67
<Switch> ping 192.168.1.58
Permission denied.
RBAC configuration example for RADIUS authentication
users
Network requirements
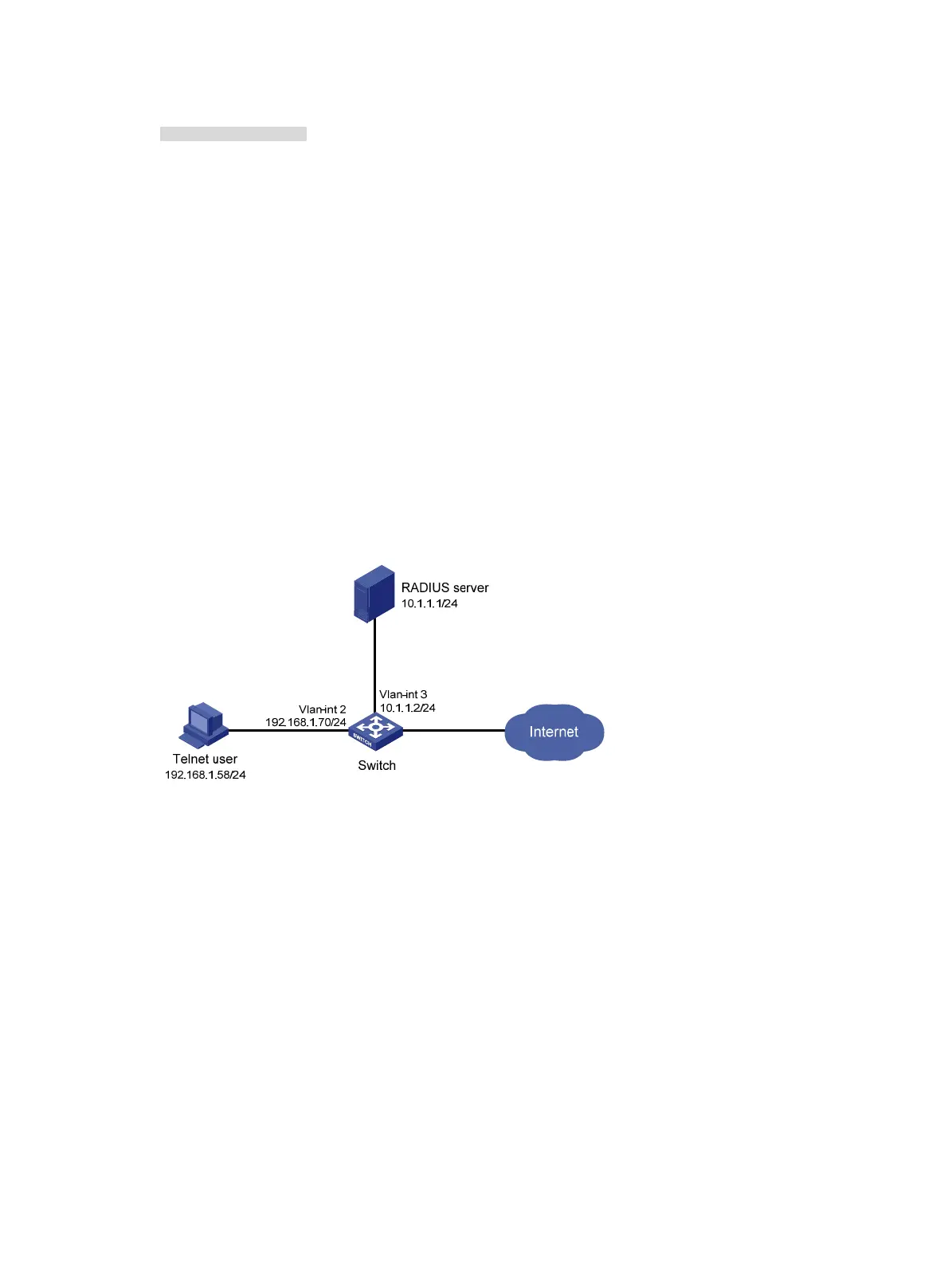
As shown in Figure 22, the switch uses the FreeRADIUS server to provide AAA service for login
users, including the Telnet user. The user account for the Telnet user is hello@bbb and is assigned
the user role role2.
Configure role2 to have the following permissions:
• Can use all commands in ISP view.
• Can use the read and write commands of the arp and radius features.
• Cannot access the read commands of the acl feature.
• Can configure only VLANs 1 to 20 and interfaces GigabitEthernet 1/0/1 to GigabitEthernet
1/0/20.
The switch and the FreeRADIUS server use the shared key expert and authentication port 1812.
The switch delivers usernames with their domain names to the server.
Figure 22 Network diagram
Configuration procedure
Make sure the settings on the switch and the RADIUS server match.
1. Configure the switch:
# Assign VLAN-interface 2 an IP address from the same subnet as the Telnet user.
<Switch> system-view
[Switch] interface vlan-interface 2
[Switch-Vlan-interface2] ip address 192.168.1.70 255.255.255.0
[Switch-Vlan-interface2] quit
# Assign VLAN-interface 3 an IP address from the same subnet as the RADIUS server.
[Switch] interface vlan-interface 3
[Switch-Vlan-interface3] ip address 10.1.1.2 255.255.255.0
[Switch-Vlan-interface3] quit
# Enable Telnet server.
[Switch] telnet server enable
# Enable scheme authentication on the user lines for Telnet users.
[Switch] line vty 0 63

 Loading...
Loading...














