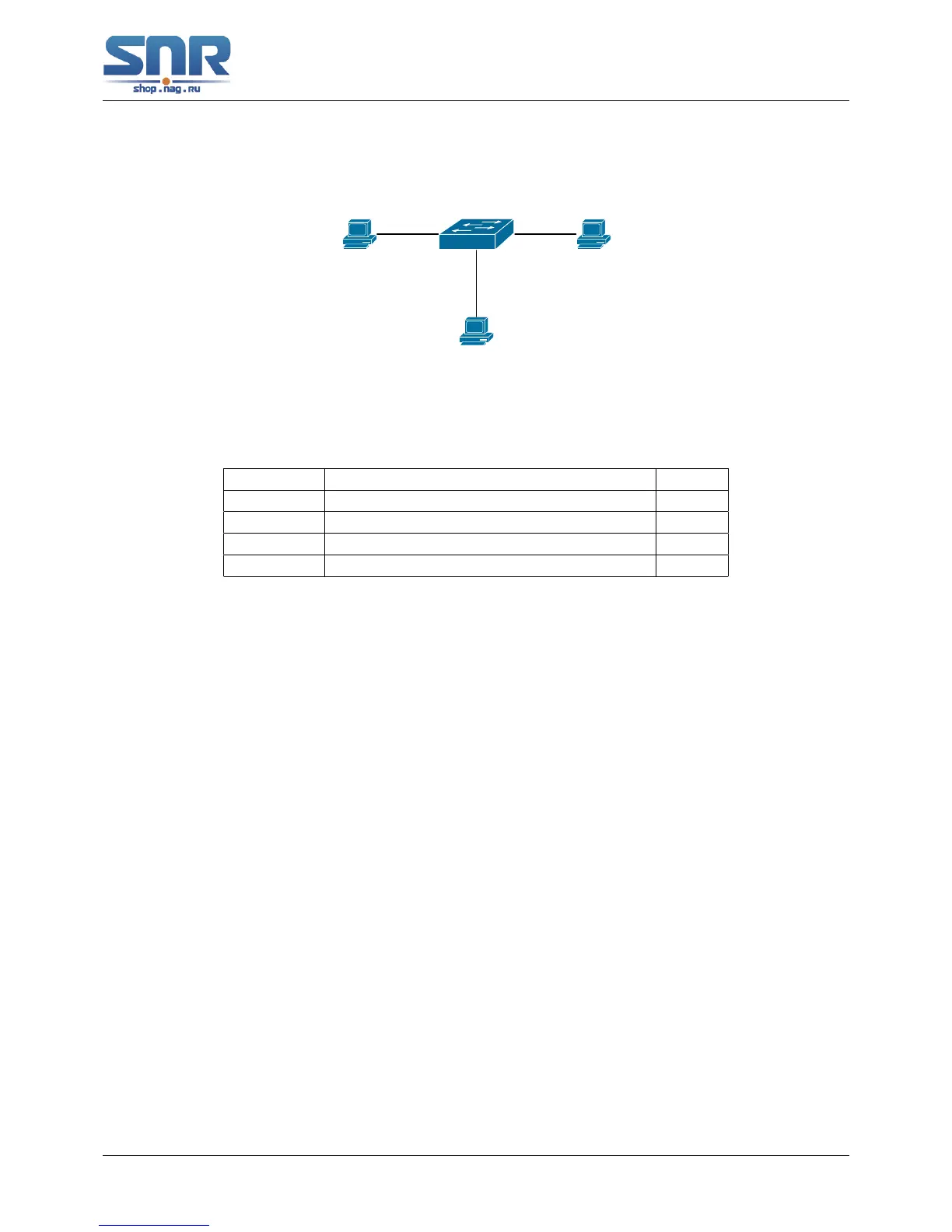
Figure 31.1: Prevent ARP spoofing configuration example
Equipment Explanation
Equipment Configuration Quality
switch IP:192.168.2.4; mac: 00-00-00-00-00-04 1
A IP:192.168.2.1; mac: 00-00-00-00-00-01 1
B IP:192.168.1.2; mac: 00-00-00-00-00-02 1
C IP:192.168.2.3; mac: 00-00-00-00-00-03 some
There is a normal communication between B and C on above diagram. A wants switch to
forward packets sent by B to itself, so need switch sends the packets transfer from B to A. firstly A
sends ARP reply packet to switch, format is: 192.168.2.3, 00-00-00-00-00-01, mapping its MAC
address to C's IP, so the switch changes IP address when it updates ARP list., then data packet
of 192.168.2.3 is transferred to 00-00-00-00-00-01 address (A MAC address).
In further, a transfers its received packets to C by modifying source address and destination
address, the mutual communicated data between B and C are received by A unconsciously. Be-
cause the ARP list is update timely, another task for A is to continuously send ARP reply packet,
and refreshes switch ARP list.
So it is very important to protect ARP list, configure to forbid ARP learning command in sta-
ble environment, and then change all dynamic ARP to static ARP, the learned ARP will not be
refreshed, and protect for users.
Switch(config)#interface vlan 1
Switch(Config-If-Vlan1)#arp 192.168.2.1 00-00-00-00-00-01 interface eth 1/0/2
Switch(Config-If-Vlan1)#interface vlan 2
Switch(Config-If-Vlan2)#arp 192.168.1.2 00-00-00-00-00-02 interface eth 1/0/2
Switch(Config-If-Vlan2#interface vlan 3
Switch(Config-If-Vlan3)#arp 192.168.2.3 00-00-00-00-00-03 interface eth 1/0/2
Switch(Config)#ip arp-security learnprotect
Switch(config)#ip arp-security convert
If the environment changing, it enable to forbid ARP refresh, once it learns ARP property, it
wont be refreshed by new ARP reply packet, and protect use data from sniffing.
Switch#config
Switch(config)#ip arp-security updateprotect
213

 Loading...
Loading...