5.7. connection and wirering of the accesscontrol
5.7.1. Configuration of Access control adn stuckture
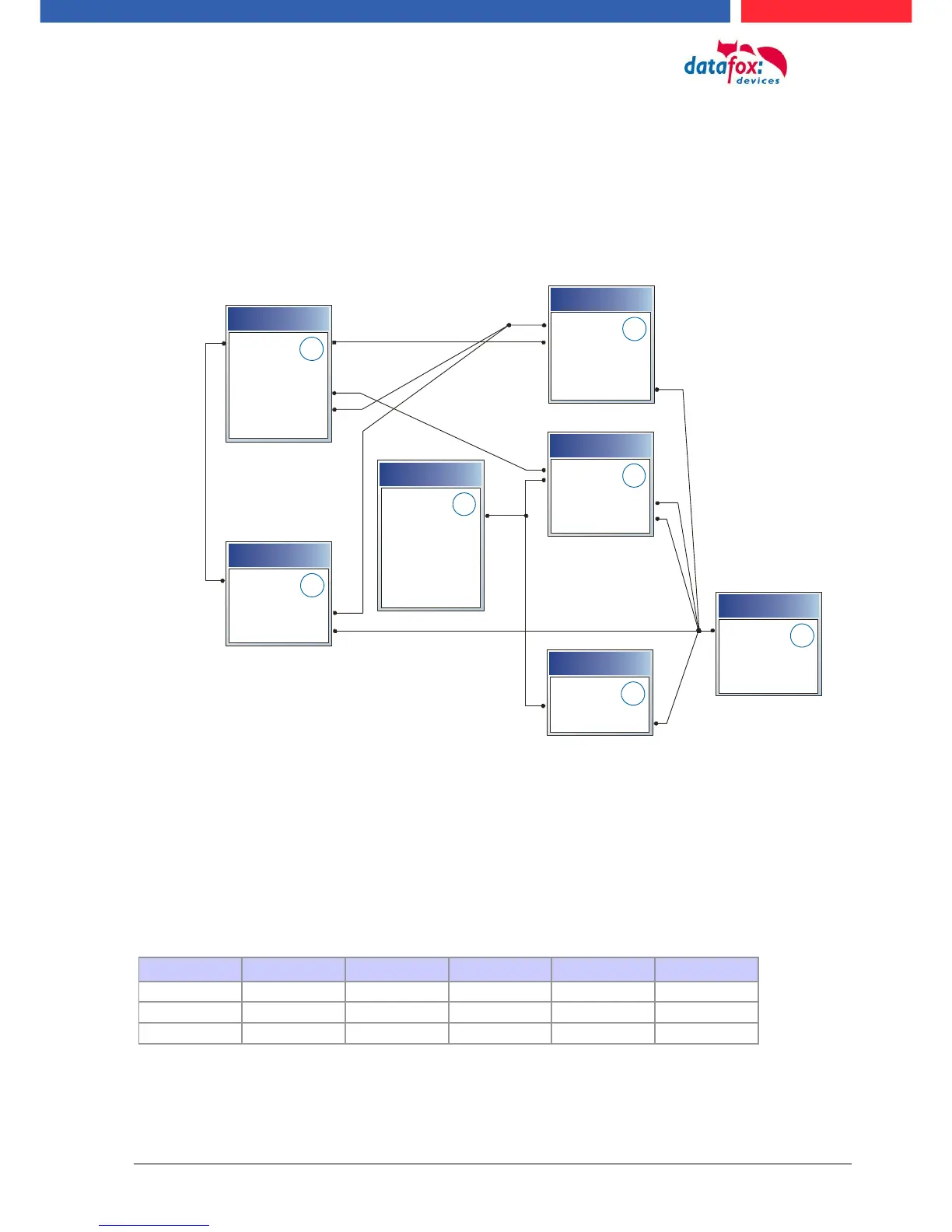
The basis of the access control II are tables. They store all information about the hardware configu-
ration of the access control system, access right of the employees, periods of time (activation,
blocking times, holidays,...). The tables are connected as follows:
The tables are created as text files. For an easier administration you can add comments within the
files.
When adding comments, you have to notice that in a comment line no field values can be given and
that the comment line has to start with a semicolon.
The table Reader.txt might look like this:
 Loading...
Loading...