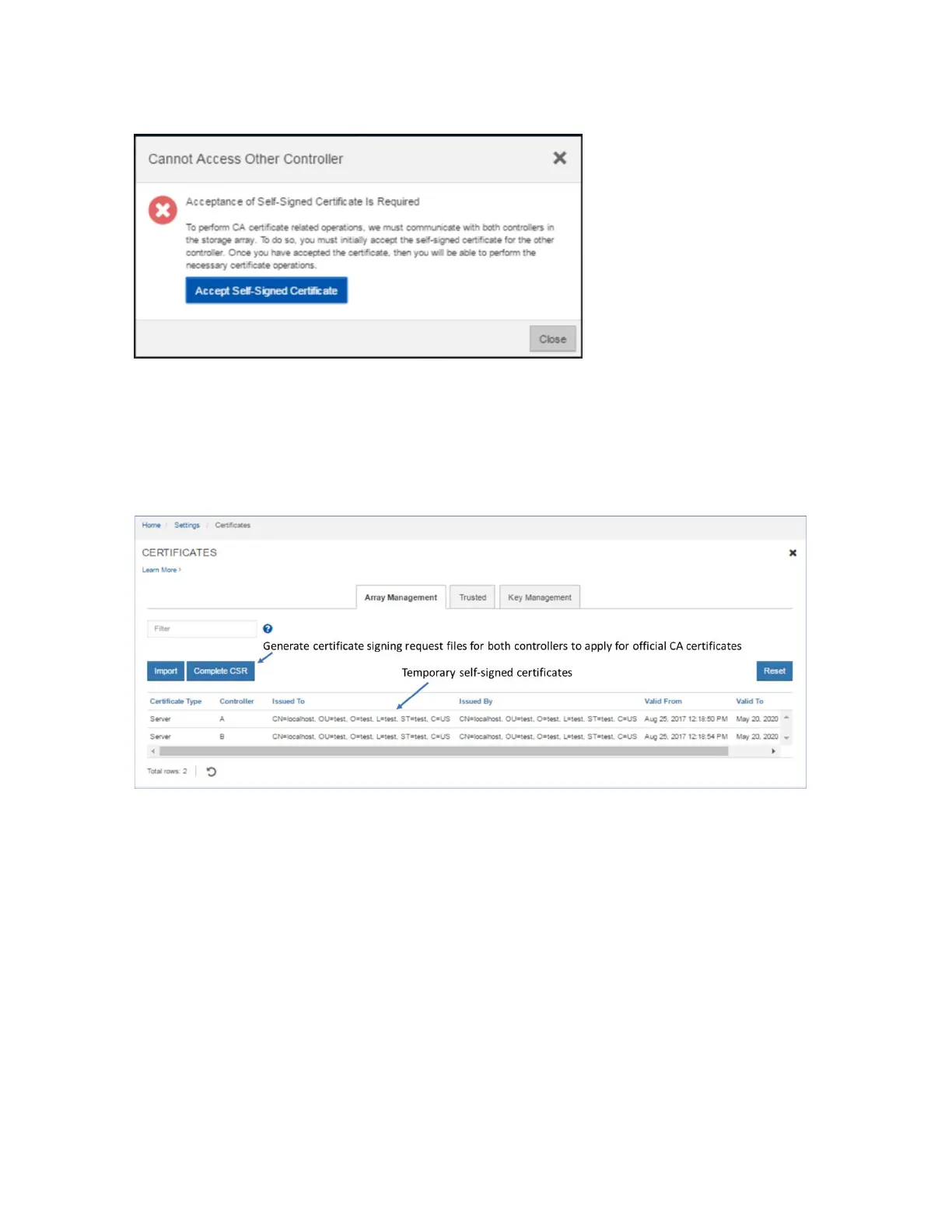
Figure 32) Initial step required to set up web server certificates.
You must accept the self-signed certificate to continue setting up certificates. The process takes you to
another webpage, where the certificate is created in the background. Follow the prompts to complete the
process. When the process is complete, the array requires the admin user or a user with security
permissions to log in again. Both controllers are then displayed with valid local host certificates, as shown
in Figure 33.
Figure 33) Expanded SANtricity System Manager Certificates tile.
To enable the E-Series onboard web servers to validate certificates from external client browsers, the
controllers are preloaded with industry-standard CA root certificates. To view the standard root
certificates, select the Trusted tab in the Certificates tile window shown in Figure 33 and then select Show
Preinstalled Certificates from the drop-down menu.
Multifactor Authentication
Feature Overview
Multifactor authentication (MFA) includes several new functional areas on E5750 arrays:
• Authentication with Security Assertion Markup Language (SAML) 2.0 to support MFA. You can
manage authentication through an identity provider (IdP) by using SAML 2.0. An administrator
establishes communication between the IdP system and the storage array and then maps IdP users
to the local user roles embedded in the storage array. Using IdP allows the administrator to configure
MFA.

 Loading...
Loading...