SECURITY
Version 4.2.7.2, 05/2014. Copyright 2012 Hitron Technologies
106
Version 4.2.7.2, 05/2014. Copyright 2014 Hitron Technologies
106
Hitron CGNV User’s Guide
7.5.1 Adding or Editing a Trust PC List
To add a new trust PC to the list, click Add Trust Device in the Security >
Keyword Filter screen.
To edit an existing trust PC in the list, locate the device in the Security >
Keyword Filter screen and click its Manage button.
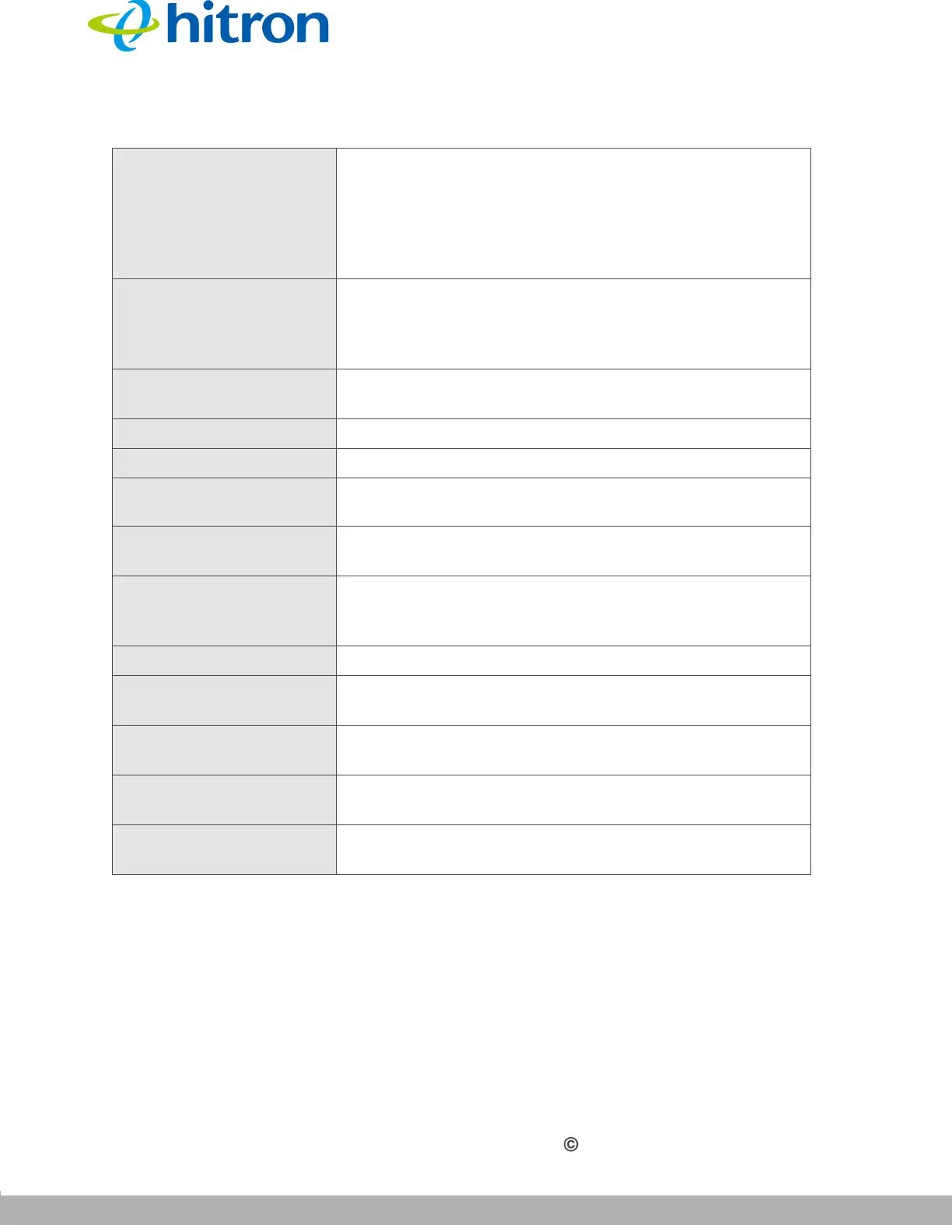
Blocked Weekdays Use these fields to specify the times at which the
keyword should be blocked. A red background indicates
that the rule will be applied (access will be blocked), and
a green background indicates that the device will not be
applied (access will not be blocked). Click a day to
toggle the rule on or off for the relevant day.
Blocked Time Use these fields to specify the period during which the
rule should be applied. Enter the start time in the From
fields, using twenty-four hour notation, and enter the
end time in the To fields.
Action Click Add to create a new keyword blocking rule; a new
row of fields display.
Trust PC List
APP Name This displays the name of the trust device connected.
IP Address This displays the IP address of the trust network device
connected.
Status This displays whether or not the keyword filter rule is
enabled
of the trust device connected.
Manage Click Manage to make changes to the trust device’s
keyword filter status; see Adding or Editing a Trust PC
List on page 106.
Action Click to delete the existing trust device from the list.
Add Trust Device Click this to add a new Trust Device. (see Adding or
Editing a Trust PC List on page 106).
Save Changes Click this to save your changes to the fields in this
screen.
Cancel Click this to return the fields in this screen to their last-
saved values without saving your changes.
Help Click this to see information about the fields in this
screen.
Table 40: The Security: Keyword Filter Screen (continued)
 Loading...
Loading...