PAMSPAN501x G.SHDSL.bis EFM Gateway
-76
SYN/FIN/RST Flood
The attack exploits the way TCP-connections are established between two
computers. Attackers send unreachable source addresses in SYN packets, so your
device sends SYN/ACK packets to the unreachable address, but does not receive
any ACK packets in return. This causes a backlog of half-opened sessions. Once
the queue is full, your device ignores all incoming SYN requests which may include
legitimate traffic.
TCP packets with FIN and RST flags set also cause problems and constitute a
preliminary survey to gain information about the victim’s network.
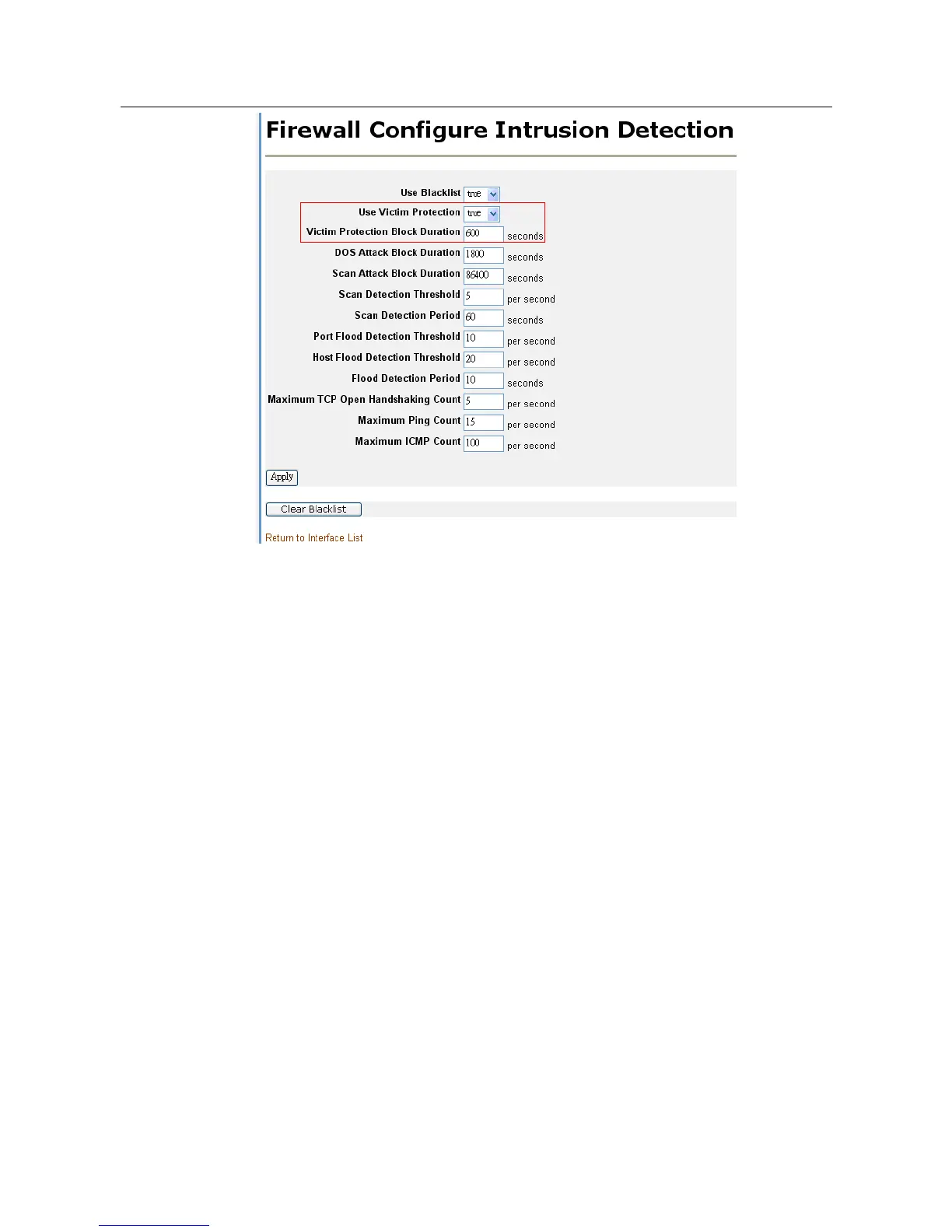
The device detects an attempted SYN flood if it received more than 20 SYN
packets per second from a single host. To modify this default threshold, enter:
security set IDS floodthreshold <max>
The device also detects an attempted SYN flood if it receives more than 10 SYN
packets per second from a single host destined for a single port. To modify this
default threshold, enter:
security set IDS portfloodthreshold <max>
 Loading...
Loading...