Cybersecurity recommended secure hardening guidelines
Securing the Network Management Module – 217
•
•
•
•
•
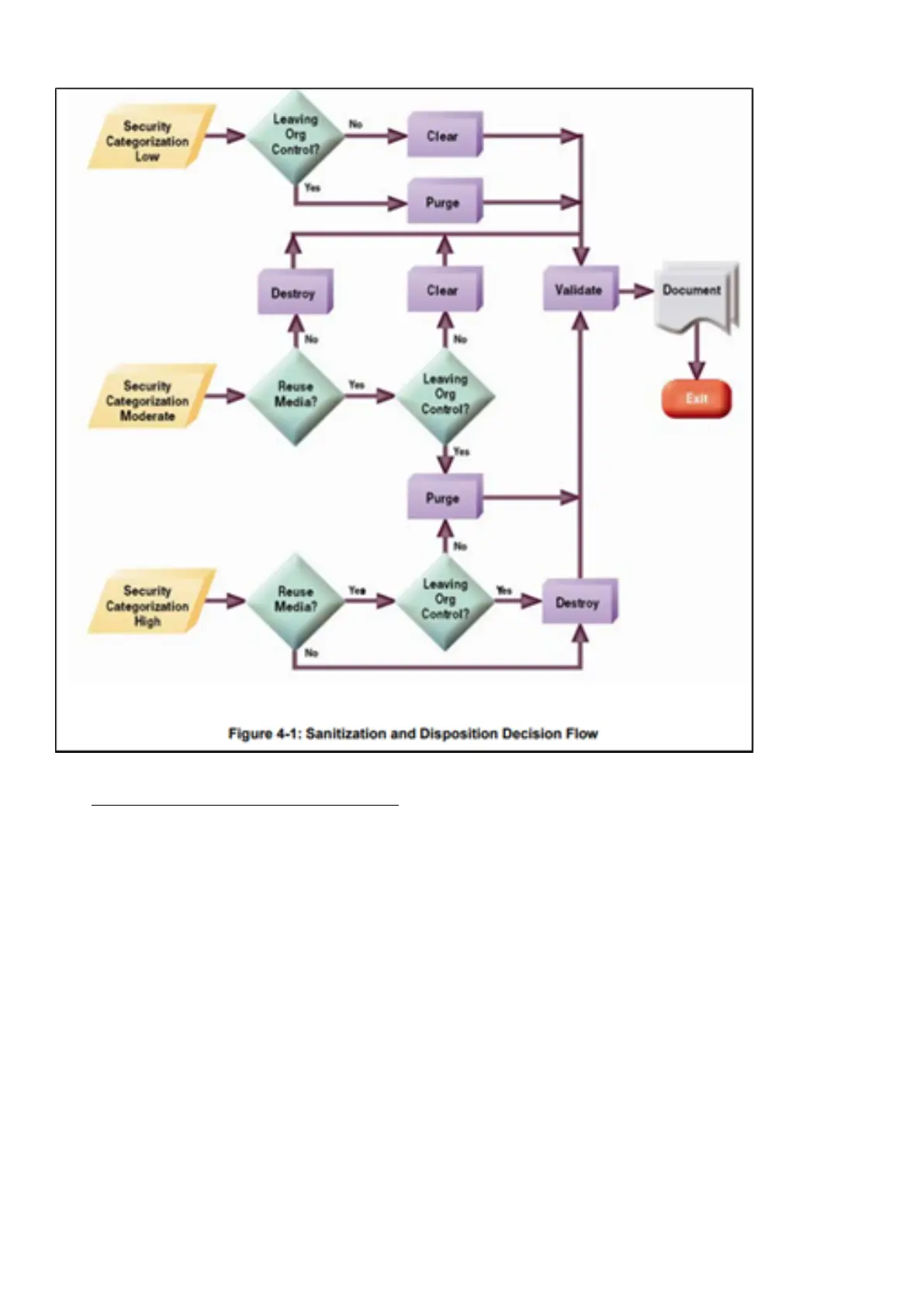
*Figure and data from NIST SP800-88
Embedded Flash Memory on Boards and Devices
Eaton recommends the following methods for disposing of motherboards, peripheral cards such as network adapters, or any
other adapter containing non-volatile flash memory.
Clear: If supported by the device, reset the state to original factory settings.
Navigate toSecuring the Network Management Module>>>Decommissioning the Network Management module.
Purge: If the flash memory can be easily identified and removed from the board, the flash memory may be destroyed
independently of the board that contained the flash memory. Otherwise, the whole board should be destroyed.
For the Network module thewhole board should be destroyed.
Destroy: Shred, disintegrate, pulverize, or Incinerate by burning the device in a licensed incinerator.
5.2.3 References
[R1] Cybersecurity Considerations for Electrical Distribution Systems (WP152002EN):http://www.eaton.com/ecm/groups/public/
@pub/@eaton/@corp/documents/content/pct_1603172.pdf
[R2] Cybersecurity Best Practices Checklist Reminder (WP910003EN):http://www.cooperindustries.com/content/dam/public/
powersystems/resources/library/1100_EAS/WP910003EN.pdf
[R3] NIST SP 800-82 Rev 2, Guide to Industrial Control Systems (ICS) Security, May 2015:https://nvlpubs.nist.gov/nistpubs/
SpecialPublications/NIST.SP.800-82r2.pdf
[R4] National Institute of Technology (NIST) Interagency “Guidelines on Firewalls and Firewall Policy, NIST Special Publication
800-41”, October 2009:http://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-41r1.pdf
 Loading...
Loading...