30-3
Catalyst 2960 and 2960-S Switches Software Configuration Guide, Release 15.0(1)SE
OL-26520-01
Chapter 30 Configuring SNMP
Understanding SNMP
SNMPv2C includes a bulk retrieval mechanism and more detailed error message reporting to
management stations. The bulk retrieval mechanism retrieves tables and large quantities of information,
minimizing the number of round-trips required. The SNMPv2C improved error-handling includes
expanded error codes that distinguish different kinds of error conditions; these conditions are reported
through a single error code in SNMPv1. Error return codes in SNMPv2C report the error type.
SNMPv3 provides for both security models and security levels. A security model is an authentication
strategy set up for a user and the group within which the user resides. A security level is the permitted
level of security within a security model. A combination of the security level and the security model
determine which security mechanism is used when handling an SNMP packet. Available security models
are SNMPv1, SNMPv2C, and SNMPv3.
Table 30-1 identifies the characteristics of the different combinations of security models and levels.
You must configure the SNMP agent to use the SNMP version supported by the management station.
Because an agent can communicate with multiple managers, you can configure the software to support
communications using SNMPv1, SNMPv2C, or SNMPv3.
SNMP Manager Functions
The SNMP manager uses information in the MIB to perform the operations described in Table 30-2.
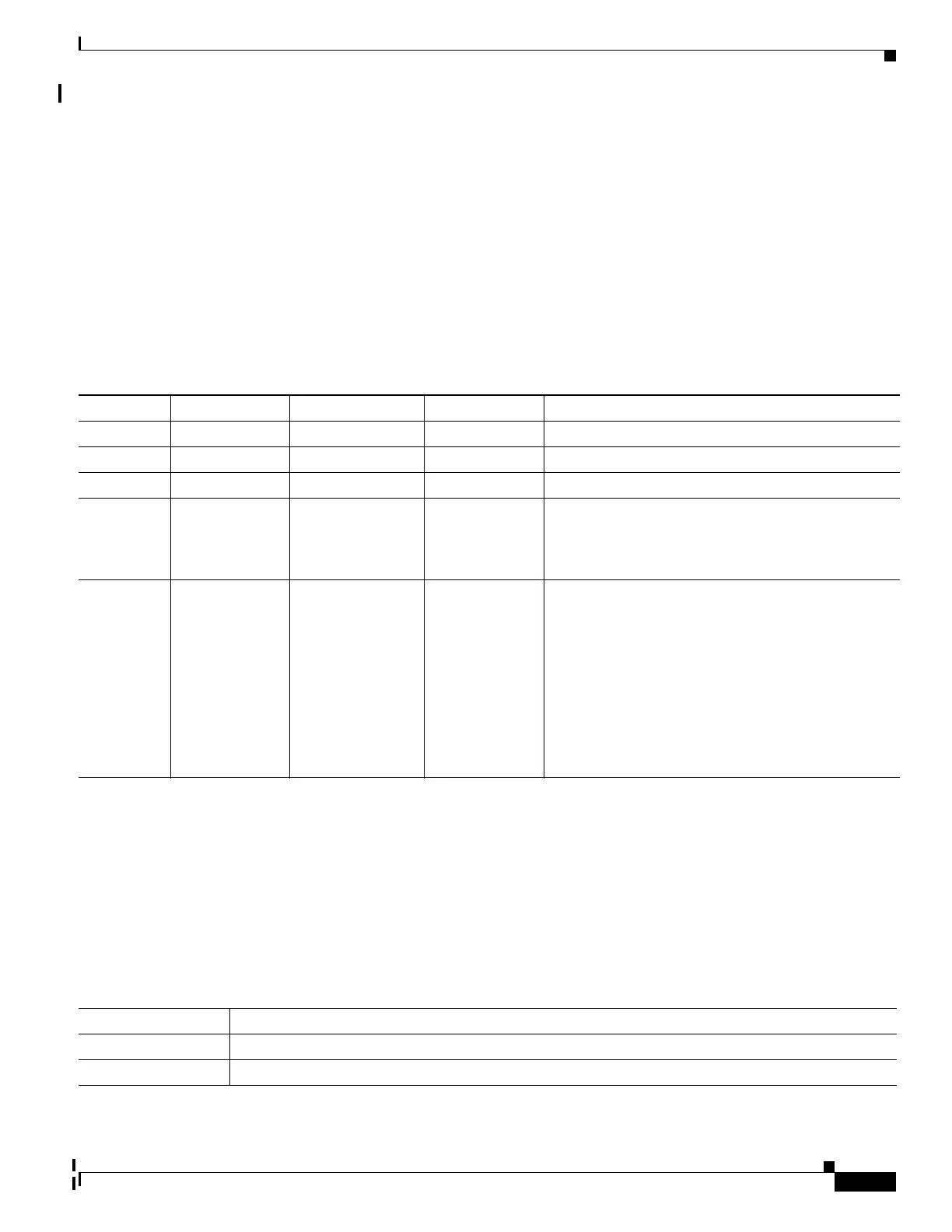
Table 30-1 SNMP Security Models and Levels
Model Level Authentication Encryption Result
SNMPv1 noAuthNoPriv Community string No Uses a community string match for authentication.
SNMPv2C noAuthNoPriv Community string No Uses a community string match for authentication.
SNMPv3 noAuthNoPriv Username No Uses a username match for authentication.
SNMPv3 authNoPriv Message Digest 5
(MD5) or Secure
Hash Algorithm
(SHA)
No Provides authentication based on the HMAC-MD5 or
HMAC-SHA algorithms.
SNMPv3 authPriv
(requires the
cryptographic
software image)
MD5 or SHA Data Encryption
Standard (DES)
or Advanced
Encryption
Standard (AES)
Provides authentication based on the HMAC-MD5 or
HMAC-SHA algorithms. Allows specifying the
User-based Security Model (USM) with these
encryption algorithms:
• DES 56-bit encryption in addition to
authentication based on the CBC-DES (DES-56)
standard.
• 3DES 168-bit encryption
• AES 128-bit, 192-bit, or 256-bit encryption
Table 30-2 SNMP Operations
Operation Description
get-request Retrieves a value from a specific variable.
get-next-request Retrieves a value from a variable within a table.
1
 Loading...
Loading...
















