Manual Datafox Evo 4.3 Page 65 Date: 27.12.2017 V 04.03.09.XX
Holiday ControlIt is now possible for ZK-II to consider holidays at switching the relay. In order to
achieve compatibility with older versions, the function Consider Holidays for the Time Control of Re-
lays has to be activated at the setup page Access Control 2. In the column Group, you specify the
Action ID of the switched relay output instead of a Group ID. Thus, it is not necessary to alter the
table structure of the holiday list. The column RefTime provides the time model applicable that day.
A minus sign must be inserted in front of the Action ID in order that the MasterIV terminal can differ-
entiate between Action ID and Group ID. As a result, these Action IDs must be three-digit numbers.
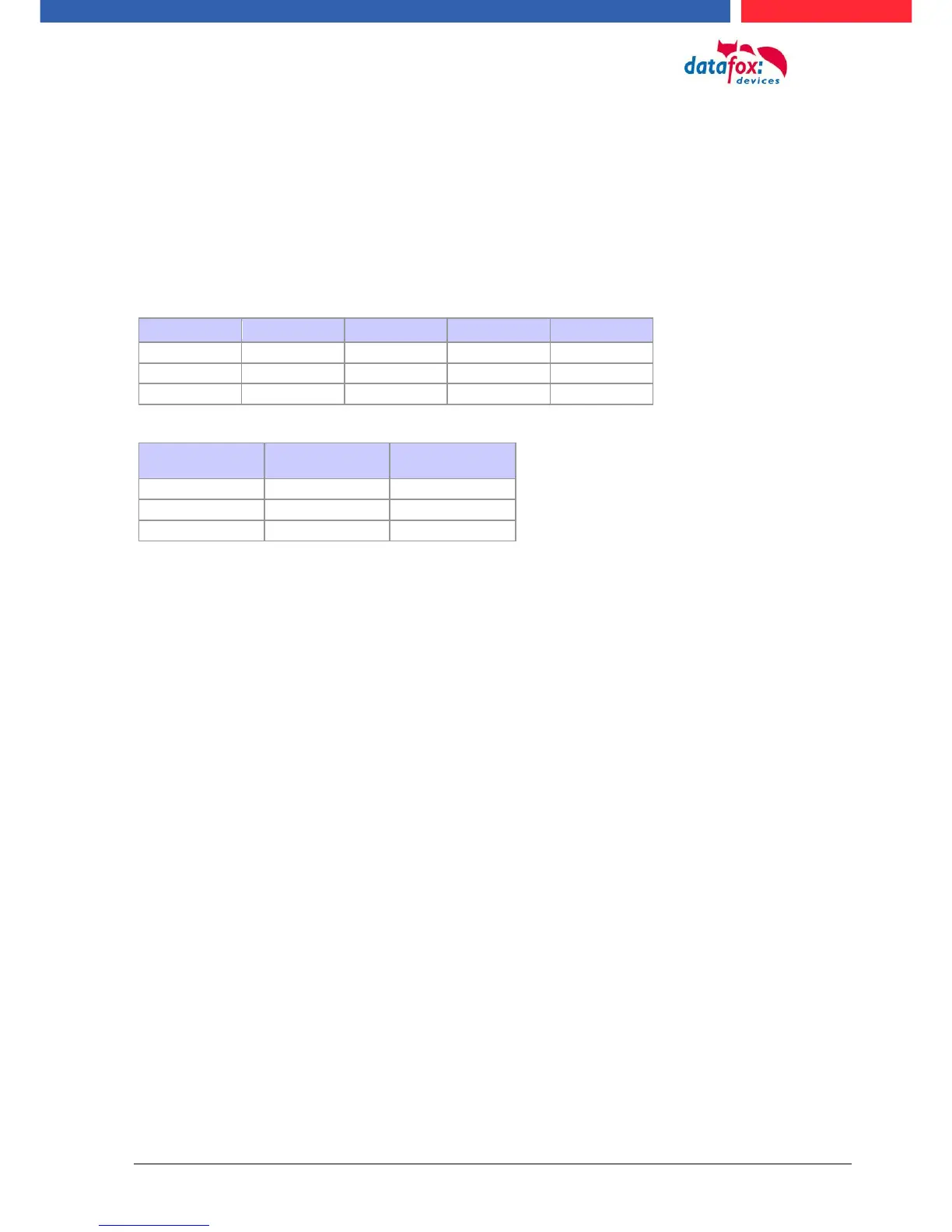
Example:
Action
In the action list above, the door module with the ID 12 was assigned the time model 2 which
switches port 1 of the module. If separate holiday control has been activated in the setup, time
model 2 is not applied to the relay output at May 1, 2012, but time model 5.
Extended Parameterization ZK-II
The value range of the parameter 'ActiveGeneral' has been extended by the value 8. Additionally to
the general permission (value 9), a PIN request is executed - if defined so for the user and activated
for the reader. Furthermore, at both configurations of the ID cards with the ActiveGeneral value 8
and 9, the validity period of the ID card is checked.
For ZK-II the operation modes online, offline or online/offline after time-out are available. In online
mode, configuration lists stored in the device are not considered. A data record is read from the
server, analyzed and an action triggered. In offline mode, the configuration lists of the terminal are
used to grant or deny access to a person. Online / offline after time-out is a combination. If the serv-
er is unavailable, the terminal can decide on basis of its lists whether to grant access to a person or
not.
 Loading...
Loading...