Managing the Access Policy
Quantum Spark 1500, 1600 and 1800 Appliance Series R80.20.40 Locally Managed Administration Guide | 163
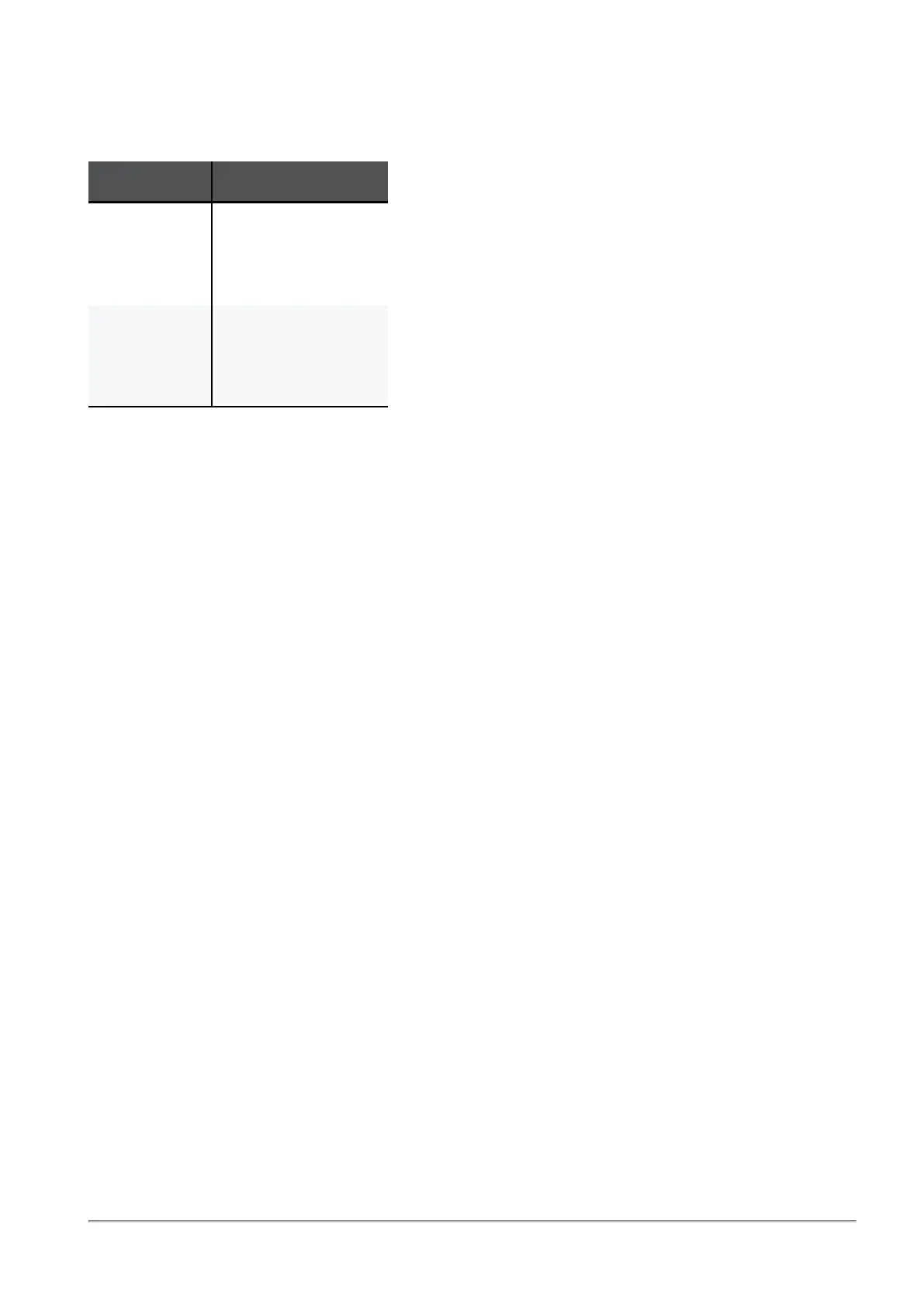
Tracking
Select which traffic to log:
Traffic Log Options
Blocked traffic
n
All
n
Outgoing
n
Incoming and
internal
Allowed traffic
n
All
n
Outgoing
n
Incoming and
internal
These settings apply to all the incoming and outgoing traffic blocked or accepted by the default Firewall and
Application & URL Filtering automatically generated rules.
These settings do not apply to automatically generated rules for VPN, DMZ, and wireless networks.
More Information
The Check Point Application Database contains more than 4,500 applications and about 96 million
categorized URLs.
Each application has a description, a category, additional categories, and a risk level. You can include
applications and categories in your Application Control and URL Filtering rules. If your appliance is licensed
for the Application Control & URL Filtering blades, the database is updated regularly with new applications,
categories and social networking widgets. This lets you easily create and maintain an up to date policy.
You can see the Application Database from:
n
The Block other undesired applications link.
n
The Applications & URLs link - This opens the Users & Objects > Applications & URLs page.
n
The Check Point AppWiki link - The AppWiki is an easy to use tool that lets you search and filter the
Application & URL Filtering Database.

 Loading...
Loading...