Chapter 2 Deploying Cisco Secure ACS
Basic Deployment Factors for Cisco Secure ACS
2-12
User Guide for Cisco Secure ACS for Windows Server
78-14696-01, Version 3.1
• Security—VPNs provide the highest level of security using advanced
encryption and authentication protocols that protect data from unauthorized
access.
• Scalability—VPNs allow corporations to use remote access infrastructure
within ISPs; therefore, corporations can add a large amount of capacity
without adding significant infrastructure.
• Compatibility with Broadband Technology—VPNs allow mobile workers,
telecommuters, and day extenders to take advantage of high-speed,
broadband connectivity, such as DSL and cable, when gaining access to their
corporate networks, providing workers significant flexibility and efficiency.
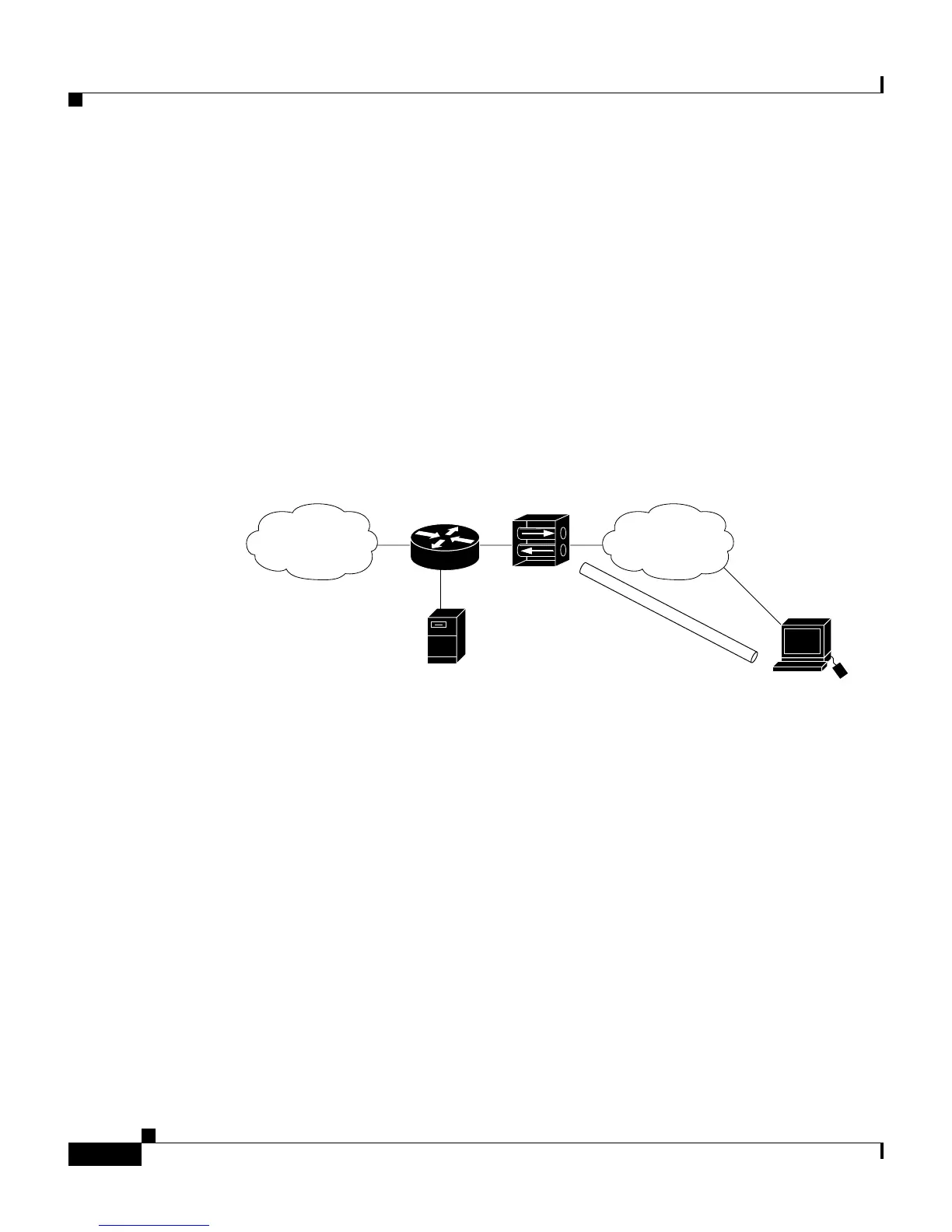
Figure 2-7 Simple VPN Configuration
There are two types of VPN access into a network:
• Site-to-Site VPNs—Extend the classic WAN by providing large-scale
encryption between multiple fixed sites such as remote offices and central
offices, over a public network, such as the Internet.
• Remote Access VPNs—Permit secure, encrypted connections between
mobile or remote users and their corporate networks via a third-party
network, such as an ISP, via VPN client software.
Generally speaking, site-to-site VPNs can be viewed as a typical WAN
connection and are not usually configured to use AAA to secure the initial
connection and are likely to use the device-oriented IPSec tunneling protocol.
Remote Access VPNs, however, are similar to classic remote connection
technology (modem/ISDN) and lend themselves to using the AAA model
effectively (Figure 2-8).
VPN concentrator
Cisco Secure
Access Control Server
Network WAN
Tunnel
63492
 Loading...
Loading...











