Manage Device Security
211
S350 Series 8-Port Gigabit Ethernet Smart Managed Pro Switch Models GS308T and GS310TP
2. Launch a web browser.
3. In the address field of your web browser
, enter the IP address of the switch.
If you do not know the IP address of the switch, see Change the Default IP Address of the
Switch on page 11.
Your web browser might display a security message, which you can ignore. For more
information, see Access the Local Browser Interface on page 19.
The login window opens.
4. Enter the switch’
s password in the Password field.
The default password is password.
The System Information page displays.
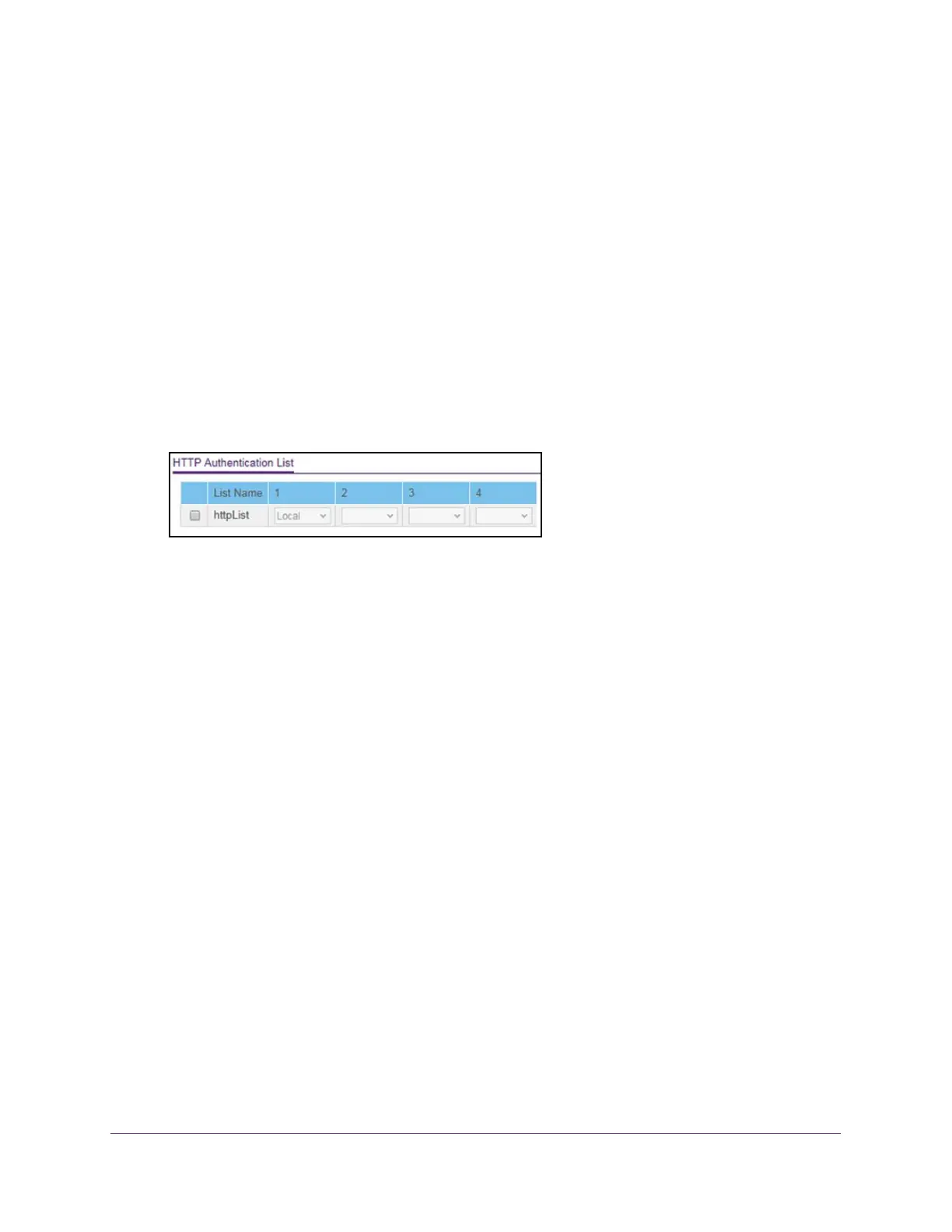
5. Select Security > Management Security >
Authentication List > HTTP Authentication
List.
6. Select the check box next to the httpList name.
7. From the menu in the 1 column, select the authentication method that must be used first in
the selected authentication login list.
If you select a method that does not time out as the first method, such as Local, no other
method is tried, even if you specified more than one method. User authentication occurs
in the order the methods are selected. Possible methods are as follows:
• Local.
The user’s locally stored ID and password are used for authentication. Since
the Local method does not time out, if you select this option as the first method, no
other method is tried, even if you specified more than one method. This is the default
method. This is the default selection for Method 1.
• RADIUS.
The user’s ID and password are authenticated using the RADIUS server. If
you select RADIUS or TACACS+ as the first method and an error occurs during the
authentication, the switch uses Method 2 to authenticate the user.
• T
ACACS+. The user’s ID and password are authenticated using the TACACS+
server. If you select RADIUS or TACACS+ as the first method and an error occurs
during the authentication, the switch attempts user authentication Method 2.
• None.
The authentication method is unspecified, that is, no authentication is required.
8. From the menu in the 2 column, select the authentication method, if any
, that must be used
second in the selected authentication login list.
This is the method that is used if the first method times out. If you select a method that
does not time out as the second method, the third method is not tried.
9. From the menu in the 3 column, select the authentication method, if any
, that must be used
third in the selected authentication login list.

 Loading...
Loading...