• Set up the IP Rule objects to allow traffic flow in either direction.
• Set up the Route in the main routing table (or another table if an alternate is being used).
• Set up the peer at the other end of the tunnel in a similar way. The local and remote networks
are reversed.
Example 9.4. PSK Based LAN-to-LAN IPsec Tunnel Setup
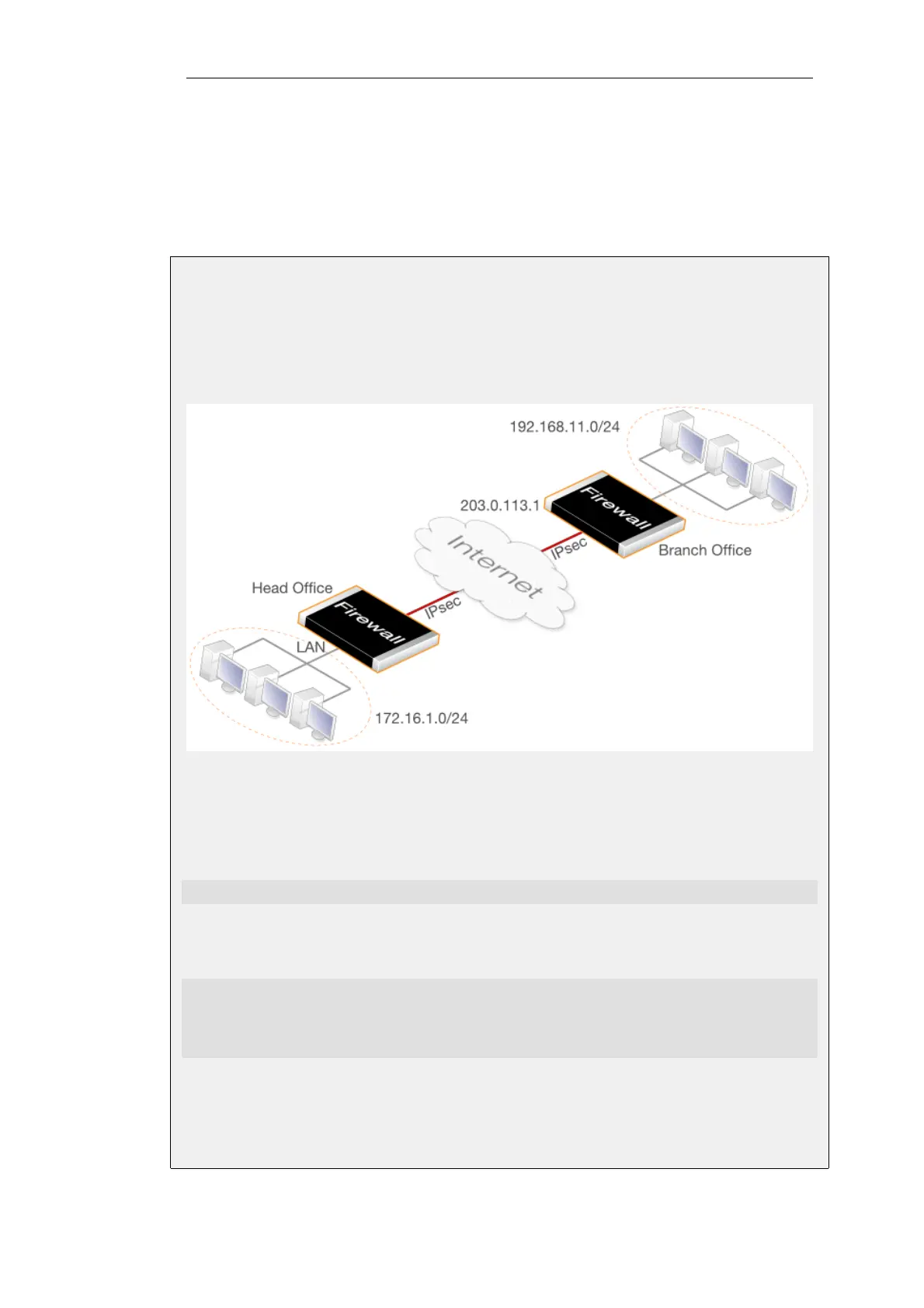
This example describes how to configure an IPsec tunnel across the public Internet to connect
the head office network 172.16.1.0/24 on the lan interface with a branch office network
192.168.11.0/24. Assume that the branch office firewall Ethernet interface connected to the
Internet has the public IP address 203.0.113.1.
It is assumed the default IKE and IPsec proposal list are used at either end of the tunnel.
Command-Line Interface
A. Create a pre-shared key for IPsec authentication:
gw-world:/> add PSK my_scecret_key Type=ASCII PSKascii=somesecretasciikey
B. Configure the IPsec tunnel:
gw-world:/> add Interface IPsecTunnel ipsec_hq_to_branch
LocalNetwork=172.16.1.0/24
RemoteNetwork=192.168.11.0/24
RemoteEndpoint=203.0.113.1
PSK=my_secret_key
C. Configure 2 IP rules to allow traffic flow both ways in the tunnel:
i. Add an IP rule to allow traffic to flow from local to remote network:
Chapter 9: VPN
705
 Loading...
Loading...