4 Web-based Switch Configuration D-Link Smart Managed Switch User Manual
96
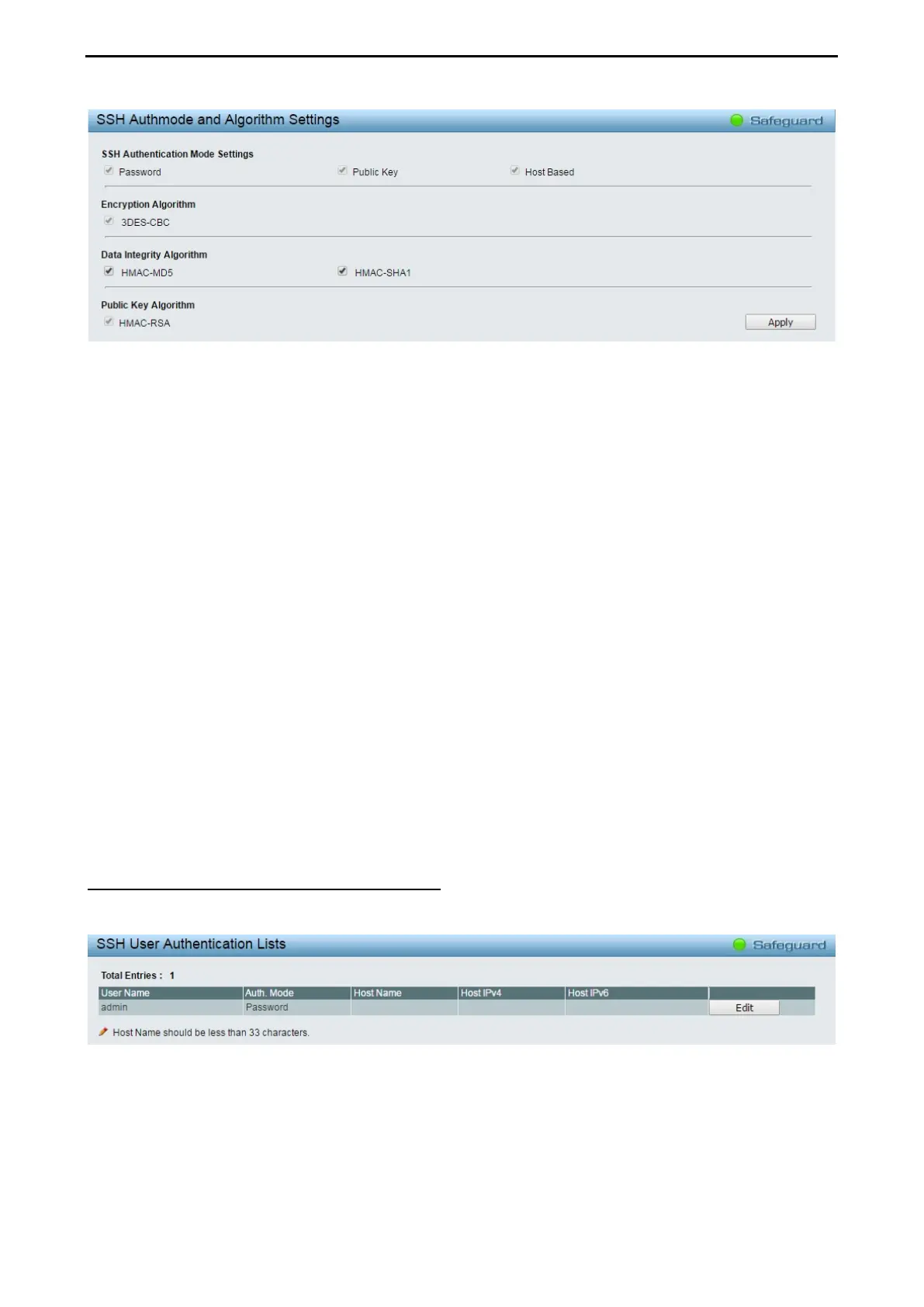
Figure 4.121 – Security > SSH > SSH Settings
SSH Authentication Mode Settings:
Password: Allows user to use a locally configured password for authentication on the Switch.
Public Key: This parameter may be enabled if the administrator wishes to use a public key configuration set
on a SSH server, for authentication on the Switch.
Host Based: This parameter may be enabled if the administrator wishes to use a host computer for
authentication. This parameter is intended for Linux users requiring SSH authentication techniques and the
host computer is running the Linux operating system with a SSH program previously installed.
Encryption Algorithm:
3DES-CBC: Use the check box to enable or disable the Triple Data Encryption Standard encryption
algorithm with Cipher Block Chaining. The default is enabled.
Data Integrity Algorithm:
HMAC-MD5: Use the check box to enable the supports of hash for message Authentication Code (HMAC)
MD5 Message Digest (MD5) mechanism.
HMAC-SHA1: Use the check box to enable the supports of hash for message Authentication Code (HMAC)
Secure Hash Algorithm (SHA) mechanism.
Public Key Algorithm:
HMAC-RSA: Use the check box to enable the supports of Hash for Message Authentication Code (HMAC)
mechanism utilizing the RSA encryption algorithm.
Click the Apply button to implement changes made.
Security > SSH > SSH User Authentication Lists
The SSH User Authentication Lists page is used to configure parameters for users attempting to access the
Switch through SSH.
Figure 4.122 – Security > SSH > SSH User Authentication Lists
The user may view the following parameters:
User Name: A name of no more than 15 characters to identify the SSH user. This User Name must be a
previously configured user account on the Switch.
Auth. Mode: The administrator may choose one of the following to set the authorization for users attempting
to access the Switch.

 Loading...
Loading...











