Chapter 13. Encryption 755
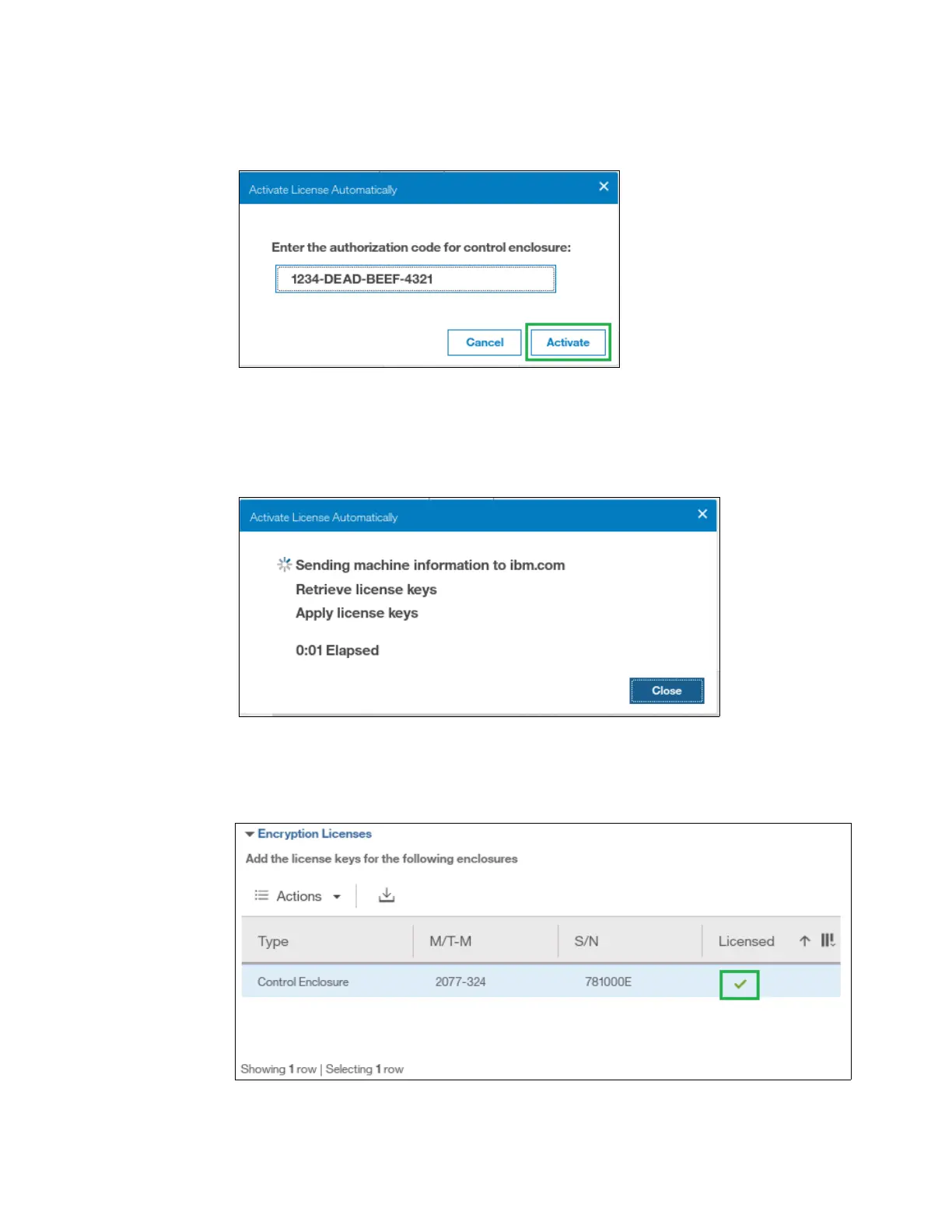
2. Enter the authorization code that is specific to the node that you selected, as shown in
Figure 13-13. You can now click Activate.
Figure 13-13 Entering an authorization code
3. The system connects to IBM to verify the authorization code and retrieve the license key.
Figure 13-14 shows a window which is displayed during this connection. If everything
works correctly, the procedure takes less than a minute.
Figure 13-14 Activating encryption
4. After the license key has been retrieved, it is automatically applied as shown in
Figure 13-15.
Figure 13-15 Successful encryption license activation

 Loading...
Loading...











