246
[SwitchB-ike-profile-profile1] quit
# Create an IKE mode IPsec policy entry, with the policy name use1, and sequence number 10.
[SwitchB] ipsec policy use1 10 isakmp
# Apply ACL 3101.
[SwitchB-ipsec-policy-isakmp-use1-10] security acl 3101
# Apply the IPsec transform set tran1.
[SwitchB-ipsec-policy-isakmp-use1-10] transform-set tran1
# Specify the local and remote IP addresses of the IPsec tunnel as 2.2.3.1 and 2.2.2.1.
[SwitchB-ipsec-policy-isakmp-map1-10] local-address 2.2.3.1
[SwitchB-ipsec-policy-isakmp-use1-10] remote-address 2.2.2.1
# Apply the IKE profile profile1.
[SwitchB-ipsec-policy-isakmp-use1-10] ike-profile profile1
[SwitchB-ipsec-policy-isakmp-use1-10] quit
# Apply the IPsec policy use1 to interface VLAN-interface 1.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] ipsec apply policy use1
Verifying the configuration
After the previous configurations, IKE negotiation is triggered to set up IPsec SAs when there are
end-to-end packets between Switch A and Switch B. After IPsec SAs are successfully negotiated by IKE,
the traffic between the two switches is IPsec protected.
Configuring IPsec for RIPng
Network requirements
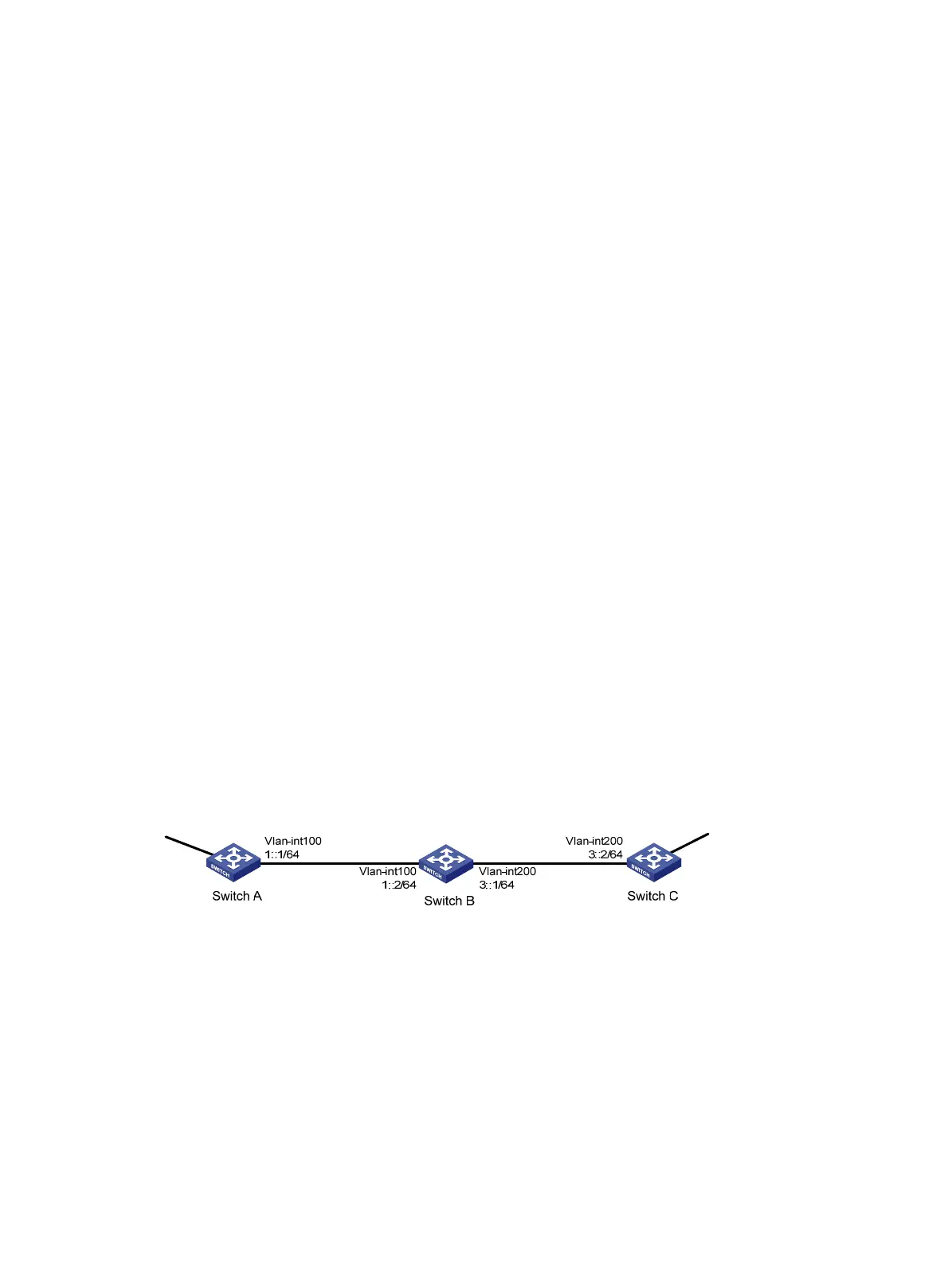
As shown in Figure 82, Switch A, Switch B, and Switch C learn IPv6 routes through RIPng.
Establish an IPsec tunnel between the switches to protect the RIPng packets transmitted in between.
Specify the security protocol as ESP, the encryption algorithm as 128-bit AES, and the authentication
algorithm as HMAC-SHA1 for the IPsec tunnel.
Figure 82 Network diagram
Configuration considerations
1. Configure basic RIPng.
For more information about RIPng configurations, see Layer 3—IP Routing Configuration Guide.
2. Configure an IPsec profile.
{ The IPsec profiles on all the switches must have IPsec transform sets that use the same security
protocol, authentication and encryption algorithms, and encapsulation mode.
{ The SPI and key configured for the inbound SA and those for the outbound SA must be the same
on each switch.
{ The SPI and key configured for the SAs on all the switches must be the same.
 Loading...
Loading...





