6: Accessing the router
_______________________________________________________________________________________________________
_____________________________________________________________________________________________________
© Virtual Access 2017
GW1000 Series User Manual
Issue: 1.9 Page 29 of 350
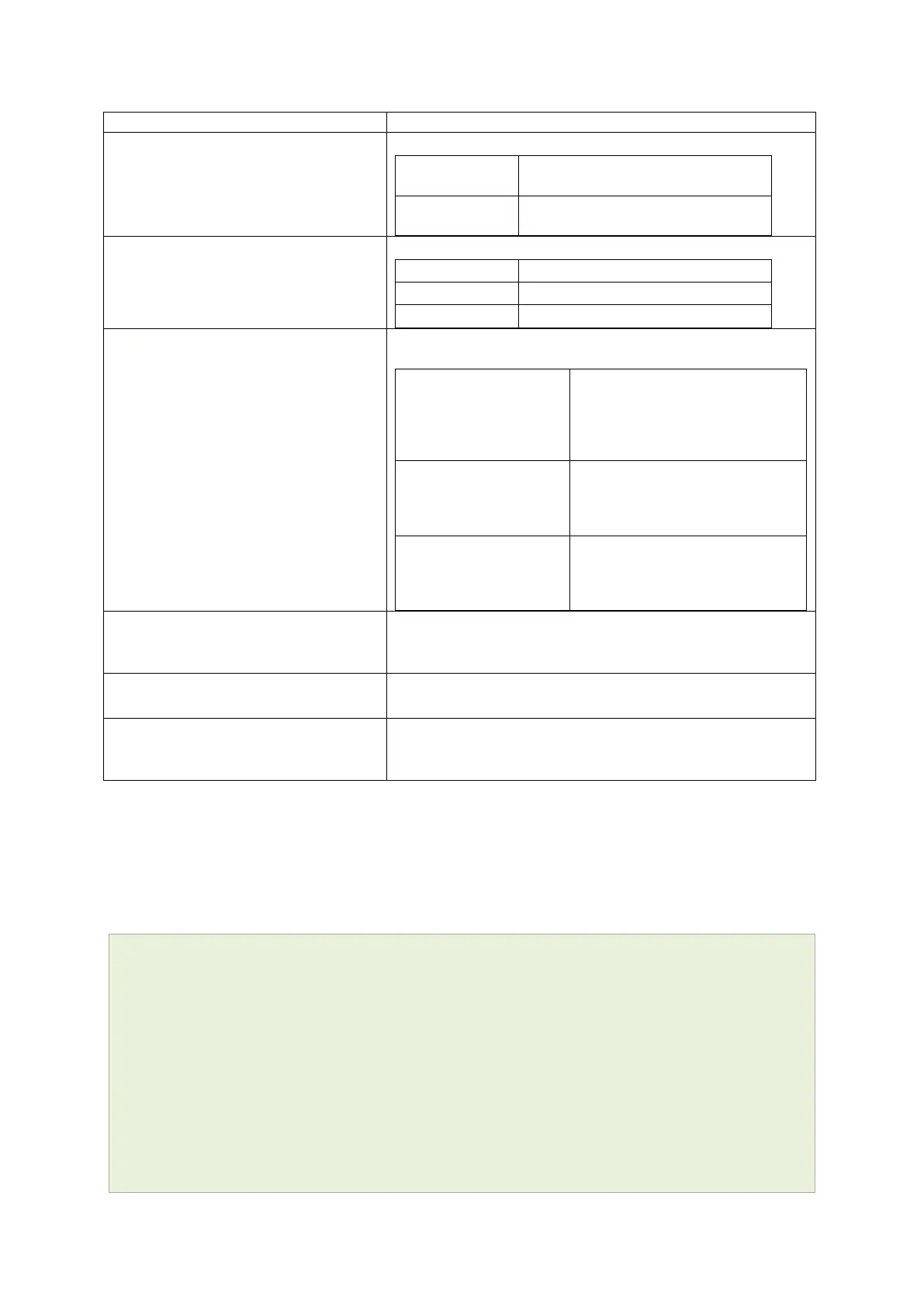
UCI: system.@pam_auth[0].enabled=yes
Opt: enabled
Enables and disables RADIUS configuration sections.
Enables following RADIUS
configuration section.
Disables following RADIUS
configuration section.
UCI: system.@pam_auth[0].pamservice
Opt: pamservice
Selects the method which users should be authenticated by.
User connecting over console cable.
User connecting over SSH.
User connecting over web.
UCI: system.@pam_auth[0].pamcontrol
Opt: pamcontrol
Specifies authentication behaviour after authentication fails or
connection to RADIUS server is broken.
First authenticates against remote
RADIUS if password authentication
fails then it tries local database
(user defined in package
management_users)
If either authentication fails or
RADIUS server is not reachable
then user is not allowed to access
the router.
[success=done
new_authtok_reqd=done
authinfo_unavail=ignore
default=die]
Local database is only checked if
RADIUS server is not reachable.
UCI:
system.@pam_auth[0].pammodule.auth
Opt: pammodule
Enables user authentication.
UCI: system.@pam_auth[0].type.radius
Opt: type
Specifies the authentication method.
UCI: system.@pam_auth[0].servers
Opt: servers
Specifies the RADIUS server or multiple servers along with port
number and password. The example below explains the syntax.
192.168.0.1:3333|test|20 192.168.2.5|secret|10
Table 9: Information table for RADIUS authentication
6.10 Accessing the device using TACACS+ authentication
TACACS+ authentication can be configured for accessing the router over SSH, web or
local console interface.
package system
config system 'main'
option hostname 'VirtualAccess'
option timezone 'UTC'
config pam_auth
option enabled 'yes'
option pamservice 'sshd'

 Loading...
Loading...