SensusRF gateway user manual
| 29/10/2019
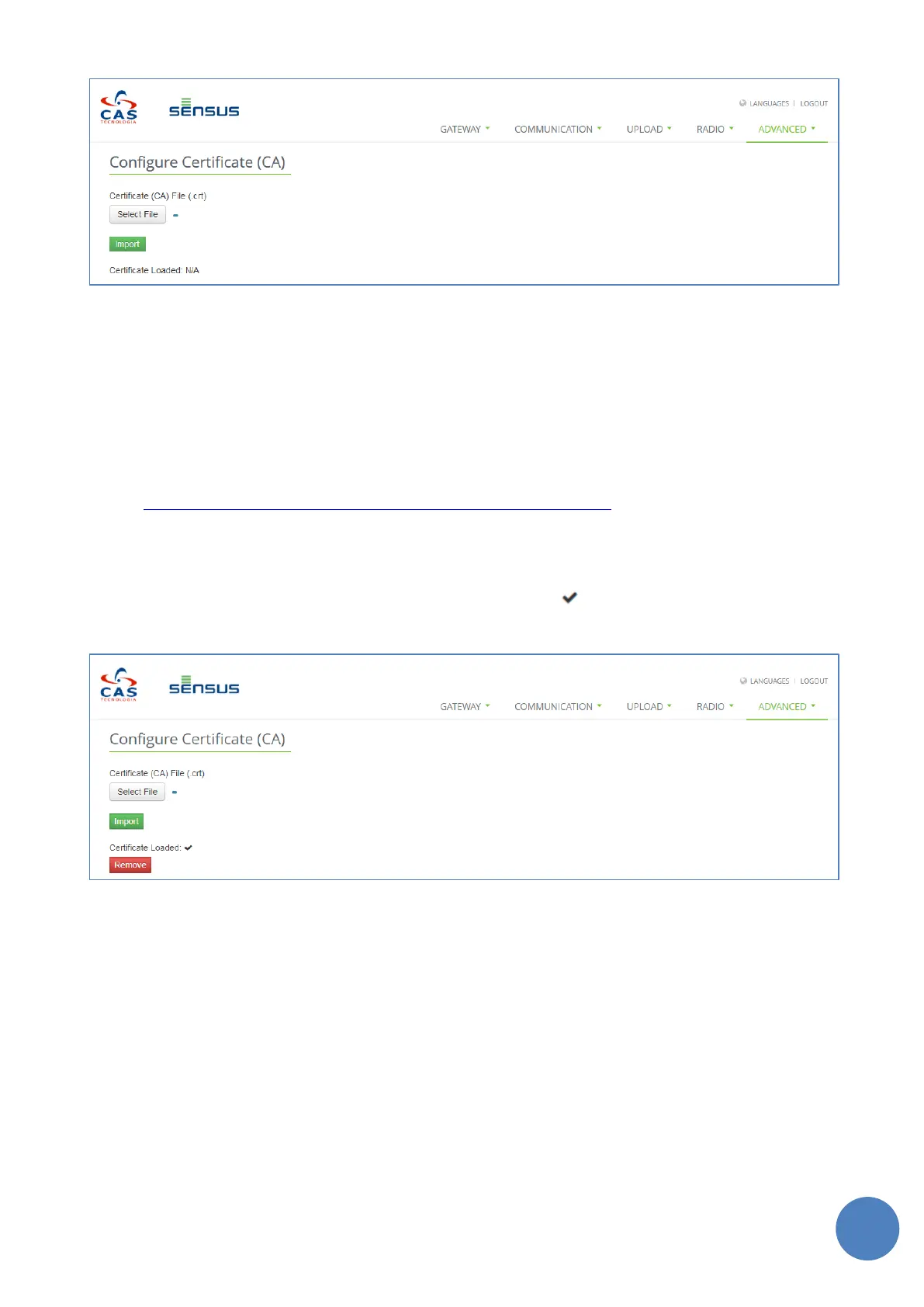
FIGURE 13-24 – TWO-FACTOR AUTHENTICATION
To enable this feature, a server and client certificates pair will be needed:
• Server certificate: A private root certification authority (CA) is required for the Gateway.
• Client certificate: A self signed client certificate (signed by the private CA above) is required for the
client web browser.
• For server and client certificates example, please visit the site
https://schnouki.net/post/2014/lighttpd-and-ssl-client-certificates/
The CA certificate (.crt) will be loaded in the gateway and the client certificate (.p12) will be loaded in client
web browser. Please, refer to your web browser user docummentation to see how to load a client certificate.
When configured, the “Certificate Loaded”filed will display the icon . To unistall the ceertificate from the
Gateway and disable the Two-factor Authentication, click the “Remove” button.
FIGURE 13-25 – TWO-FACTOR AUTHENTICATION ENABLED
IMPORTANT:
• Once enabled Two-factor Authentication, only browsers that have the proper client certificate will
be allowed to access the gateway web page over HTTPS.
• Insecure HTTP access will be disable and only HTTPS will be allowed on all interfaces (Ethernet, PPP
and USB), regardless the firewall configuration.
• If the server CA + client certificate pair is wrong or the client certificate is lost, the gateway web page
access will be lost. There is no tool or method available for end-users (customers) to undo this
configuration. Only an engineering factor reset will be able to recover the Gateway and all local data
and configurtion will be lost.
 Loading...
Loading...