20-10
Catalyst 2960 and 2960-S Switches Software Configuration Guide, Release 15.0(1)SE
OL-26520-01
Chapter 20 Configuring DHCP and IP Source Guard Features
Configuring DHCP Snooping
• Configuring the relay agent forwarding policy
Enabling DHCP Snooping and Option 82
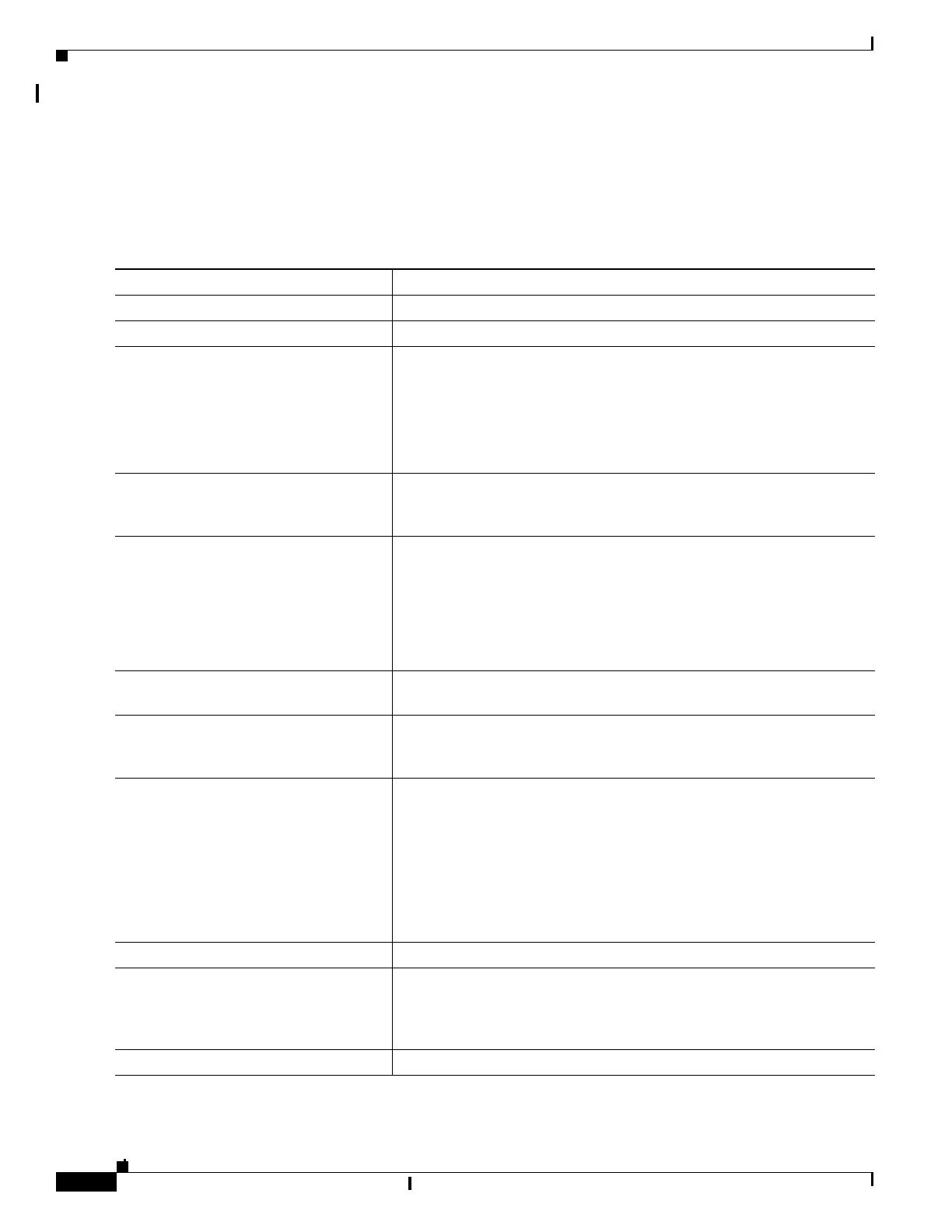
Beginning in privileged EXEC mode, follow these steps to enable DHCP snooping on the switch:
Command Purpose
Step 1
configure terminal Enter global configuration mode.
Step 2
ip dhcp snooping Enable DHCP snooping globally.
Step 3
ip dhcp snooping vlan vlan-range Enable DHCP snooping on a VLAN or range of VLANs. The range is
1to4094.
You can enter a single VLAN ID identified by VLAN ID number, a series
of VLAN IDs separated by commas, a range of VLAN IDs separated by
hyphens, or a range of VLAN IDs separated by entering the starting and
ending VLAN IDs separated by a space.
Step 4
ip dhcp snooping information option Enable the switch to insert and to remove DHCP relay information
(option-82 field) in forwarded DHCP request messages to the DHCP
server. This is the default setting.
Step 5
ip dhcp snooping information option
allow-untrusted
(Optional) If the switch is an aggregation switch connected to an edge
switch, enable the switch to accept incoming DHCP snooping packets
with option-82 information from the edge switch.
The default setting is disabled.
Note Enter this command only on aggregation switches that are
connected to trusted devices.
Step 6
interface interface-id Specify the interface to be configured, and enter interface configuration
mode.
Step 7
ip dhcp snooping trust (Optional) Configure the interface as trusted or as untrusted. Use the no
keyword to configure an interface to receive messages from an untrusted
client. The default setting is untrusted.
Step 8
ip dhcp snooping limit rate rate (Optional) Configure the number of DHCP packets per second that an
interface can receive. The range is 1 to 2048. By default, no rate limit is
configured.
Note We recommend an untrusted rate limit of not more than 100
packets per second. If you configure rate limiting for trusted
interfaces, you might need to increase the rate limit if the port is
a trunk port assigned to more than one VLAN with DHCP
snooping.
Step 9
exit Return to global configuration mode.
Step 10
ip dhcp snooping verify mac-address (Optional) Configure the switch to verify that the source MAC address in
a DHCP packet received on untrusted ports matches the client hardware
address in the packet. The default is to verify that the source MAC
address matches the client hardware address in the packet.
Step 11
end Return to privileged EXEC mode.
 Loading...
Loading...
















