Chapter 3
| Network Settings
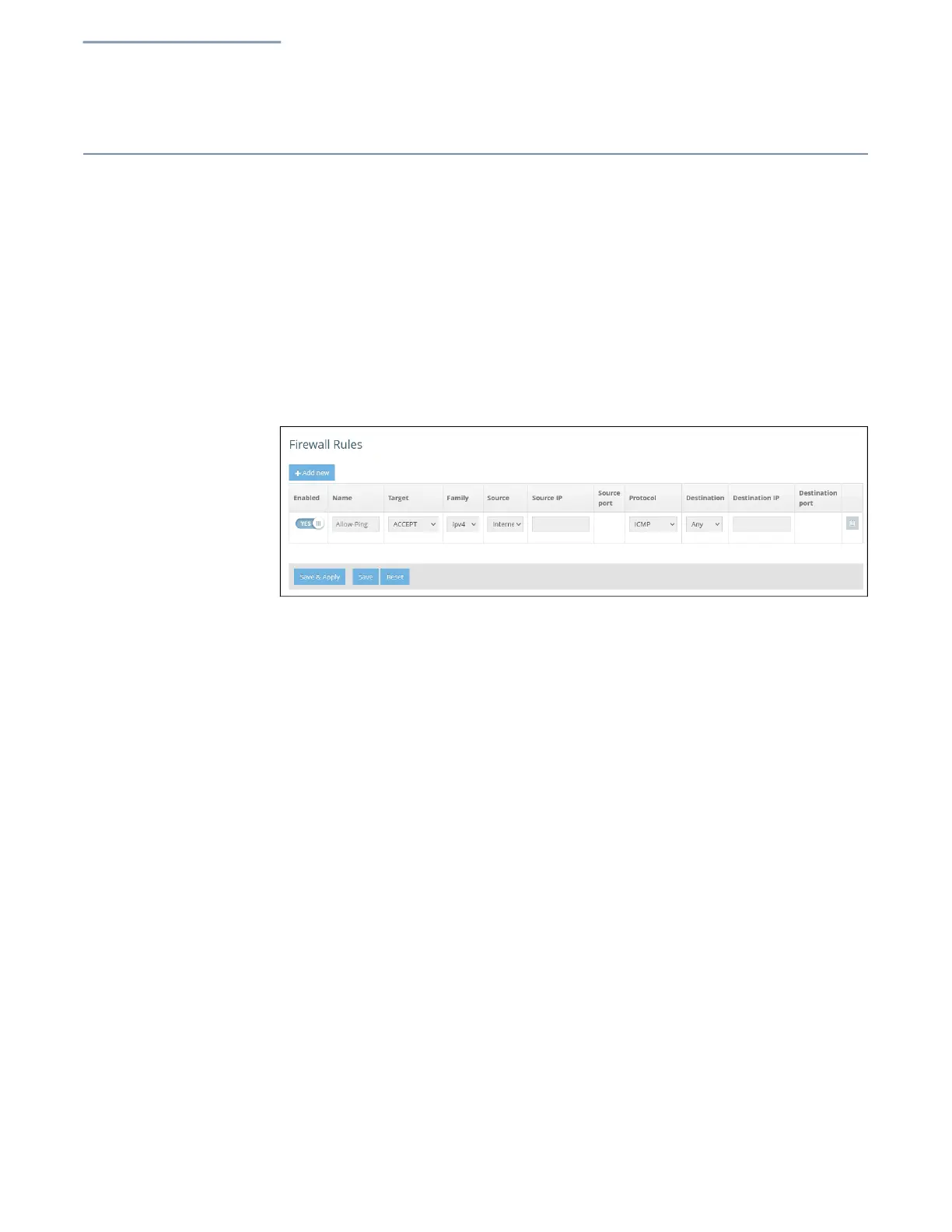
Firewall Rules
– 50 –
Firewall Rules
Firewall filtering restricts connection parameters to limit the risk of intrusion. The
firewall settings allow you to define a sequential list of rules that filter traffic based
on source and destination IP addresses and ports. Ingress packets are tested
against the filter rules one by one. As soon as a packet matches a rule, the
configured target action is implemented.
One rule, “Allow-Ping,” is pre-configured to allow Ping packets from the Internet.
You can enabl
e or disable this rule, but it cannot be modified or deleted. Click the
“
Add new” button to add a new firewall rule.
Figure 32: Firewall Rules
The following items are displayed on this page:
Enabled — Enables or disables the rule.
Name — A user-defined name for the filtering rule. (Range: 1-30 characters)
Target — The action to take when a packet is matched. (Options: Accept,
Reject, Drop; Default: Accept)
Accept — Accepts matching packets.
Reject — Drops matching packets and returns an error packet in response.
Drop — Drops matching packets.
Family — The IP address family. (Options: Any, IPv4; Default: Any)
Source — The source interface. (Options: Guest Network, Hotspot Network,
Default Local Network, Internet, Any)
Source IP — The source IPv4 address in CIDR notation. Includes an IPv4
address followed by a slash (/) and a decimal number to define the network
mask.
Source port — The source protocol port. (Range: 0-65535)
 Loading...
Loading...