Ping can also be initiated in the Web Interface by going to: Status > Tools > Ping.
Outgoing ICMP messages from the firewall do not require an IP rule which allows them since the
gateway is trusted. However, if the firewall is to be pinged by an external host then an IP rule or
IP policy must be set up to allow this, just as it is needed for IPv4. Such an IP rule or policy would
use the predefined Service object called ping6-inbound The service object called all_icmpv6
covers all IPv6 ICMP messages except mobile ICMP messages.
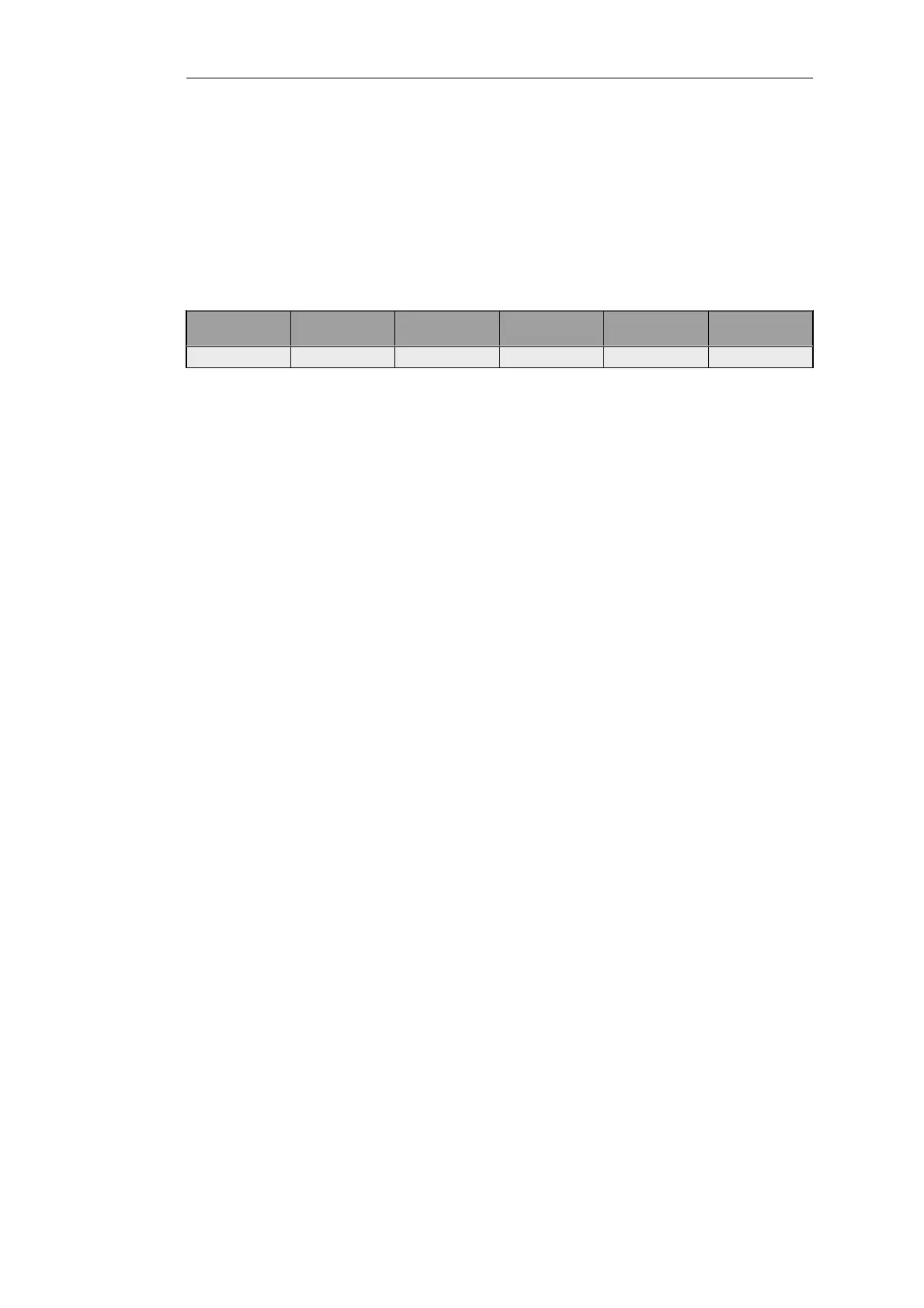
An appropriate IP rule to allow NetDefendOS to respond to IPv6 ping messages would be the
following:
Action Source
Interface
Source
Network
Destination
Interface
Destination
Network
Service
Allow wan all-nets6 core wan_ip6 ping6-inbound
The above rule assumes that IPv6 has been enabled on the wan interface.
IPv6 Usage Restrictions
The following is a summary of IPv6 restrictions in the current version of NetDefendOS:
• Management access with any NetDefendOS management interface is not possible using IPv6.
• IP rules using IPv4 and IPv6 addresses can coexist in the same IP rule set but a single rule
cannot combine IPv4 and IPv6.
• IPv6 addresses are not currently supported in IP rules with the following actions:
i. NAT
ii. SAT
iii. SLB SAT
iv. Multiplex SAT
• Routes using IPv4 and IPv6 addresses can coexist in the same routing table set but a single
route cannot combine IPv4 and IPv6.
• Routing rules using IPv4 and IPv6 addresses coexist but a single rule cannot combine IPv4
and IPv6.
• IPv6 cannot be used with the following:
i. VPN.
ii. IDP.
iii. Traffic shaping (pipes and pipe rules).
iv. Most ALGs. The HTTP and LW-HTTP ALGs do support IPv6.
IPv6 and High Availability
NetDefendOS High Availability (HA) fully supports IPv6 and any IPv6 configuration objects will be
mirrored on both the HA master and slave units.
The address book object IP6 HA Address is the IPv6 equivalent of the IP4 HA Address object. This
allows both shared and private IPv6 addresses to be assigned to interface pairs in an HA cluster.
Chapter 3: Fundamentals
162
 Loading...
Loading...