Chapter 13. Encryption 759
Support for simultaneous use of both USB flash drives and a key server is available in IBM
Spectrum Virtualize code V8.1 and later. Organizations that use encryption key management
servers might consider parallel use of USB flash drives as a backup solution. During normal
operation such drives could be disconnected and stored in a secure location. However, in the
event of a catastrophic loss of encryption servers, the USB drives could still be used to unlock
the encrypted storage.
The following list of key server and USB flash drive characteristics might help you to choose
the type of encryption key provider that you want to use.
Key servers can have the following characteristics:
Physical access to the system is not required to perform a rekey operation.
Support for businesses that have security requirements precluding use of USB ports.
Possibility to use Hardware Security Modules (HSMs) for encryption key generation.
Ability to replicate keys between servers and perform automatic backups.
Implementations follow an open standard (KMIP) that aids in interoperability.
Ability to audit operations related to key management.
Ability to separately manage encryption keys and physical access to storage systems.
USB flash drives have the following characteristics:
Physical access to the system might be required to process a rekey operation.
No moving parts with almost no read or write operations to the USB flash drive.
Inexpensive to maintain and use.
Convenient and easy to have multiple identical USB flash drives available as backups. You
can just copy them if needed.
13.4.1 Starting the Enable Encryption wizard
After the license activation step is successfully completed, you can now enable encryption.
You can enable encryption after completion of the initial system setup using either GUI or CLI.
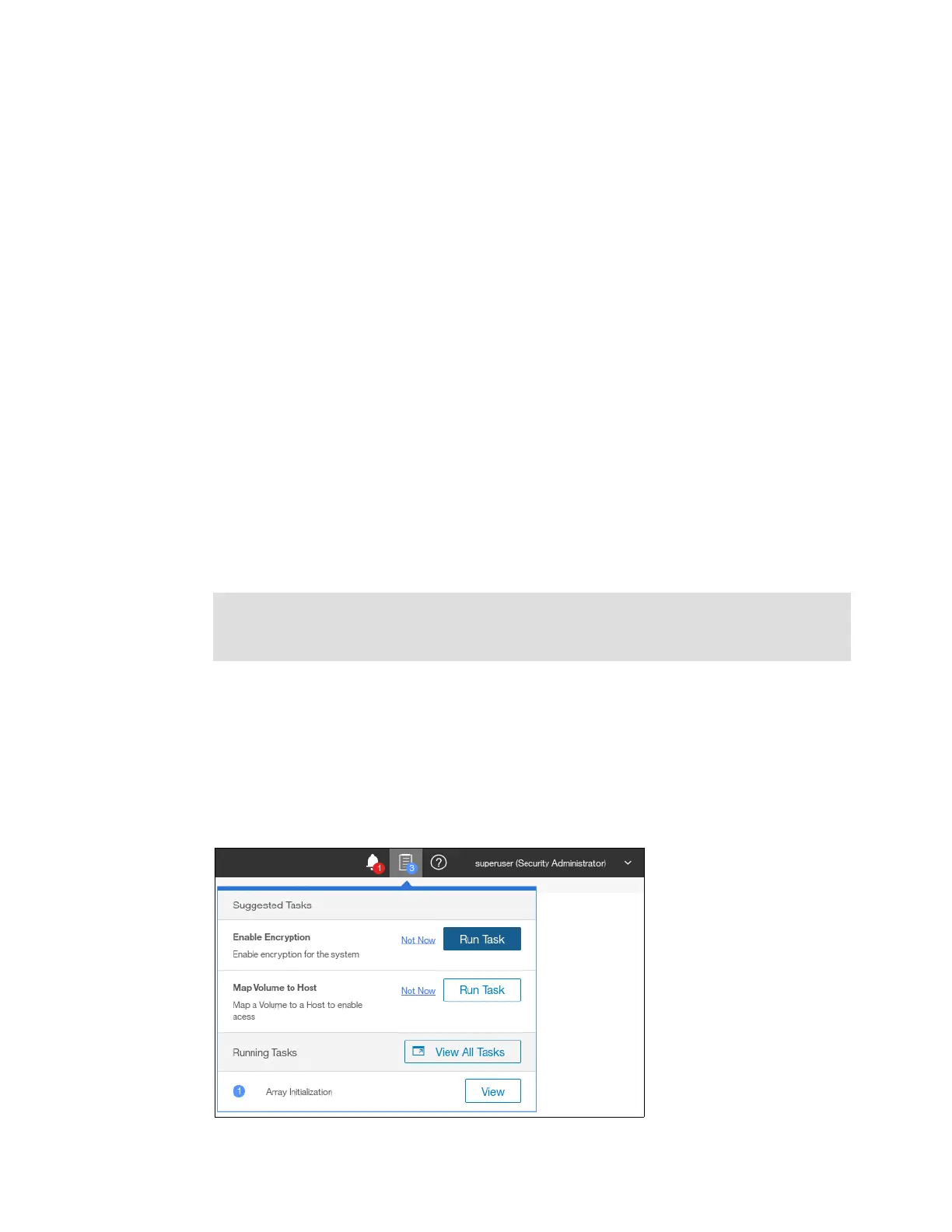
There are two ways in the GUI to start the Enable Encryption wizard. It can be started by
clicking Run Task button next to Enable Encryption on the Suggested Tasks window as
shown in Figure 13-21.
Figure 13-21 Enable Encryption from the Suggested Tasks window
Important: Maintaining confidentiality of the encrypted data hinges on security of the
encryption keys. Pay special attention to ensuring secure creation, management and
storage of the encryption keys.

 Loading...
Loading...











