186
A certificate must be revoked when, for example, the username changes, the private key is compromised,
or the user is no longer certified by the CA. The CA periodically publishes a CRL that contains the serial
numbers of all revoked certificates. CRLs provide an effective way for verifying the validity of certificates.
CA policy
A CA policy is a set of criteria that a CA follows to process certificate requests, to issue and revoke
certificates, and to publish CRLs. Typically, a CA advertises its policy in a certification practice statement
(CPS). You can obtain a CA policy through out-of-band means such as phone, disk, and email. Make
sure you understand the CA policy before you select a trusted CA for certificate request because different
CAs might use different policies.
PKI architecture
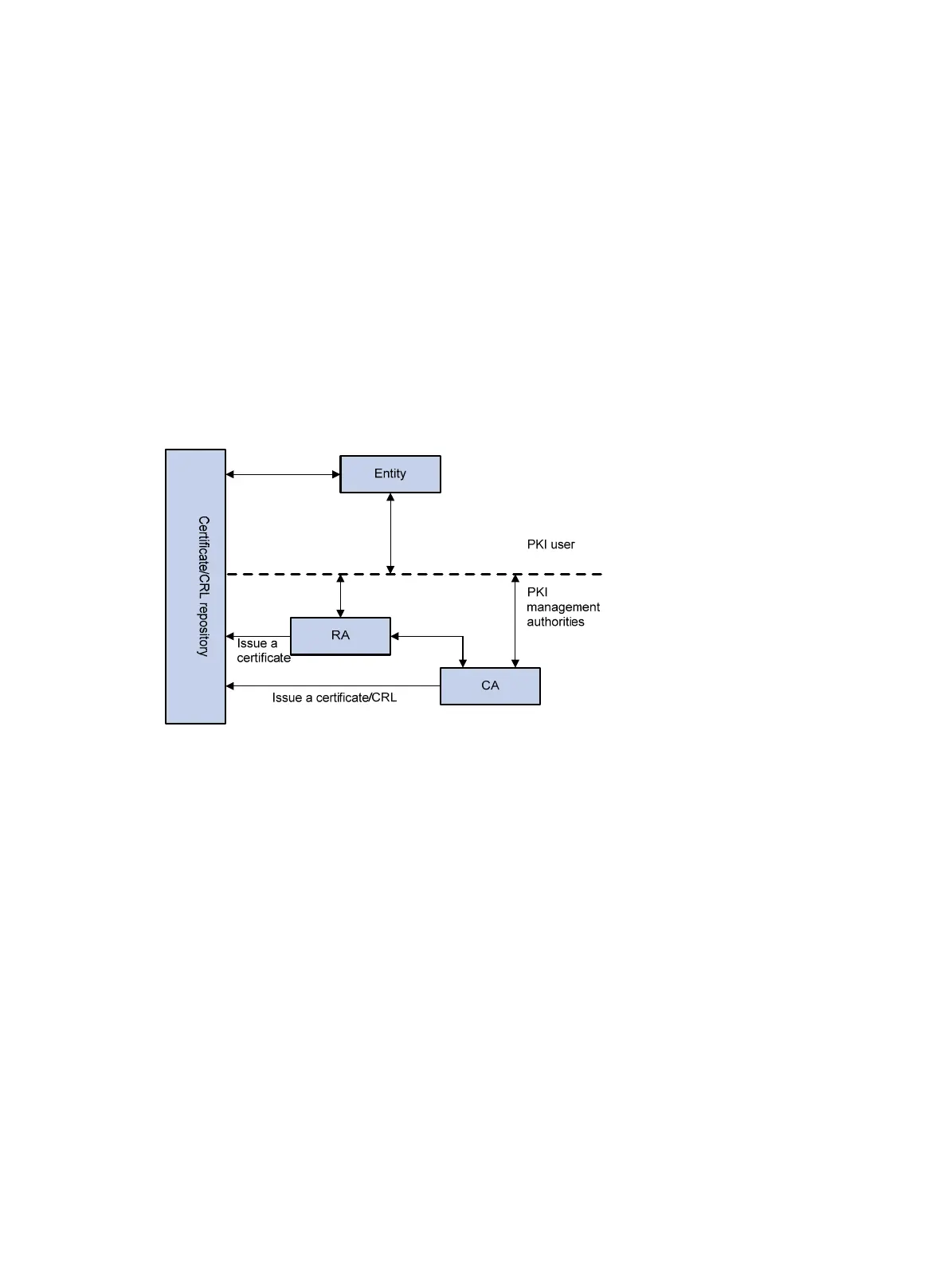
A PKI system consists of PKI entities, CAs, RAs and a certificate/CRL repository, as shown in Figure 71.
Figure 71 PKI architecture
• PKI entity—An end user using PKI certificates. The PKI entity can be an operator, an organization,
a device like a router or a switch, or a process running on a computer. PKI entities use SCEP to
communicate with the CA or RA.
• CA—Certification authority that grants and manages certificates. A CA issues certificates, defines
the certificate validity periods, and revokes certificates by publishing CRLs.
• RA—Registration authority, which offloads the CA by processing enrollment requests. The RA
accepts certificate requests, verifies user identity, and determines whether to ask the CA to issue
certificates.
The RA is optional in a PKI system. In cases when the CA operates over a wide geographical area
or when there is security concern over exposing the CA to direct network access, it is advisable to
delegate some of the tasks to an RA and leave the CA to concentrate on its primary tasks of signing
certificates and CRLs.
• Repository—A certificate distribution point that stores certificates and CRLs, and distributes these
certificates and CRLs to PKI entities. It also provides the query function. A PKI repository can be a
directory server using the LDAP or HTTP protocol, of which LDAP is commonly used.
PKI operation
The following workflow describes how a PKI entity requests a local certificate from a CA that has RAs:

 Loading...
Loading...





