Honeywell® FS24XPlus™ | User Manual
10
Security Guide
The construction of a reliable flame detection system requires protecting the equipment from
unauthorized changes. The installer should comprehensively consider all types of tampering,
including over digital networks. The FS24XPlus™ is not vulnerable to traditional cyberattacks
because it does not contain any type of radio or routable communications protocol such as internet
protocol (IP). Security is usually achieved by listing and then limiting the attack vectors. An “attack
vector” is an approach that a malicious operator might try to exploit to harm the target. Possible
attack vectors are listed below. This has been made as comprehensive as possible to aid analysis.
Some of the attack vectors may be dismissed as trivial.
Cybersecurity traditionally has three goals – integrity, availability, and confidentiality. However,
confidentiality is excluded from the table below because it has lower importance in most flame
detection applications.
Note that the HART® interface is disabled by default. If desired, it can be enabled using
FlameManager.
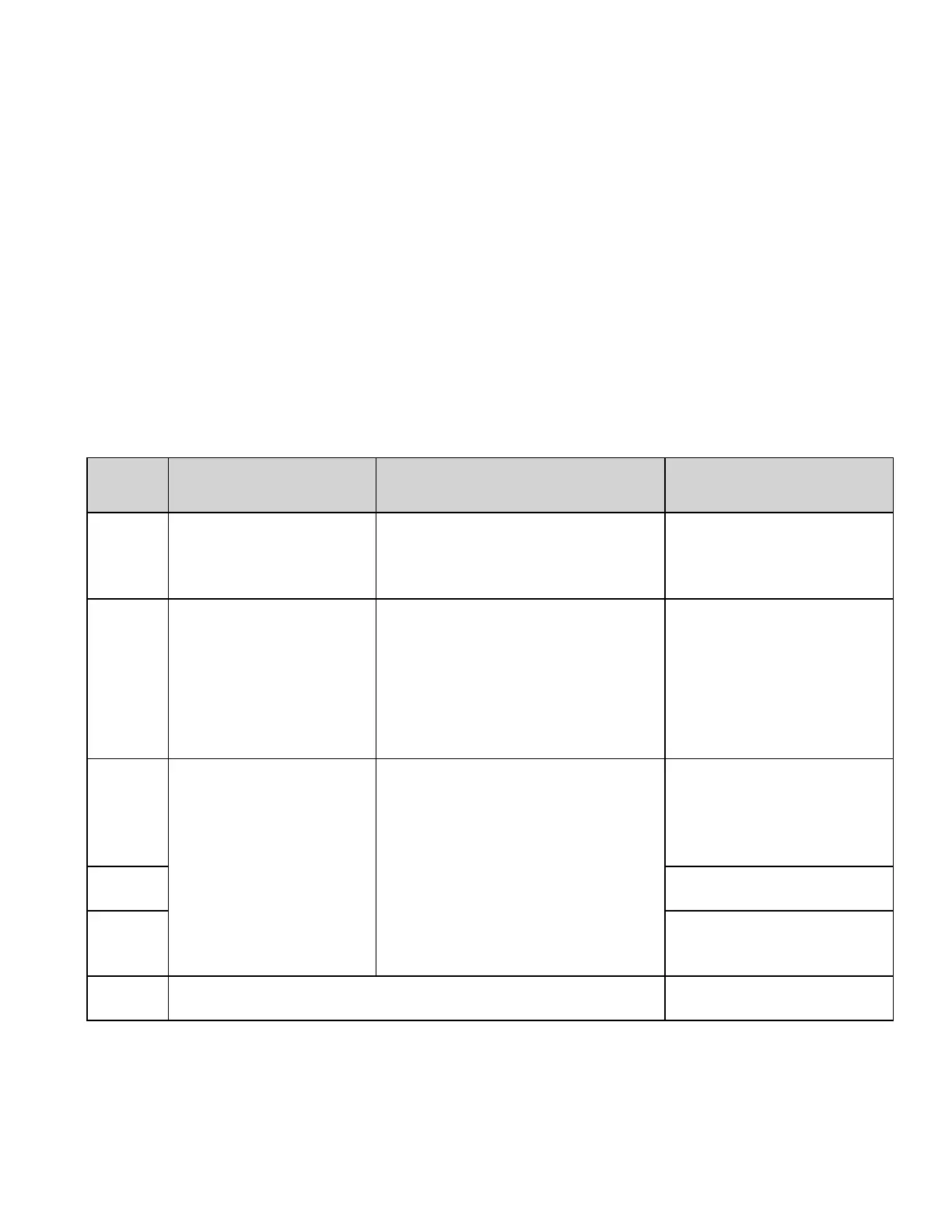
Attack
Vector
Integrity,
Reliable detection of fire
Availability,
Uptime, No nuisance alarms
Mitigation,
Defense Measures
Disrupt
the front
window
Yes – Foreign material
could block the infrared
energy and prevent
detection of fire.
Yes – Flashing light from malicious
use of the test lamp.
Limit access by
unauthorized personnel.
Analog
signal
wires
Power,
20 mA,
relay
Yes – The detector could
be replaced with a
resistor in the mA loop.
Relay wiring could be cut
or shorted.
Yes – Resistance could be added in
series to generate a fault report or
in parallel to generate an alarm
report. Relay wiring could be cut or
shorted.
The power wiring could be cut,
causing a fault report.
Limit access by
unauthorized personnel.
Regularly perform end-to-
end testing.
HART®
Yes – The detector could
be inhibited, or the
sensitivity could be mis-
set low.
Yes – the outputs can be driven to
alarm state or the sensitivity could
be mis-set high.
Leave the HART® interface
in the default disabled state
unless used. Protect the
cabling from unauthorized
access.
USB-FP2
Secure the enclosure with
the supplied set screw.
RS-485
FP2
Protect cabling or leave RS-
485 terminals
unconnected.
RS-485
Modbus®
No – interface is read only. No defense needed.
Note that by default the RS-485 interface is configured for FP2, not Modbus. It can be switched
between these protocols using FlameManager.
Cybercriminals frequently display astonishing creativity. A flame detection system should be
configured to resist attacks years in the future, during the equipment’s entire life cycle. The system
should be regularly tested end-to-end.
 Loading...
Loading...











