Operation Manual – SSH2.0
Quidway S3100 Series Ethernet Switches Chapter 1
SSH Terminal Services
Huawei Technologies Proprietary
1-2
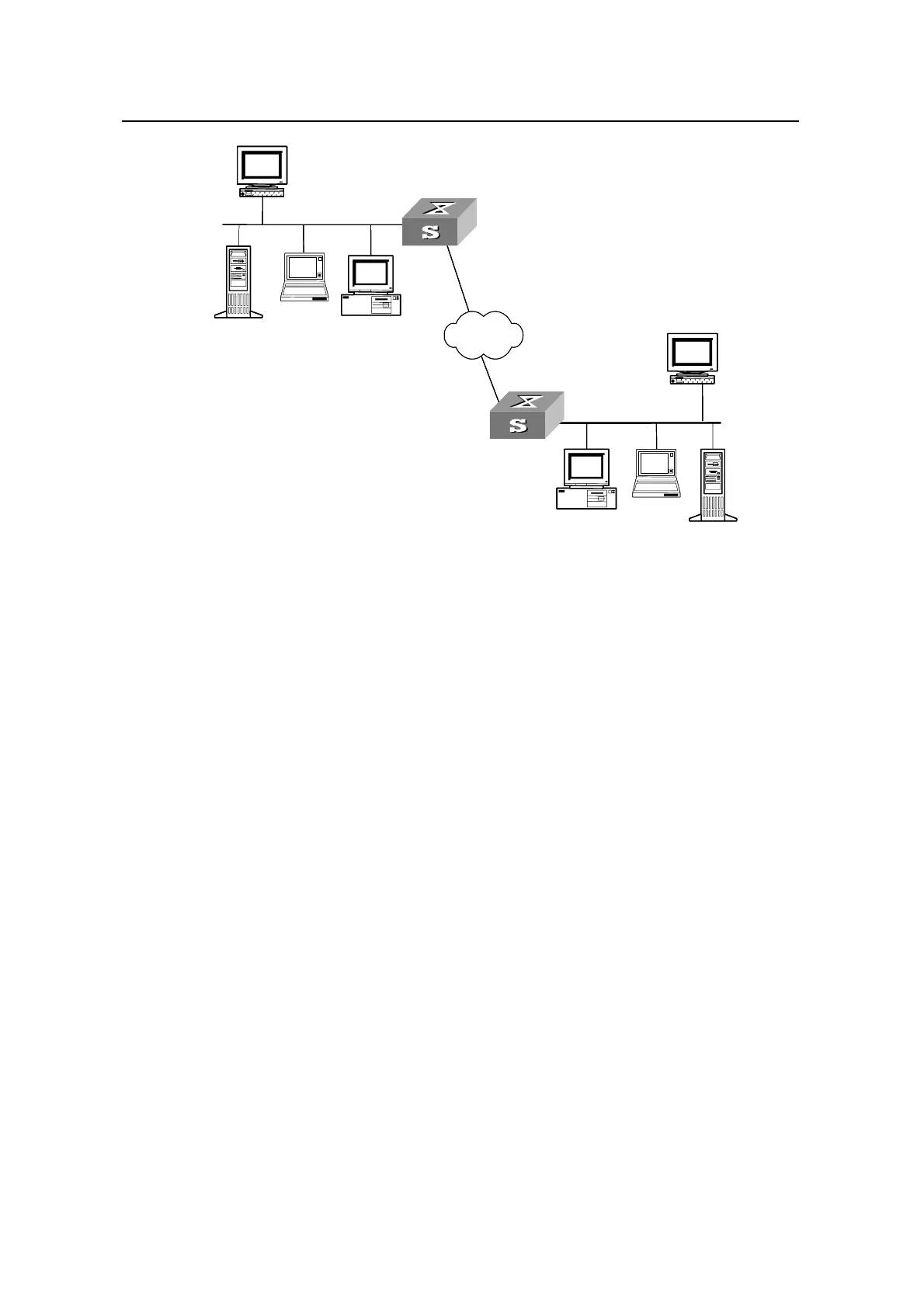
Local Switch
Local Ethernet
WAN
Server
PC
SSH-Client
PC
Laptop
Laptop
PC
Laptop
Workstation
Laptop
Workstation
Remot
Remote Switch
ssh-server
e Ethernet
Server
Local Switch
Local Ethernet
WAN
Server
PC
SSH-Client
PC
Laptop
Laptop
Local Switch
Local Ethernet
WAN
Server
PC
SSH-Client
PC
Laptop
Laptop
PC
Laptop
Workstation
Remot
Remote Switch
ssh-server
Workstation
Laptop
e Ethernet
Server
Figure 1-2 Establish SSH channels through WAN
The communication process between the server and client includes these five stages:
1) Version negotiation stage. These operations are completed at this stage:
z The client sends TCP connection requirement to the server.
z When TCP connection is established, both ends begin to negotiate the SSH
version.
z If they can work together in harmony, they enter the key algorithm negotiation
stage. Otherwise the server clears the TCP connection.
2) Key algorithm negotiation stage. These operations are completed at this stage:
z The server sends the public key in a randomly generated RSA key pair to the
client.
z The client figures out session key based on the public key from the server and the
random number generated locally.
z The client encrypts the random number with the public key from the server and
sends the result back to the server.
z The server then decrypts the received data with the server private key to get the
client random number.
z The server then uses the same algorithm to work out the session key based on
server public key and the returned random number.
Then both ends get the same session key without data transfer over the network, while
the key is used at both ends for encryption and decryption.
3) Authentication method negotiation stage. These operations are completed at this
stage:

 Loading...
Loading...











