MX Series Voice Gateway User Manual
New Rock Technologies, Inc. 97
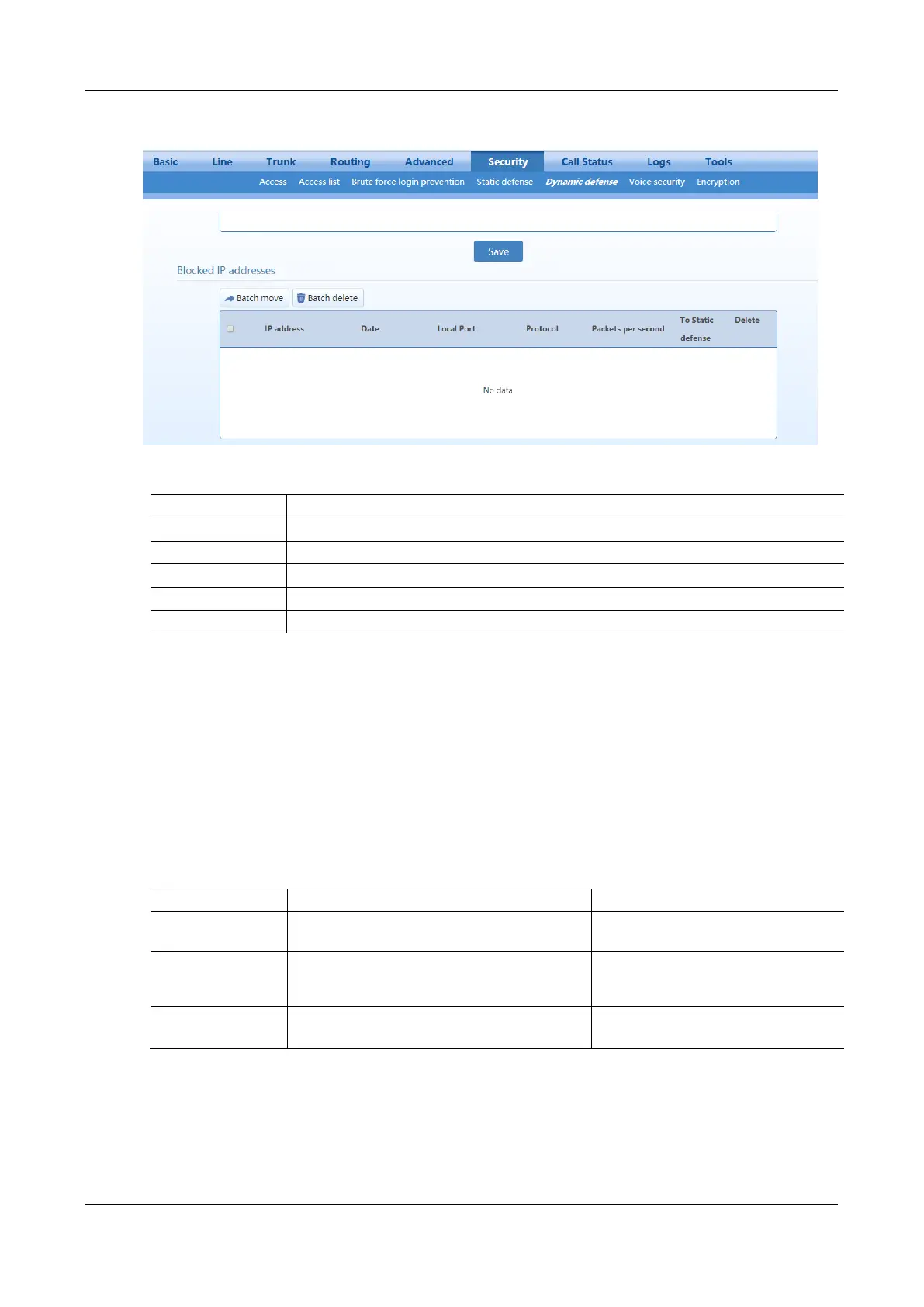
Figure 2-61 Dynamic Defense (Blocked IP Addresses) Interface
Table 2-39 Dynamic Defense (Blocked IP Addresses) Information
The IP address of the attacker detected by the device.
The time when the device detects the attacker and initiates defense.
The port through which the data packet from the attacker is received.
The data packet receiving rate threshold.
You can perform the following operations:
Batch move: Move the selected entries in batch to the static defense rules, and provides three subsequent choices:
Block: Add the entry to the static defense list and block the matched packets.
Accept: Add the entry to the static defense list and accept the matched packets.
Cancel: Cancel to add the entry to the static defense list.
Table 2-40 Subsequent choices for moving the Blocked IP Addresses to static defense
Add the entry to the static defense list and block
the matched packets.
These entries are confirmed to be attach
sources.
Add the entry to the static defense list and accept
the matched packets.
These entries are confirmed to be valid
sources (applicable to heavy traffic
scenarios such as call centers).
Cancel to add the entry to the static defense list.
For details about static defense, see 2.7.4 ACL-based Traffic Filtering.
Batch delete: Delete selected entries in a batch.
Example
Explanations of the rules listed in Figure 2-60 are as follows:
 Loading...
Loading...