CLSS Gateway - Installation and Users’ Manual | P/N:LS10248-000HW-E | REV. F | FEB/11/2022 21
For Preventing Potential Risks Security Recommendations
Best Practices: Network Security
Open protocols, unencrypted connections, and unauthenticated sites are risks.
Ensure the following:
• Required firewalls and VPN connections are in place
• The logging systems monitor malicious activity and perform regular audits
• Unused services and ports are disabled
• Security patches are up to date
• Users have only minimum required privileges for files and folders
Best Practices: Connected Devices
For VESDA Detectors
• Adhere to the xtralis security guidelines: https://xtralis.com/file/9584
• When connected with one VESDA detector, use a short point-to-point link between
the VESDA detector and the CLSS Gateway.
• When connected with multiple VESDA detectors, allow only the VESDA detectors and
the gateway connections. Do not allow any other connections.
• Allow only authorized personnel to configure VESDA devices.
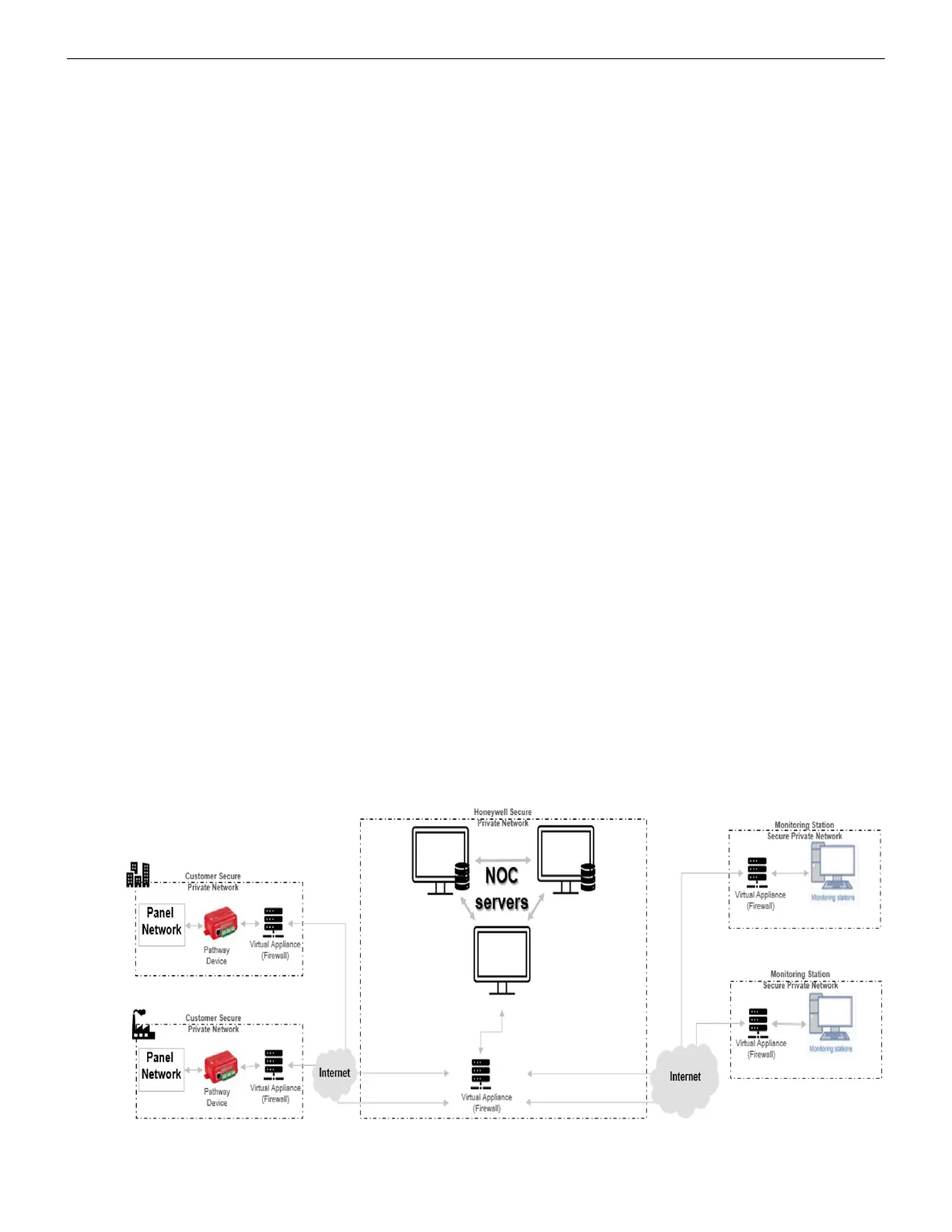
3.2.6 Securing the Monitoring Stations
• Good security practices should be observed on the Monitoring Station PCs.
• Operating systems and software should be kept up to date by installing the
manufacturers updates, as well as maintaining up-to-date anti-virus software on all
computers, which may be connected directly or via a network.
• For monitoring stations, it is recommended to use secure VPN channel, which must
be placed behind the firewall.
• It is suggested to use hardware receiver as an adapter at the monitoring station.
• For the CLSS Pathway devices, it is recommended to use secure private network, and
keep them behind the firewall.
• Only authorized personnel should get access to private network.
• Best industry standards should be followed while configuring the firewall policies.
• Devices should be safely installed in the secure zone and they must be out of reach to
unauthorized personnel.
• Ensure that the computers are regularly scanned for viruses.
• Only install files and software from trusted sources and use only them on associated
computers to avoid malicious software.
• Use only authorized removable media. For example, use CD, DVD, external hard drives,
or USB memory sticks, which have been scanned using up-to-date anti-virus
software.

 Loading...
Loading...











