Configuring Security Features
183
This chapter provides information for making configuration changes for the following
security-related features:
Transport Layer Security
Secure Real-Time Transport Protocol
Encrypting Configuration Files
The TLS protocol is a commonly-used protocol for providing communications privacy
and managing the security of message transmission. The TLS allows the IP phone to
communicate with other remote parties and connect to the HTTPS URL for provisioning in
a way that is designed to prevent eavesdropping and tampering.
The TLS protocol is composed of two layers: the TLS Record Protocol and the TLS
Handshake Protocol. The TLS Record Protocol completes the actual data transmission
and ensures the integrity and privacy of the data. The TLS Handshake Protocol allows
the server and client to authenticate each other and negotiate an encryption algorithm
and cryptographic keys before data is exchanged.
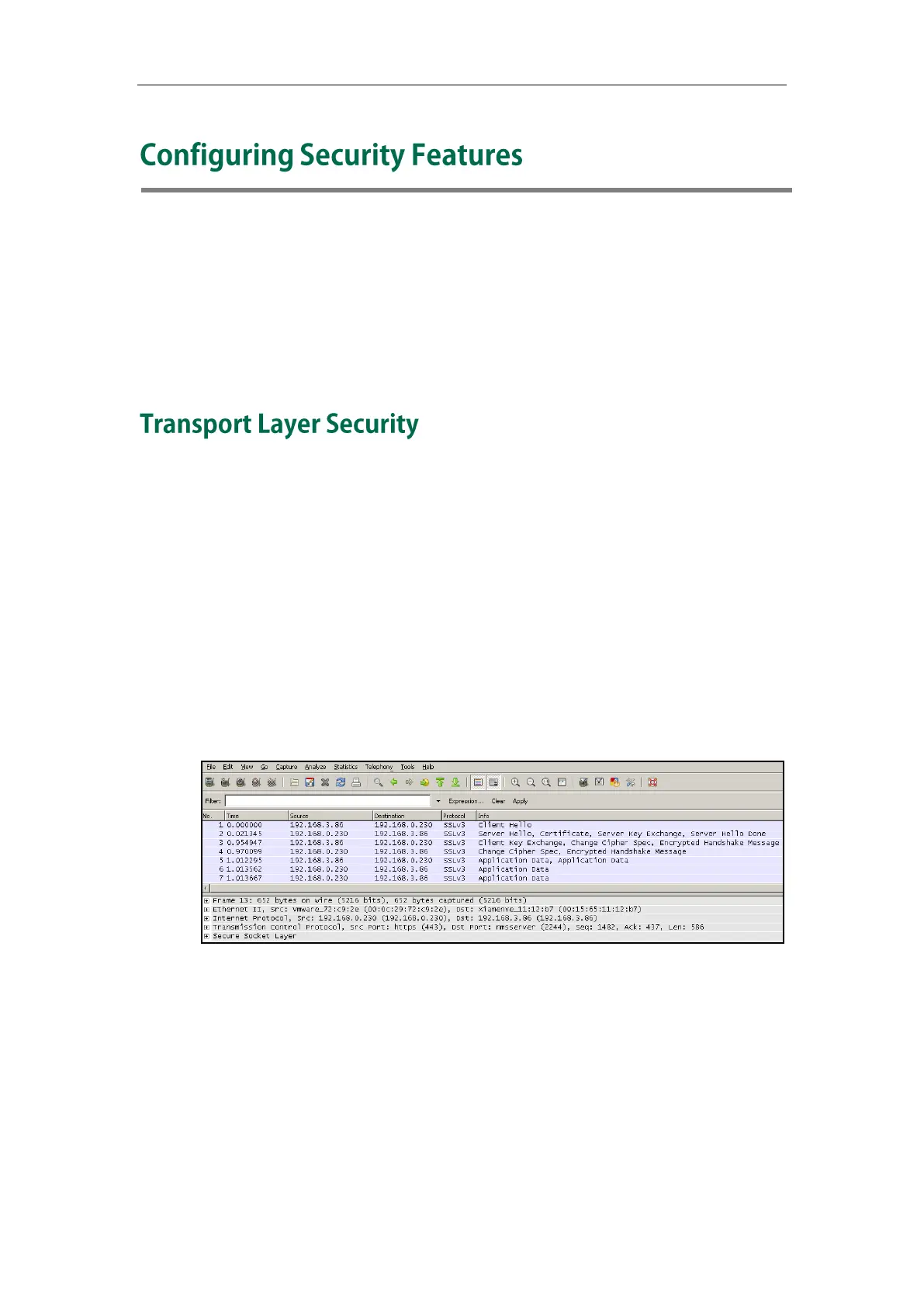
The following figure illustrates the TLS messages exchanged between the IP phone and
TLS server to establish an encrypted communication channel:
Step1: IP phone sends ―Client Hello‖ message proposing SSL options.
Step2: Server responds with ―Server Hello‖ message selecting the SSL options, sends its
public key information in ―Server Key Exchange‖ message and concludes its part of the
negotiation with ―Server Hello Done‖ message.
Step3: IP phone sends session key information (encrypted with server’s public key) in
the ―Client Key Exchange‖ message.
Step4: Server sends ―Change Cipher Spec‖ message to activate the negotiated options
for all future messages it will send.

 Loading...
Loading...






