Label Distribution Protocol
Page 248 7210 SAS M, T, X, R6, Mxp MPLS Configu-
ration Guide
The path by way of R2 and R4 can be used to protect against the failure of router R3. However,
with the link R2-R3 metric set to 5, R2 sees the same cost to forward a packet to R5 by way of R3
and R4. Thus R1 cannot guarantee that enabling the LFA next-hop R2 will protect against R3 node
failure. This means that the LFA next-hop R2 provides link-protection only for prefix R5. If the
metric of link R2-R3 is changed to 8, then the LFA next-hop R2 provides node protection since a
packet to R5 will always go over R4. In other words it is required that R2 becomes loop-free with
respect to both the source node R1 and the protected node R3.
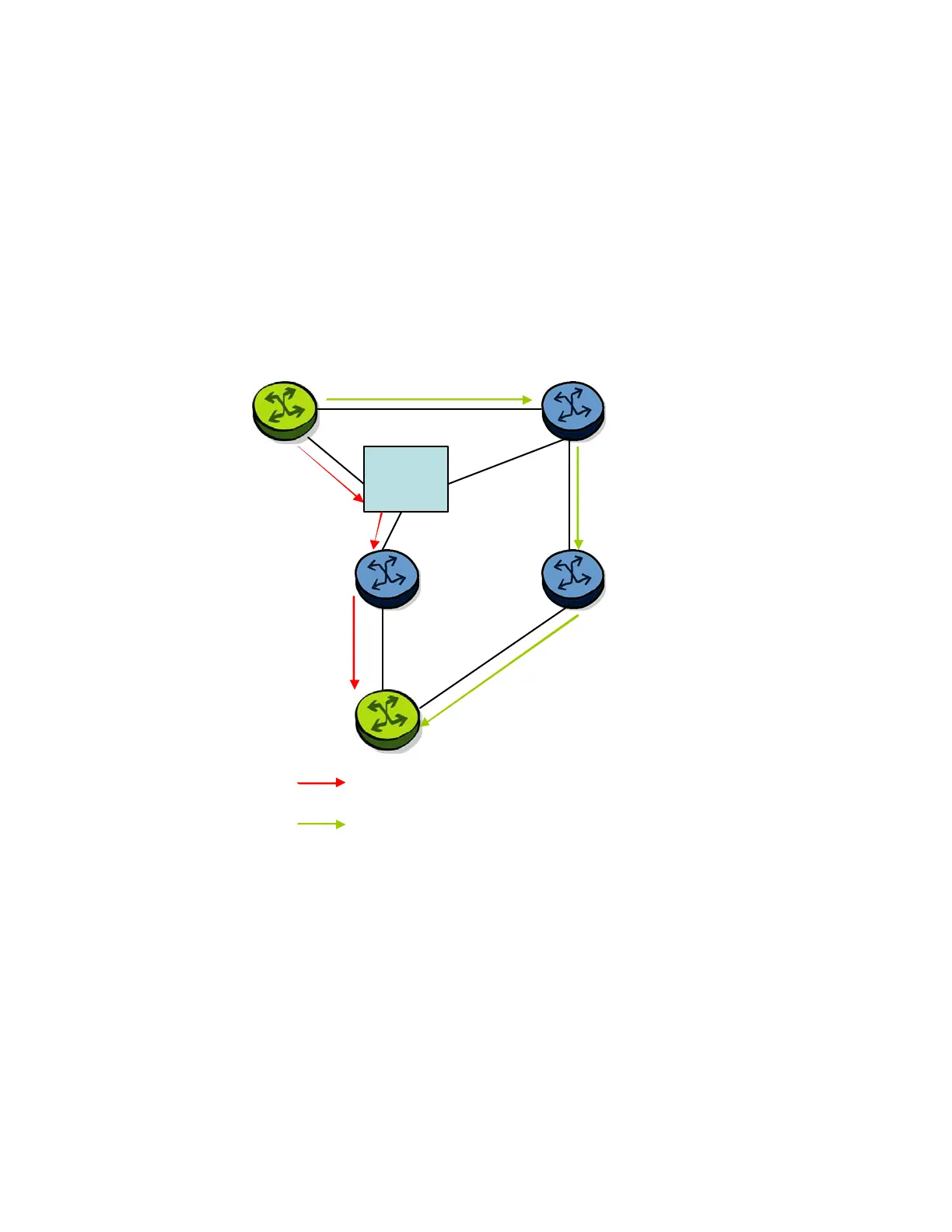
Consider the case where the primary next-hop uses a broadcast interface as illustrated in Figure 28
Figure 28: Example Topology with Broadcast Interfaces
In order for next-hop R2 to be a link-protect LFA for route R5 from R1, it must be loop-free with
respect to the R1-R3 link’s Pseudo-Node (PN). However, since R2 has also a link to that PN, its
cost to reach R5 by way of the PN or router R4 are the same. Thus R1 cannot guarantee that
enabling the LFA next-hop R2 will protect against a failure impacting link R1-PN since this may
cause the entire subnet represented by the PN to go down. If the metric of link R2-PN is changed
to 8, then R2 next-hop will be an LFA providing link protection.
R1 R2
R3 R4
R5
5
5
5
5 (8)
5
5
Primary Route
LFA Link-Protect Route
PN
5

 Loading...
Loading...















