Basic System Configuration Guide Boot Options
Edition: 01 3HE 11010 AAAC TQZZA 145
5.1.3.1 CSM and Data Path Security Features and Algorithms in
FIPS-140-2 Mode
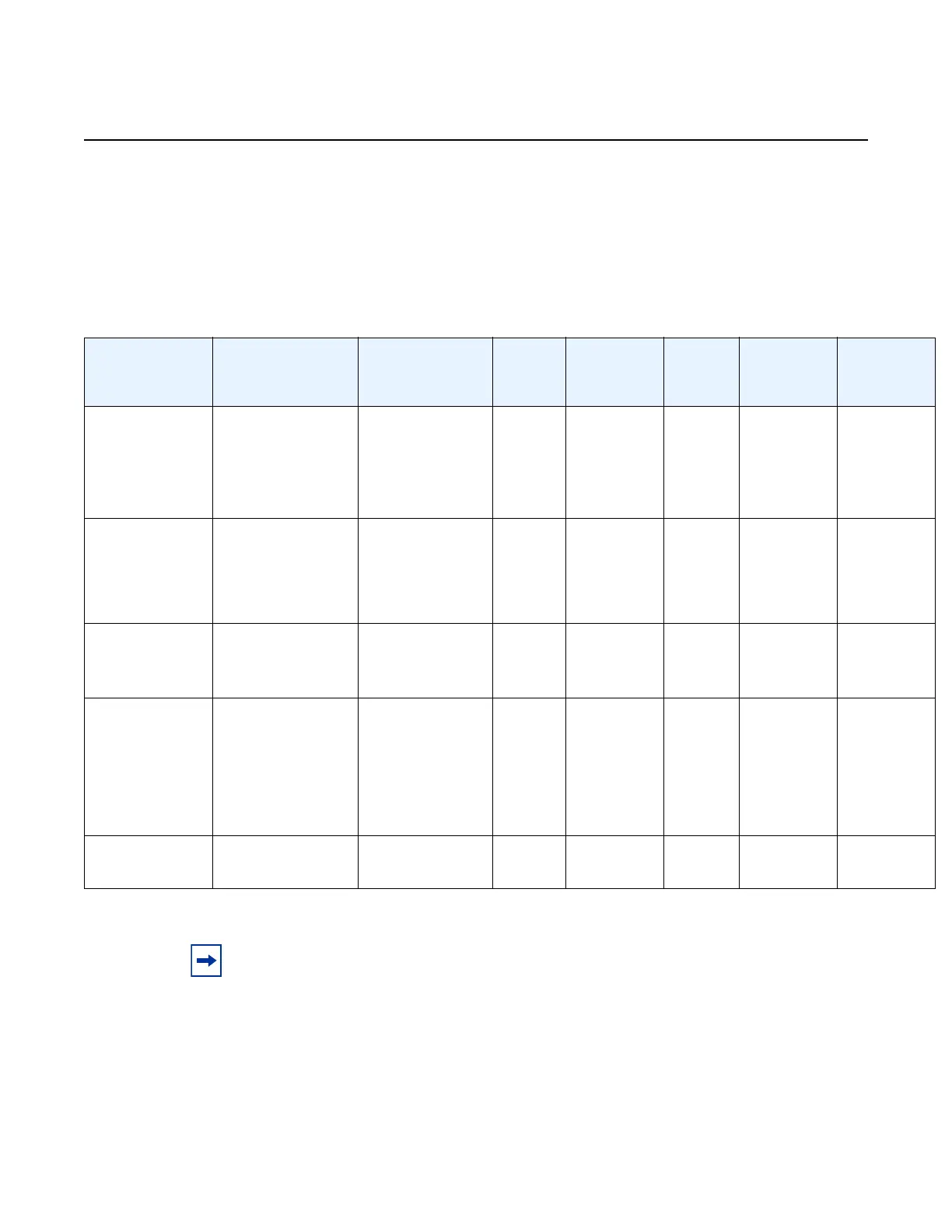
Table 19 and Table 20 show the CSM and data path security features and
associated algorithms for a 7705 SAR node running in FIPS-140-2 mode.
Table 19 CSM Algorithms
FIPS-140-2
CSM
Algorithms
SSH2 IPSec (IKEv1,
IKEv2)
NGE SNMPv3 SCP,
SFTP
IGP,
BGP,
MPLS
PKI
Authentication RSA 2048
DSA 1024
Preference to
RSA in SSH
negotiation
PSK
(DH G14,
DHG 15)
SSH N/A SSH N/A N/A
Asymmetric
Key
DH G14
(P ≥ 2K prime
numbers,
q > 224)
DH G14,
DHG 15
(P ≥ 2K prime
numbers,
q > 224)
SSH N/A SSH N/A RSA/
DSA 2048
Symmetric
Key
AES-CBC
(128,192, 256)
3DES-CBC
AES-CBC
(128,192, 256)
3DES-CBC
N/A AES-128 SSH N/A N/A
Hash
Algorithm
SHA-1 (128)
–HMAC-MD5
–HMAC-RIPEMD-
160
–HMAC-SHA1-96
–HMAC-MD5-96
SHA-1 (128)
SHA-2
(256, 384, 512)
N/A SHA-1
(SHA-128)
SSH SHA-1
(128)
SHA-2
(256)
AES-18-
CMAC-96
SHA1
SHA-224
SHA-256
SHA-384
SHA-512
Digital
Signature
RSA 2048
DSA 1024
N/A N/A N/A N/A N/A RSA/
DSA-2048
Note: MD5 algorithms are not blocked from configuration in FIPS-140-2 mode. Although
MD5 is not a FIPS-140-2-approved algorithm, it is allowed to be used when running in
FIPS-140-2 mode.

 Loading...
Loading...