5.3 VPN
5.3.1 L2TP INTRODUCTION
ADVANCED SETUP >VPN>L2TP
Layer 2 Tunnelling Protocol (L2TP) is a tunnelling protocol used to support virtual private networks
(VPNs). It does not provide any encryption or confidentiality by itself; it relies on an encryption
protocol that it passes within the tunnel to provide privacy.
The entire L2TP packet, including payload and L2TP header, is sent within a UDP datagram. It is
common to carry Point-to-Point Protocol (PPP) sessions within an L2TP tunnel. L2TP does not
provide confidentiality or strong authentication by itself. IPsec is often used to secure L2TP packets
by providing confidentiality, authentication and integrity. The combination of these two protocols is
generally known as L2TP/IPsec.
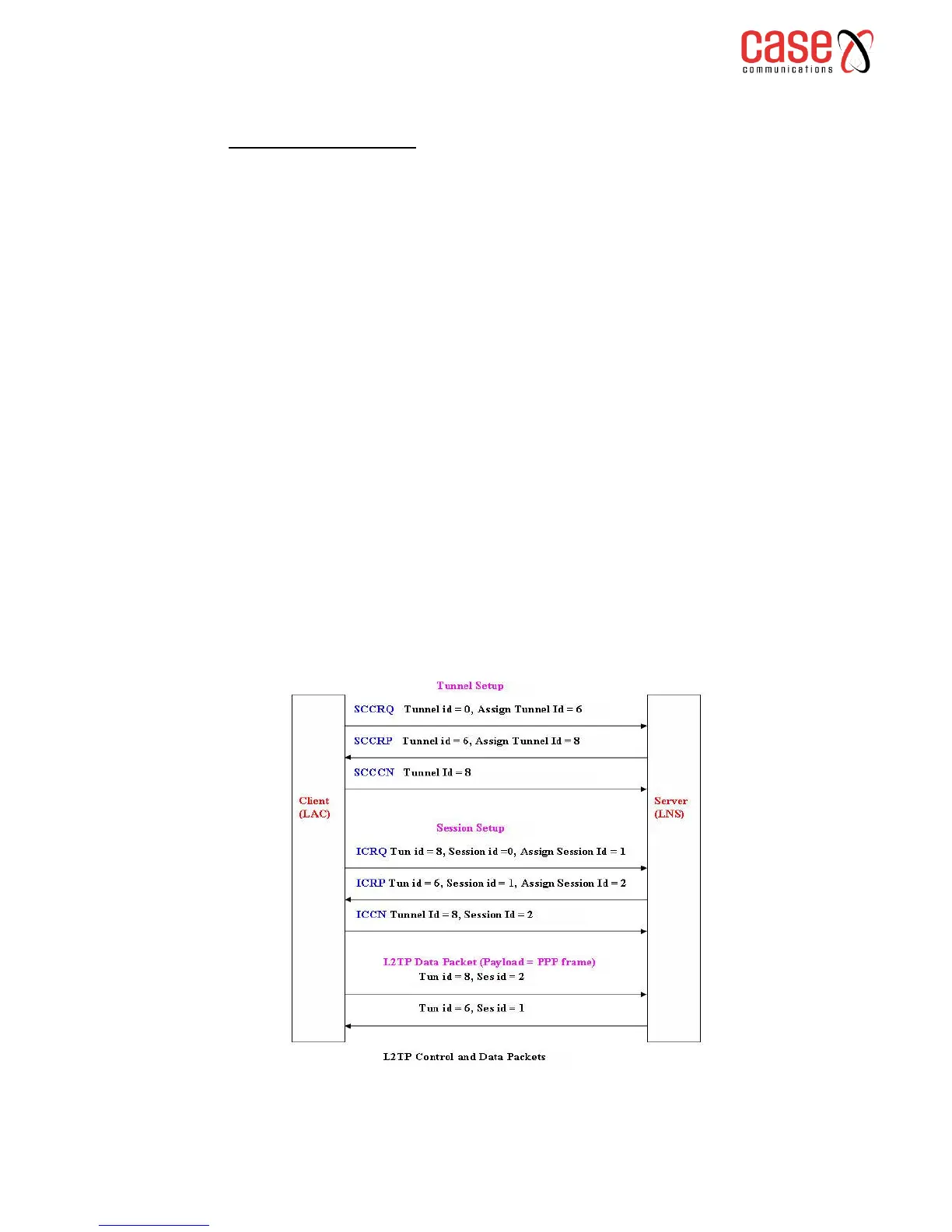
The two endpoints of an L2TP tunnel are called the LAC (L2TP Access Concentrator) and the LNS
(L2TP Network Server). The LAC is the initiator of the tunnel while the LNS is the server, which
waits for new tunnels. Once a tunnel is established, the network traffic between the peers is
bidirectional. To be useful for networking, higher-level protocols are then run through the L2TP
tunnel. To facilitate this, an L2TP session (or call) is established within the tunnel for each higher-
level protocol such as PPP. Either the LAC or LNS may initiate sessions. The traffic for each session
is isolated by L2TP, so it is possible to set up multiple virtual networks across a single tunnel.
The packets exchanged within an L2TP tunnel are categorised as either control packets or data
packets. L2TP provides reliability features for the control packets, but no reliability for data packets.
 Loading...
Loading...