First we include all of the libraries we need, and we define constants for the
PIR sensor pin and our MAC address. Then we define
SmtpService
and
PassiveIn-
fraredSensor
objects and use them to define a
BurglarAlarm
instance. Note that we
pass a username and a password, implying that we’re using an authenticated
SMTP connection to send our emails. If you use an unauthenticated connec-
tion, you can safely remove the
USERNAME
and
PASSWORD
parameters and all of
their occurrences.
In the
setup
method, we define the serial port and the Ethernet shield. I’ve
also added a delay of twenty seconds, which gives you enough time to leave
the room before the alarm begins to work.
The
loop
function is simple, too. It delegates all the work to
BurglarAlarm
’s
check
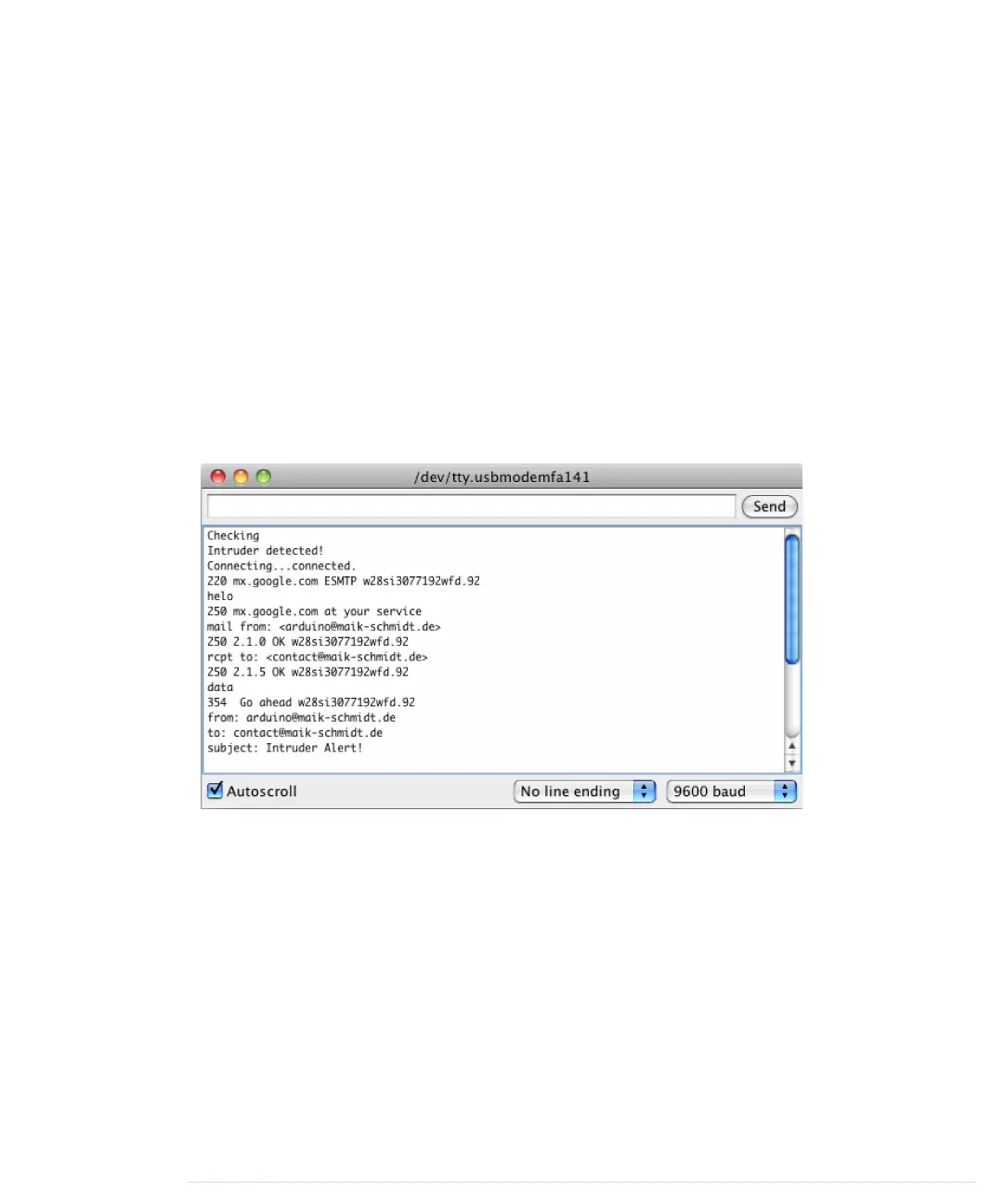
method. In the following figure, you can see what happens when the burglar
alarm detects an intruder.
Did you notice how easy object-oriented programming on an embedded device
can be? We’ve cleanly hidden in two small classes the complexity of both
email and the PIR sensor. To build the burglar alarm, we then only had to
write some glue code.
One word regarding privacy: do not abuse the project in this chapter to observe
other people without their knowledge. Not only is it unethical, but in many
countries it’s even illegal!
In this and the preceding chapter, you learned different ways to connect the
Arduino to the Internet. Some of them require an additional PC, while others
need an Ethernet shield, but they all open the door to a whole new range of
embedded computing applications.
report erratum • discuss
Bringing It All Together • 199
www.it-ebooks.info

 Loading...
Loading...