Version 5.2 Sourcefire 3D System Installation Guide 45
Understanding Deployment
Deployment Options
Chapter 2
If the packet meets the conditions of a rule, traffic flow and inspection depend on
the rule action. If no rules match the packet, traffic flow and inspection depend on
the default policy action. (An exception occurs with Monitor rules, which allow
traffic to continue to be evaluated.) The default action on each access control
policy manages traffic that has not been fast-pathed or blacklisted, or matched by
any non-Monitor rule. Note that fast-path is available only for 8000
Series and
3D9900 devices.
You can create access control rules to provide more granular control over how you
handle and log network traffic. For each rule, you specify an action (trust, monitor,
block, or inspect) to apply to traffic that meets specific criteria.
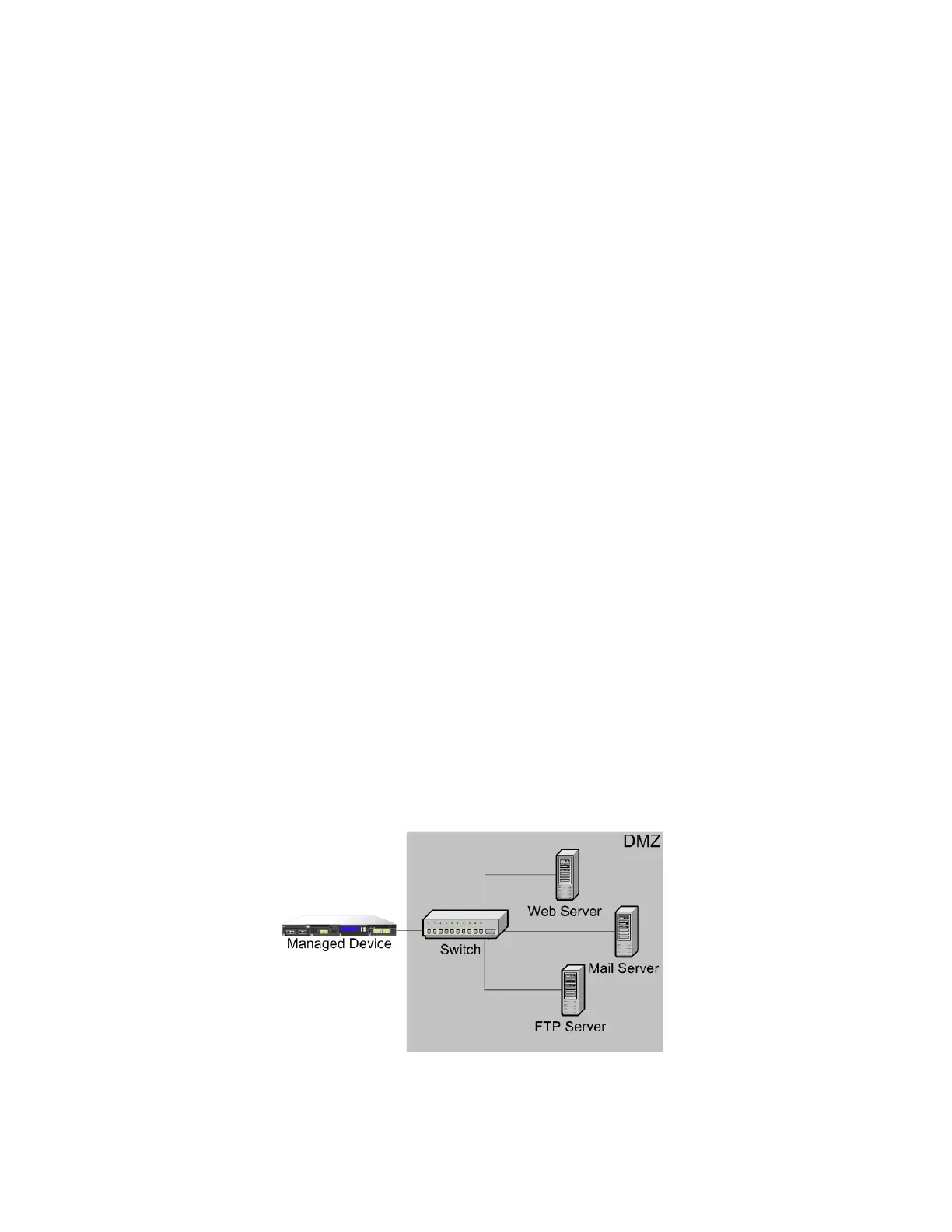
On the DMZ
The DMZ contains outward-facing servers (for example, web, FTP, DNS, and
mail), and may also provide services such as mail relay and web proxy to users on
the internal network.
Content stored in the DMZ is static, and changes are planned and executed with
clear communication and advance notice. Attacks in this segment are typically
inbound and become immediately apparent because only planned changes
should occur on the servers in the DMZ. An effective access control policy for this
segment tightly controls access to services and searches for any new network
events.
Servers in the DMZ can contain a database that the DMZ can query via the
network. Like the DMZ, there should be no unexpected changes, but the
database content is more sensitive and requires greater protection than a web
site or other DMZ service. A strong intrusion policy, in addition to the DMZ access
control policy, is an effective strategy.
A managed device deployed on this segment can detect attacks directed to the
Internet that originate from a compromised server in the DMZ. Monitoring
network traffic using Network Discovery can help you monitor these exposed
servers for changes (for example, an unexpected service suddenly appearing) that
could indicate a compromised server in the DMZ.
 Loading...
Loading...