Contextual help of the web interface – 115
•
•
•
•
•
•
•
•
•
•
•
•
•
6. If Auth is selected on the communication security mechanism, select the Authentication algorithms.
SHA— SHA1 is not recommended as it is not secured.
SHA256—fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
SHA384—fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
SHA512—fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
AES / AES192 / AES256
7. If Priv is selected on the communication security mechanism, select the Privacy algorithms.
AES— fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
AES192—fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
AES256—fill in password and privacy keys. The password can be between 8 and 24 characters and use a combination of
alphanumeric and the following special characters<>&@#%_=:;,./?|$*.
8. Enter your own login password and clickSave.
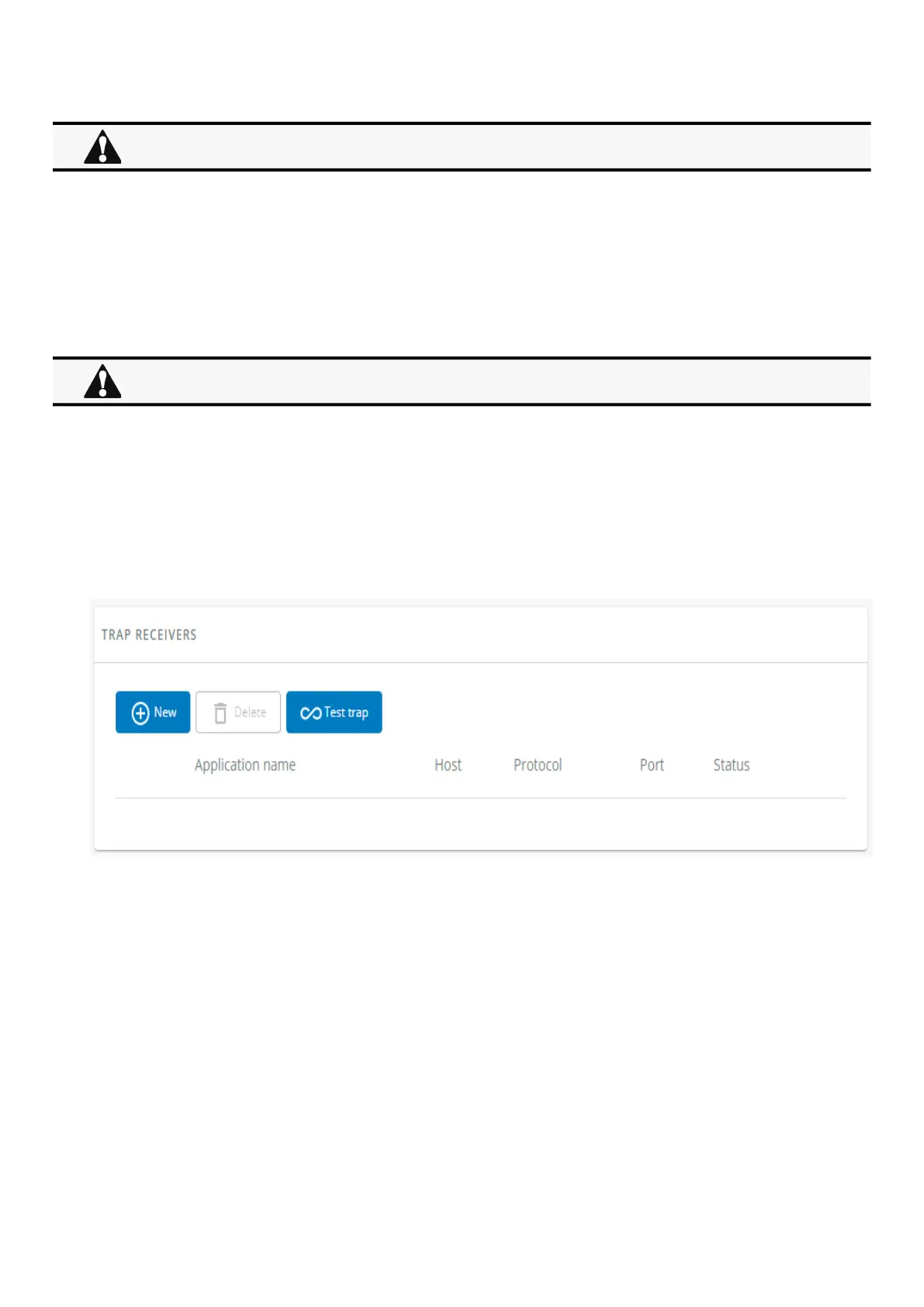
3.7.5.2 Trap receivers
The table shows all the trap receivers and includes the following details:
Application name
Host
Protocol
Port
Status:Active/Inactive/Error(configuration error)
It is recommended to set SHA256/SHA384/SHA512 with the AES192/AES256 Privacy algorithms.
It is recommended to set AES192/AES256 with the SHA256/SHA384/SHA512 Authentication algorithms.
 Loading...
Loading...