Configure the System Web Interface Port Lock
You can limit the number of failed login attempts to the G7500 system web interface to protect against
brute-force attacks.
Procedure
1. In the system web interface, go to Security > Access.
2. Configure the following settings:
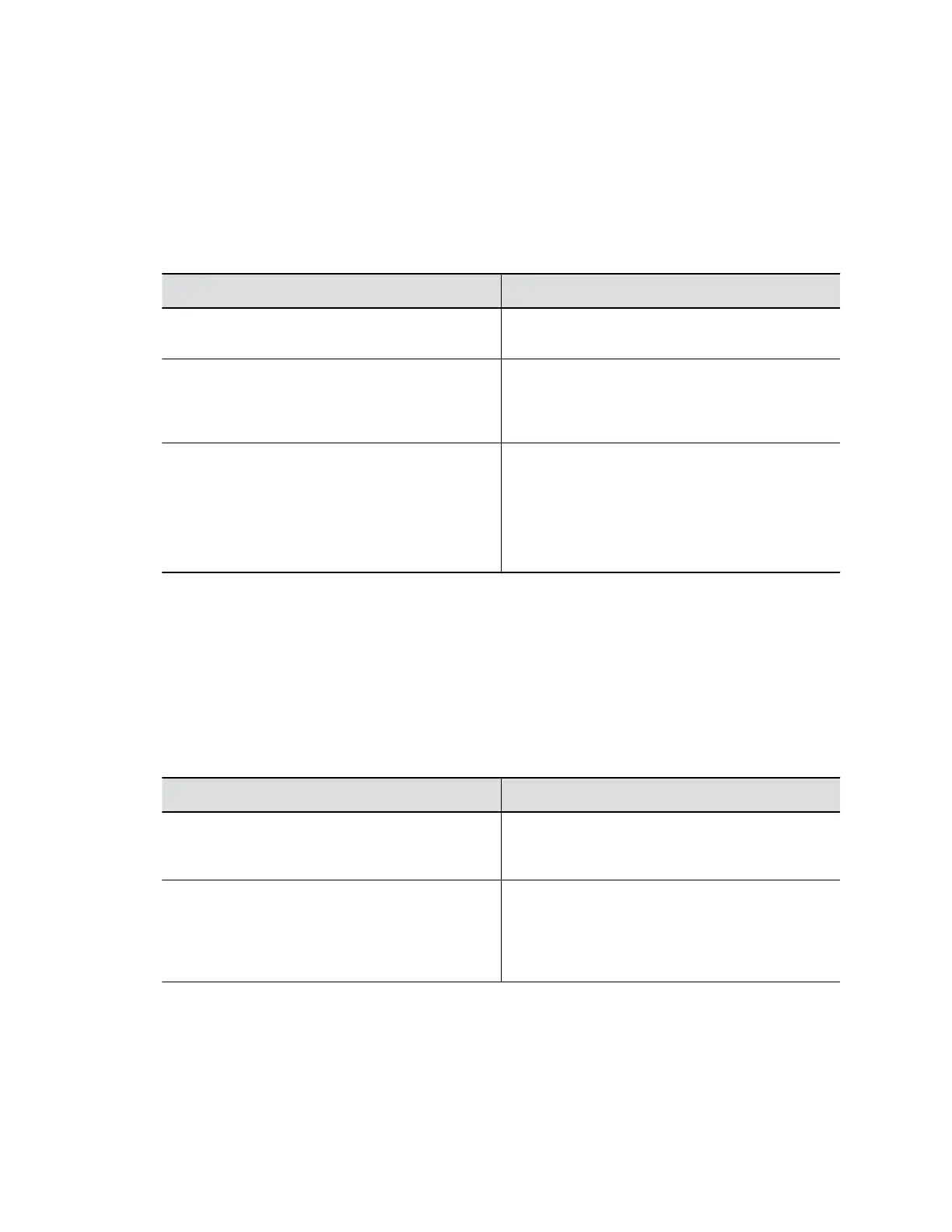
Setting Description
Lock Port after Failed Logins The number of failed login attempts allowed before
the web interface locks. You can set this to Off.
Port Lock Duration Specifies the amount of time that the web interface
remains locked due to failed login attempts. When
this period expires, the failed login attempts counter
resets and you can try to log in again.
Reset Port Lock Counter After Specifies the number of hours, starting with the first
failed login attempt, during which subsequent failed
login attempts are counted against the maximum
number allowed (Lock Port After Failed Logins).
The counter resets when the set period of time
expires or a user successfully logs in.
3. Select Save.
Configure the SSH Port Lock
You can limit the number of failed SSH login attempts to your G7500 system command-line API to protect
against brute-force attacks.
Procedure
1. In the system web interface, go to Security > Access.
2. Configure the following settings:
Setting Description
Lock SSH Port After Failed Logins Specifies the number of failed login attempts
allowed before the system locks SSH access to the
API.
SSH Port Lock Duration Specifies the amount of time that SSH access to
the API remains locked due to failed login attempts.
After this period expires, the system resets the
failed login attempts counter, and you can again try
to log in again.
Securing the System
Polycom, Inc. 47

 Loading...
Loading...











