Chapter 5
| System Settings
User Accounts
– 87 –
Use Default Certificate — Click to reset to use the AP’s default certificate.
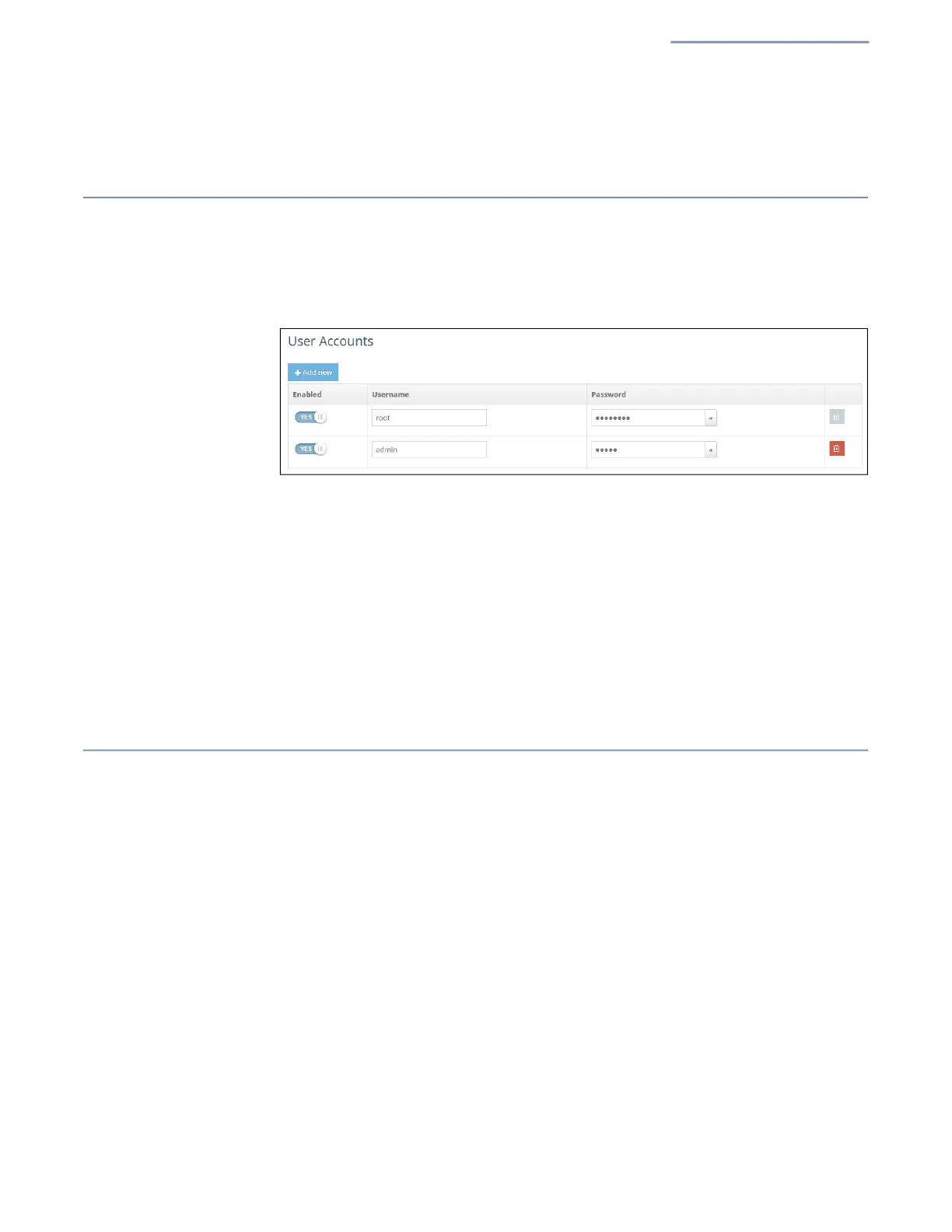
User Accounts
The User Accounts page allows you to control management access to the AP based
on manually configured user names and passwords.
Figure 58: User Accounts
The following items are displayed on this page:
Enabled — Click to enable or disable the user account.
Username — The name of the user. (Range: 1-32 ASCII characters. Only
accepts A-Z, a-z, 0-9, period “.”, underscore “_”, and hyphen “-”. Usernames
cannot begin with a hyphen “-” or period “.”.)
Password — The user password. (Range: 6-20 ASCII characters, case
sensitive, no special characters)
Services
The Services page allows you to control SSH management access to the AP,
configure NTP time servers, and configure iBeacon settings.
SSH The Secure Shell (SSH) can act as a secure replacement for Telnet. The SSH
protocol uses generated public keys to encrypt all data transfers passing between
the access point and SSH-enabled management station clients and ensures that
data traveling over the
network arrives unaltered. Clients can then securely use the
l
ocal user name and password for access authentication.
Note that SSH client software needs to be installed on the management station to
access the access point for management via the SSH protocol.
 Loading...
Loading...