M3 Vital Signs Monitor User Manual Intended Use and Safety Guidance
- 8 -
CAUTION
3 Ensure that the data are deleted after the patient is discharged. (Refer to Section 4.12
Data Store).
4 Ensure that the monitor is connected only to the device authorized/approved by
EDAN. Users should operate all EDAN deployed and supported monitors within
EDAN authorized specifications, including EDAN approved software, software
configuration, security configuration, etc.
5 Protect all the passwords to prevent unauthorized changes.
6 Anti-virus measures such as USB device virus scanning should be carried out prior to
using USB flash drive.
7 Firewalls and/or other security devices should be in place between the medical
system and any externally accessible systems. It’s recommended to use Windows
defender firewall or any other firewall that can defend against Dos and DDos attacks,
and keep it up to date.
8 When the monitor is returned for maintenance, disposed of, or removed from the
medical institution for other reasons, it is necessary to ensure that all patient data are
removed from the monitor. (Refer to Section 4.12 Data Store).
9 Please protect the privacy for the information and the data displayed on the screen,
and for the information and the data stored in the monitor.
10 When building the networking environment: 1) If a wireless router is used, please turn
on the MAC address filtering function of the wireless router and add the MAC address
of the monitor to the rule list. The wireless router only allows devices in the rule list to
access the wireless network. 2) It is suggested to build a VLAN, assign the LAN ports
where the approved switch port, monitor and MFM-CMS are into the same VLAN, and
isolate it from other VLANs.
NOTE:
Log files generated by the monitor are used for system troubleshooting and do not
contain protected medical data.
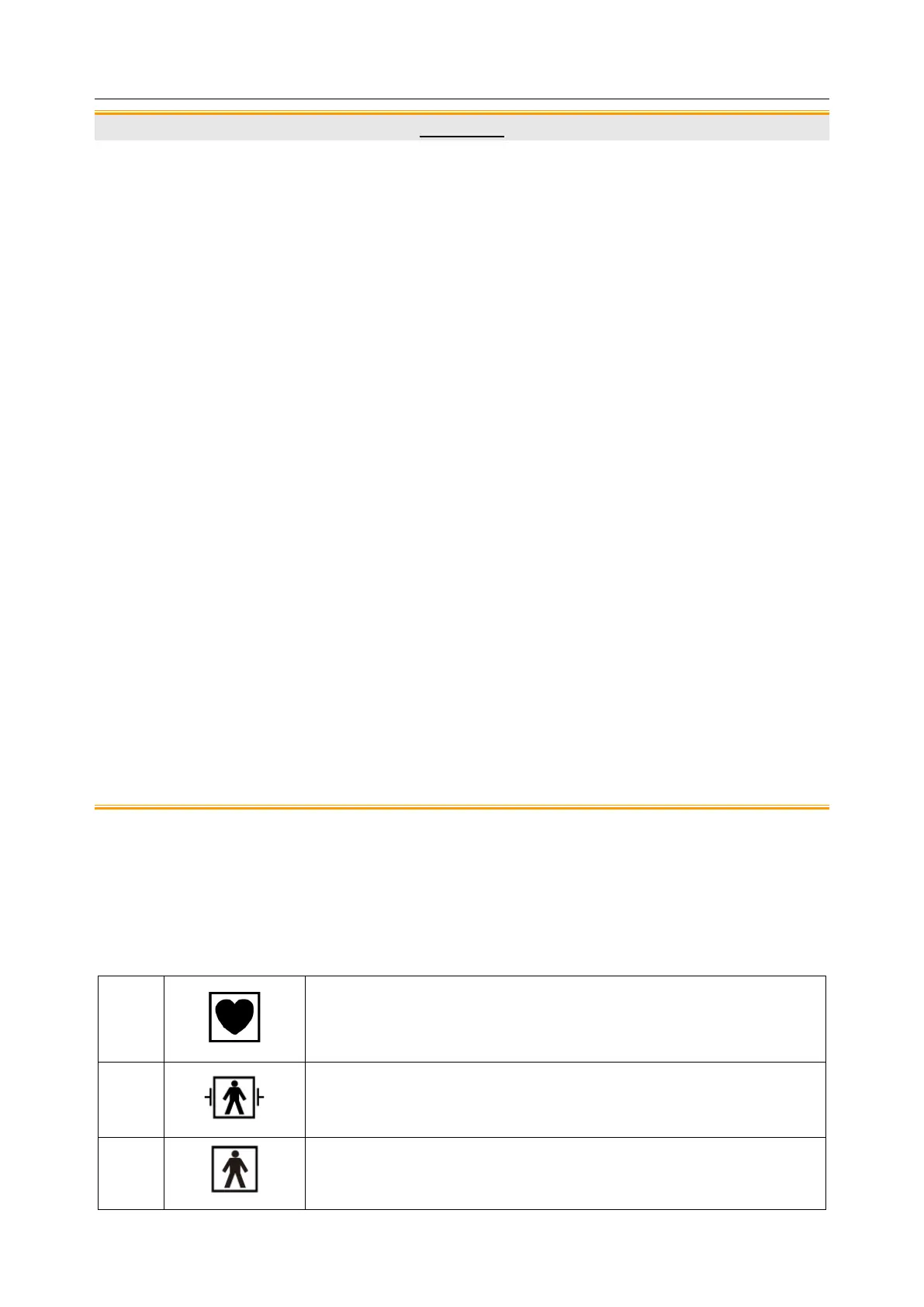
1.2.8 Explanation of Symbols on the Monitor
DEFIBRILLATION-PROOF TYPE BF APPLIED PART
 Loading...
Loading...