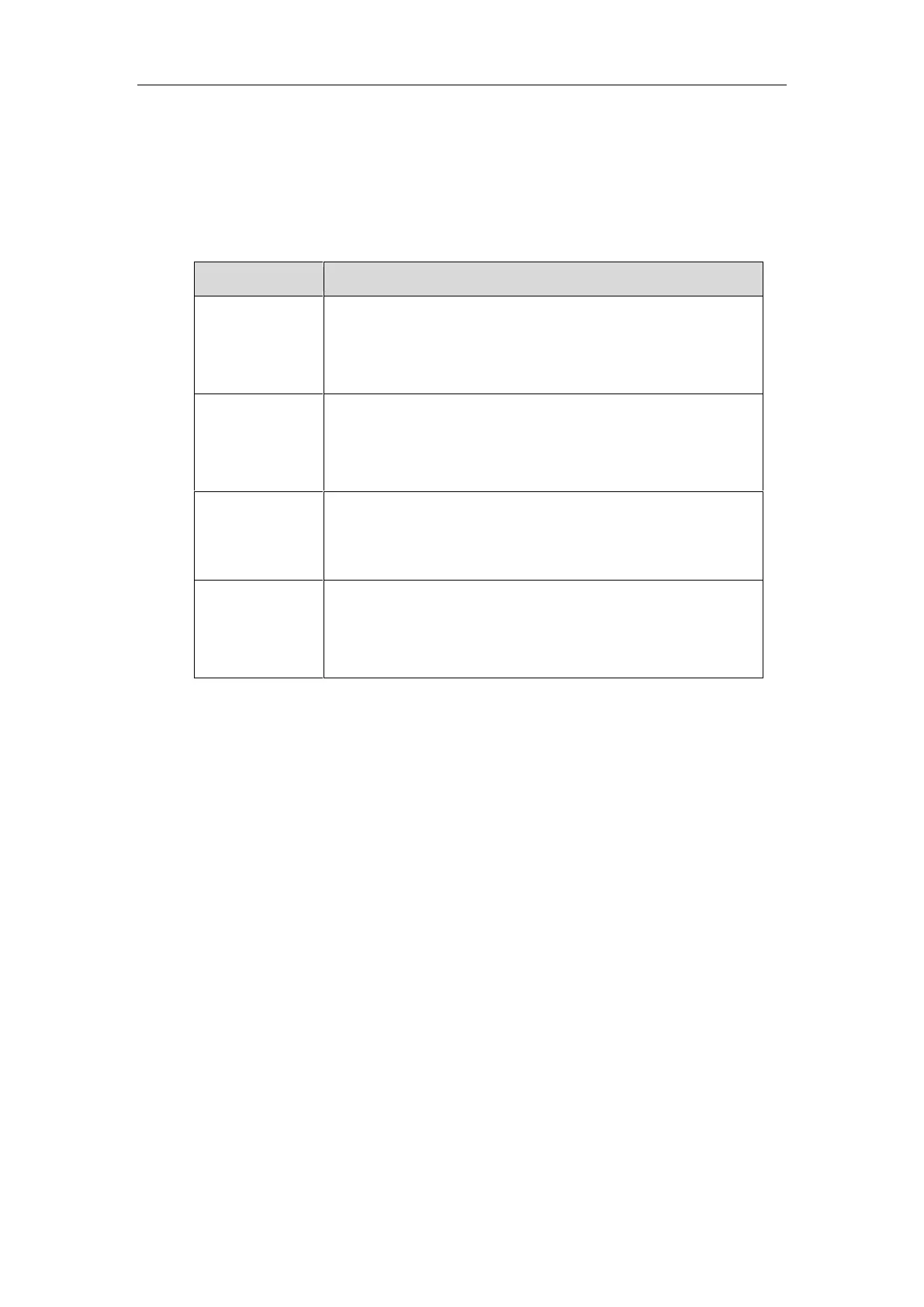
Highlights the web/phone user interface items such as menus, menu
selections, soft keys, or directory names when they are involved in a
procedure or user action (e.g., Click on Security->License).
Also used to emphasize text (e.g., Configuration File).
Used to show the format of examples (e.g.,
http(s)://[IPv6 address]
),
or to show the title of a section in the reference documentations
available on the Yealink Technical Support Website (e.g.,
Triggering
the Skype for Business phone to Perform the Auto Provisioning
).
Used for cross references to other sections within this
documentation (e.g., refer to Troubleshooting).
Used for hyperlinks to Yealink resources outside of this
documentation such as the Yealink documentations (e.g.,
Yealink_Skype_for_Business_HD_IP_Phones_Auto_Provisioning_Guide
).
In This Guide
The information detailed in this guide is applicable to the Skype for Business phones running
firmware version 8 or higher. The firmware format is like x.x.x.x.rom. The second x from left must
be greater than or equal to 8 (e.g., the firmware version of T46G Skype for Business phone:
28.8.0.50.rom). This administrator guide includes the following chapters:
Chapter 1, “Product Overview” describes the SIP components and Skype for Business
phones.
Chapter 2, “Getting Started” describes how to install and connect Skype for Business
phones, configuration methods and resource files.
Chapter 3, “Configuring Basic Features” describes how to configure the basic features on
Skype for Business phones.
Chapter 4, “Configuring Advanced Features” describes how to configure the advanced
features on Skype for Business phones.
Chapter 5, “Configuring Audio Features” describes how to configure the audio features on
Skype for Business phones.
Chapter 6, “Configuring Security Features” describes how to configure the security features

 Loading...
Loading...






