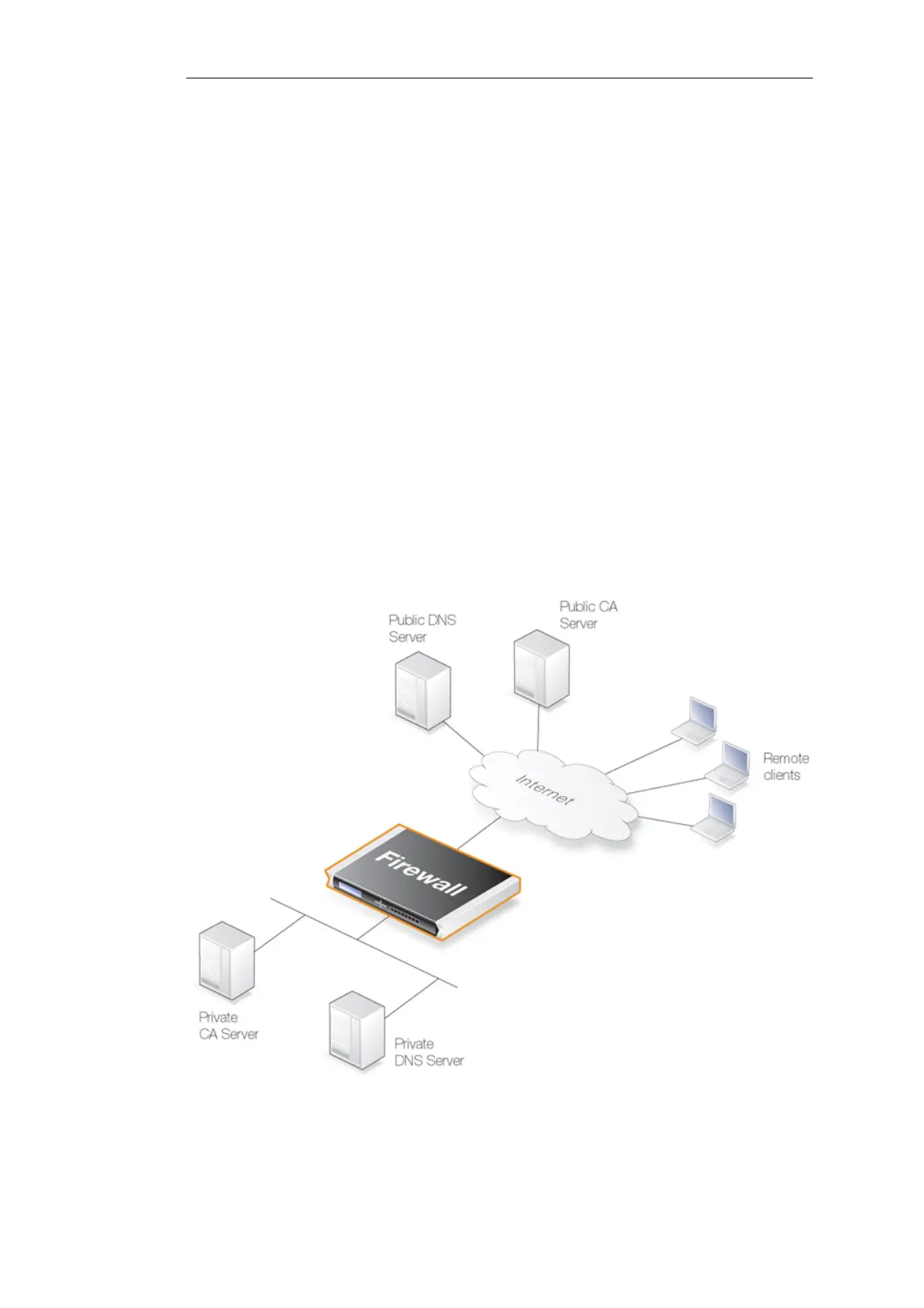
b. The external IP address of the NetDefend Firewall needs to be registered in the
public DNS system so that the FQDN reference to the private CA server in
certificates sent to clients can be resolved. For example, NetDefendOS may send a
certificate to a client with an FQDN which is ca.example.com and this will need to be
resolvable by the client to a public external IP address of the NetDefend Firewall
through the public DNS system.
The same steps should be followed if the other side of the tunnel is another firewall
instead of being many clients.
3. The CA server is a commercial server on the public Internet. In this, the simplest case,
public DNS servers will resolve the FQDN. The only requirement is that NetDefendOS will
need to have at least one public DNS server address configured to resolve the FQDNs in
the certificates it receives.
• It must be also possible for an HTTP PUT request to pass from the validation request source
(either the NetDefend Firewall or a client) to the CA server and an HTTP reply to be received.
If the request is going to pass through the NetDefend Firewall, the appropriate rules in the
NetDefendOS IP rule set need to be defined to allow this traffic through.
IP rules are not required if it NetDefendOS itself that is issuing the request to the CA server.
Actions taken by NetDefendOS are trusted by default. This is a general rule that also applies
to DNS resolution requests issued by NetDefendOS.
Figure 3.13. Certificate Validation Components
Chapter 3: Fundamentals
278
 Loading...
Loading...