Chapter 13. Disk sanitization 183
Sanitization is the process of preventing the retrieval of information from the erased media by
using normal system functions or software. The data might still be recoverable, but not
without special laboratory techniques. This level of security is typically achieved by
overwriting the physical media at least once.
Purging is the process of preventing the retrieval of information from the erased media by
using all known techniques, including specialist laboratory tools. This level of security is
achieved by securely erasing the physical media by using firmware-level tools.
As the name implies, destruction is the physical destruction of the decommissioned media.
This level of security is only required in defense or other high-security environments.
13.2.3 Technology drivers
As technology advances, upgrades, disk subsystem replacements, and data lifecycle
management require the migration of data. To ensure that the data movement does not
create a security risk by leaving data patterns behind, IBM System Storage N series offers the
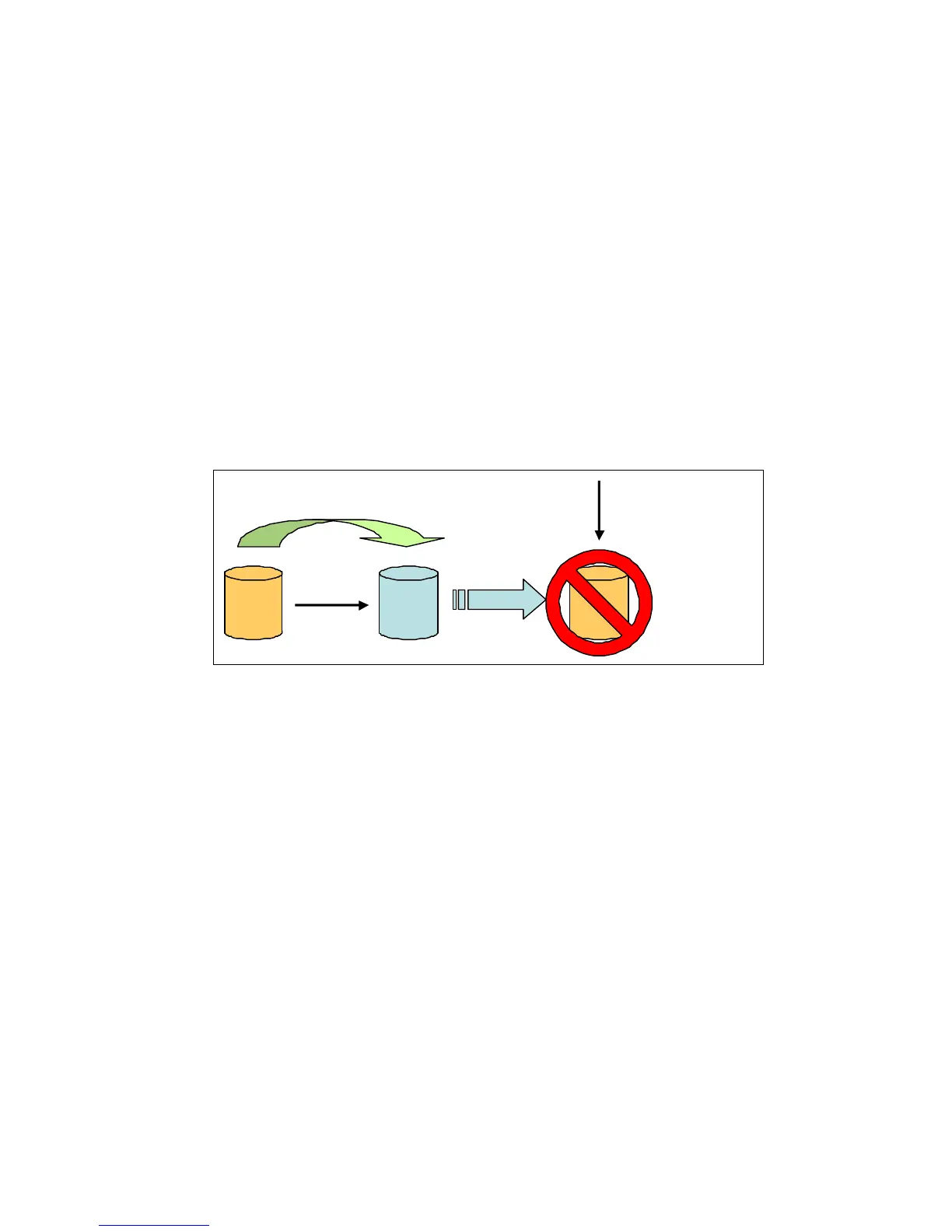
disk sanitization feature, as shown in Figure 13-1.
Figure 13-1 Disposing of disks
You might also sanitize disks if you want to help ensure that data on those disks is physically
unrecoverable. You might have disks that you intend to remove from one storage system and
want to reuse those disks in another appliance.
13.2.4 Costs and risks
All enterprises must consider the following critical factors when they are deciding on the cost
and risk of a hard disk sanitization practices:
The cost of running sanitization programs on a fleet of computers can be prohibitive. Even
in smaller organizations, the number of hard disks that must be cleansed can be
unmanageable. Most IT managers do not have the time or resources to accomplish such a
task without affecting other core business responsibilities. If you choose to destroy your
hard disks (many of which can be reused), you dispose of equipment that still has market
value.
Companies also must recognize the significant risk that is associated with breaches of
private information. When companies do not properly sanitize exiting storage devices, they
expose themselves to a myriad of public relations, legal, and business repercussions if
any confidential data is leaked. Because governments around the world continue to pass
and enforce regulations for electronic data security, IT managers must act quickly to adopt
and implement appropriate hard disk sanitization practices.
ITSO
REDB
OOKS
Write
Pattern X
Sanitization Cycle
XXXX
XXXX
XXXX
Data not
Accessible
Access to
Data

 Loading...
Loading...











