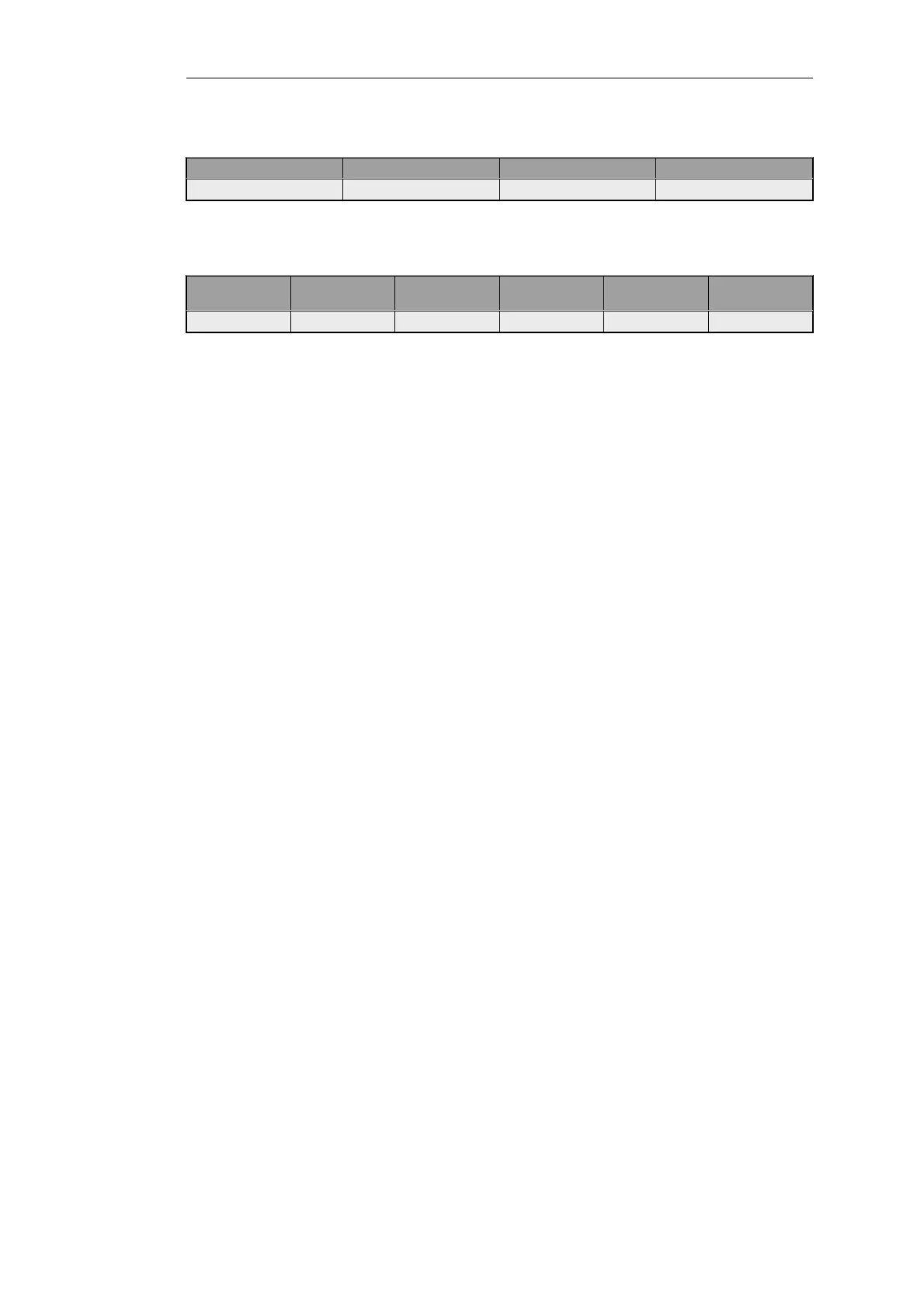
The isp2 routing table
Index # Interface Destination Gateway
1 wan2 all-nets isp2_ip
If traffic coming through wan2 is to have access to If1_net then a routing rule needs to
constructed as follows:
Source
Interface
Source
Network
Destination
Interface
Destination
Network
Forward
Routing Table
Return
Routing Table
wan2 all-nets any If1_net main isp2
This rule allows the forward traffic through the wan2 table to find the route for If1_net in the
main routing table. The return traffic will use the isp2 table so it can reach the initiator of the
connection.
This example should also have some address translation rules since If1_net will probably be a
private IP network. For simplicity, that has been omitted.
Explicit Interface/Routing Table Association
If a particular routing table is to be always used for traffic from a given source interface,
regardless of the service, it is possible to associate the source interface explicitly with a particular
table using the Routing Table Membership property of the interface.
The difference with this method of explicit association is that the administrator cannot specify
the service, such as HTTP, for which the lookup will apply. Routing rules allow a more
fine-grained approach to routing table selection by being able to also select a specific service
and interface/network filter.
The Routing Table Selection Process
When a packet corresponding to a new connection first arrives, these are the processing steps
taken to determine which routing table to use:
1. The routing rules are looked up first. To allow this, the packet’s destination interface must be
determined using an initial route lookup that is always performed in the main routing table.
It is therefore important that a match for the destination network is found. To ensure this, it
is recommended to at least have a default all-nets route which can catch anything not
explicitly matched.
2. A search is now made for a routing rule that matches the packet's source/destination
interface/network as well as service. If a matching rule is found then this determines the
routing table to use. If no routing rule is found then the main table will be used.
3. If no matching routing rule is found, a check is made to see if the receiving interface is a
member of a specific routing table. If the interface is associated with a particular routing
table through its Routing Table Membership property, that routing table will be used. If there
is no membership then the main table will be used.
4. Once the correct routing table has been located, a check is made to make sure that the
source IP address in fact belongs on the receiving interface. The Access Rules are firstly
examined to see if they can provide this check (see Section 6.1, “Access Rules” for more details
of this feature). If there are no Access Rules or a match with the rules cannot be found, a
reverse lookup in the previously selected routing table is done using the source IP address. If
the check fails then a Default access rule log error message is generated.
Chapter 4: Routing
312
 Loading...
Loading...